Using Velociraptor to Detect and Hunt for Affected Systems: Unknown Malware Analysis
1.0 Introduction

1.1 What is Threat Hunting ?
Threat hunting is the proactive, iterative process of identifying and disrupting threats within an organization’s environment. Mirza [2] also define threat hunting as proactive, manual, or machine-assisted process of actively seeking out security incidents and anomalies that may have evaded detection by automated security systems. It involves a deeper investigation into data, behavior patterns, and system activities to identify potential threats before they can cause harm [1]. Many researchers [1] [6] [7] [8] have already explained different types of threat hunting techniques as explained in this table 1.
| Type of Threat Hunting | Description | Approach | Techniques |
|---|---|---|---|
| Reactive Threat Hunting | Performed in response to specific indicators, alerts, or intelligence. | Focus on investigating known threats or alerts. | Log analysis, IOC (Indicators of Compromise) searches, network traffic analysis [1]. |
| Proactive Threat Hunting | Initiated without specific triggers, looking for unknown threats. | Search for undetected threats before alerts are triggered. | Behavioral analysis, anomaly detection, network and endpoint monitoring, machine learning models [7] [8]. |
| Hypothesis-Driven Threat Hunting | Starts with a hypothesis about potential threats based on known attack methods. | Create hypotheses and search for signs of those specific attack methods. | Creating hypotheses based on attack techniques (e.g., MITRE ATT&CK), searching relevant logs or endpoints [6]. |
| Unknown (Blind) Threat Hunting | Hunt without a specific threat in mind, aiming to uncover unknown threats. | Explore data for hidden or unusual patterns that may indicate a compromise. | Advanced analytics, anomaly detection, machine learning, pattern recognition to identify potential unknown threats [9]. |
| IOC-Based Threat Hunting | Searches for known Indicators of Compromise (IOCs) related to threats. | Look for specific IOCs (e.g., IP addresses, file hashes) associated with known threats. | Searching for IOCs in logs, network traffic, files, and endpoint data [8]. |
| Behavioral Threat Hunting | Focuses on suspicious behavior patterns rather than IOCs. | Search for abnormal behaviors or deviations from normal user/system activity. | Baseline behavior analysis, anomaly detection, machine learning, statistical analysis to detect abnormal activity patterns [6] [7]. |
Proactive Threat Hunting is driven by a broader awareness of potential risks. In this approach, hunters actively search for threats before they manifest as incidents or trigger alerts. This type of hunting involves analyzing system behavior, network traffic, and endpoint activity to identify early signs of compromise, using techniques such as behavioral analysis, anomaly detection, and network monitoring.
Proactive threat hunting involves security teams actively searching an organization’s IT environment for signs of infiltration, assuming that threat actors may have already breached the perimeter or gained access through a vulnerability or misconfiguration [3] [6].
This approach is both a shift in mindset and a practical methodology. By anticipating potential threats before they manifest, hunting teams can identify issues early, preventing crises, and implement hardening techniques to reduce risk [3].
1.2 Case Scenarios.
In this scenario, we are tasked with investigating a potential security incident on a Windows 10 Pro system associated with the user daniyyell-client@DESKTOP-U9HDOEJ. The objective is to conduct proactive threat hunting to determine whether the system has been compromised. Since the system’s integrity is uncertain, we will leverage Velociraptor to perform the hunt, collecting comprehensive logs and artifacts for in-depth analysis. This approach will allow us to uncover any signs of compromise or suspicious activities and ensure the system’s security posture is thoroughly assessed.
In this article, we assume that the Velocirator agent is already installed on the Windows system. Our focus will be on collecting logs and artifacts. For detailed instructions on how to install the Velocirator agent, please refer to this article [4].
2.0 Velocirator Selected Artifacts
While many of these artifacts may not be directly useful, they are selected because we are hunting for every potential Indicator of Compromise (IoC) or Indicator of Attack (IoA). If some artifact queries do not return any data, it is understandable. However, we will focus on the other relevant artifact results [4]. Here are a few artifacts that we have selected for this article:
| Artifact Name | Usage |
|---|---|
| Windows.System.DNSCache | Collects DNS cache entries to identify suspicious or malicious domains used for C2 communication. |
| Windows.Analysis.EvidenceOfExecution | Identifies evidence of process execution, useful for detecting malicious payload execution. |
| Windows.Analysis.EvidenceOfDownload | Tracks downloaded files, which could include potentially malicious payloads. |
| Windows.Sysinternals.Autoruns | Lists autostart locations for persistence mechanisms, often used by malware. |
| Windows.EventLogs.ScheduledTasks | Analyzes scheduled tasks to identify persistence or malicious task execution. |
| Windows.Registry.RDP | Detects changes to RDP-related registry keys, which could indicate remote access activity. |
| Windows.System.Pslist | Captures a list of running processes to identify suspicious ones. |
| Windows.System.UntrustedBinaries | Detects binaries that are not signed or have unknown origins, potentially linked to malware. |
| Windows.Network.NetstatEnriched | Provides detailed network connection data to identify unusual TCP connections. |
| Windows.Attack.ParentProcess | Tracks parent-child process relationships to identify suspicious process spawning. |
| Windows.Attack.UnexpectedImagePath | Detects binaries executed from unexpected or non-standard locations. |
| Windows.Detection.BinaryHunter | Searches for potentially malicious binaries present on the system. |
| Windows.Detection.BinaryRename | Identifies renamed binaries, often a tactic used by malware for evasion. |
| Windows.Detection.Impersonation | Detects impersonation attempts, such as stolen or misused credentials. |
| Windows.Detection.Mutants | Identifies malicious mutex objects, often used for synchronization in malware. |
| Windows.EventLogs.EvtxHunter | Analyzes EVTX logs for suspicious events and anomalies. |
| Windows.EventLogs.Evtx | Collects raw event logs for detailed manual or automated analysis. |
| Windows.Memory.PEDump | Dumps in-memory PE files for analysis, useful for identifying injected components. |
The next step is to download the logs from the selected artifacts and move them to a secure location for analysis. Since some of the hunt packages may not yield any results, we will focus only on those that do produce results to maximize efficiency and time. At this stage, we are uncertain about what we will find, and if no significant findings emerge, that is acceptable, as we are equipped to thoroughly analyze the logs regardless.
2.1 Windows.Analysis.EvidenceOfDownload
This artifact is designed to detect evidence of user download activity as shown in Fig 1. It works by searching for the Zone.Identifier alternate data stream, which is created alongside files downloaded from the internet or an intranet. The Zone.Identifier stream is generated by applications when a user saves a file from a different security zone to the local file system.
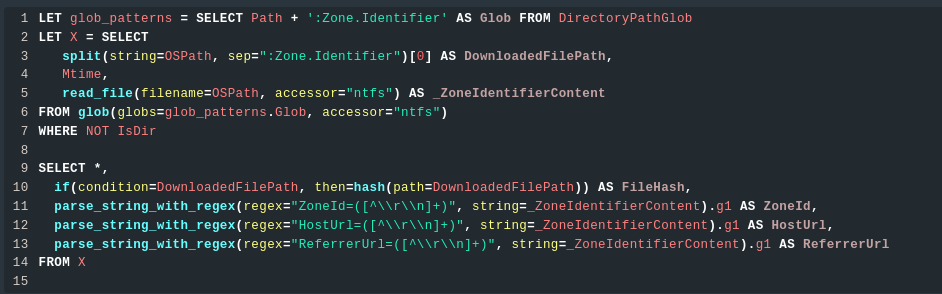
Fig 1: Windows.Analysis.EvidenceOfDownload
The artifact searches the specified directory for any file with an alternate data stream named Zone.Identifier, then identifies files with a zoneId of 3 (Internet) or 4 (Intranet). It also calculates the hash value of the file and extracts the content of the Zone.Identifier stream, which can sometimes contain valuable information. The artifact returns a list of files with their hashes, paths, and Zone.Identifier stream content.
2.2.1 Results
Upon reviewing the logs, there is no indication of any malicious files being downloaded to the victim’s system as shown in Fig 2. The downloaded files include:
ProcessExplorer.zipclient.config.yamlfakenet3.3.zipvelociraptor.exe
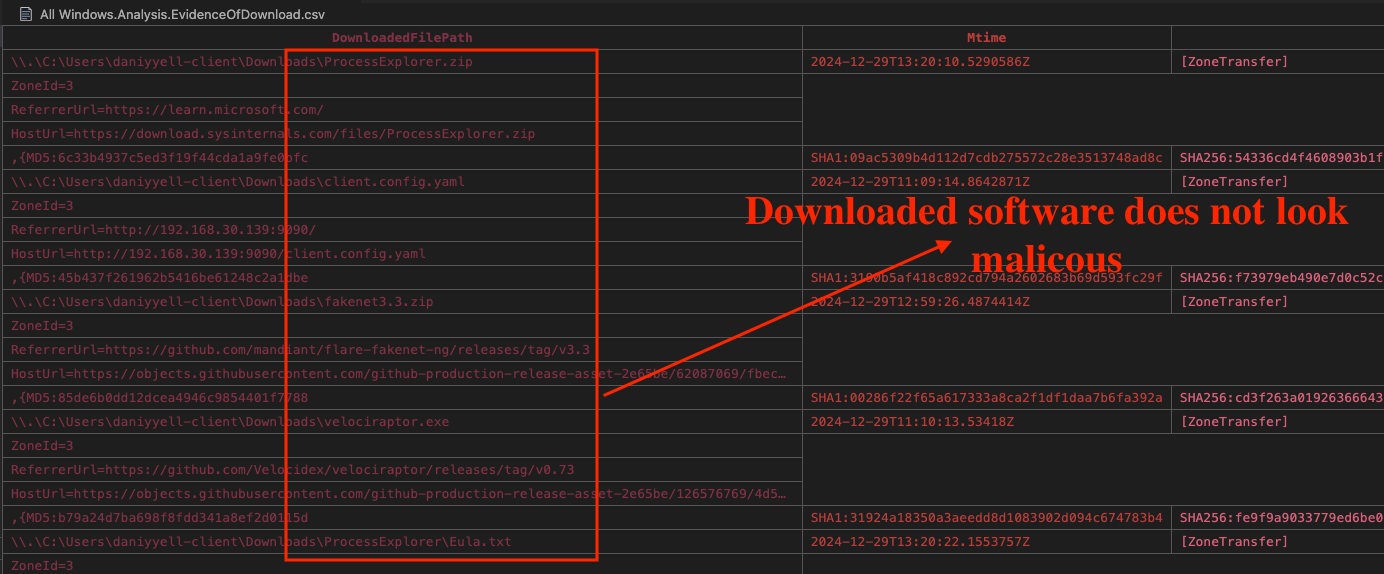
Fig 2: Windows.Analysis.EvidenceOfDownload
As shown in Fig. 2, all MD5 hashes for these files are legitimate. Therefore, we will proceed to the next artifact for further analysis.
2.2 Windows.Analysis.EvidenceOfExecution/Amcache
In many investigations, it is crucial to find evidence of program execution. This artifact combines the findings from several collectors into a comprehensive overview of all program execution artifacts.
This artifact combines the following sources:
- UserAssist
SELECT * FROM Artifact.Windows.Registry.UserAssist() - Amcache
SELECT * FROM Artifact.Windows.Detection.Amcache() - Timeline
SELECT * FROM Artifact.Windows.Forensics.Timeline() - ShimCache
SELECT * FROM Artifact.Windows.Registry.AppCompatCache() - Prefetch
SELECT * FROM Artifact.Windows.Forensics.Prefetch() - Recent Apps
SELECT * FROM Artifact.Windows.Forensics.RecentApps()
2.2.1 Results Analysis
Based on Figure 3, the files and their respective locations appear suspicious. The client.exe file is located in the AppData folder, which is not uncommon for legitimate software, but in this case, it is paired with a publisher identified as Google LLC as shown in Fig 3. The use of legitimate-looking names and locations, such as Google Chrome being present in unconventional directories, raises concerns of possible suspicious activity or spoofing.
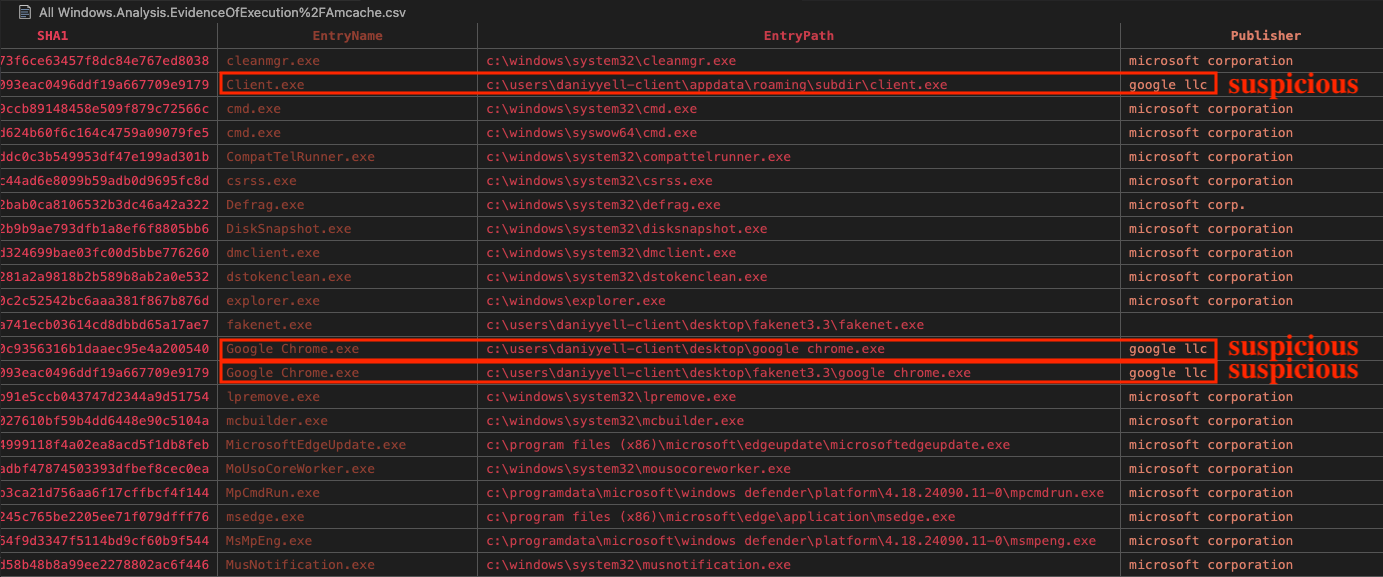
Fig 3: Windows.Analysis.EvidenceOfExecution
We will document these suspicious instances, as they might be indicators of compromise (IoCs) or tactics such as file masquerading.
2.2.2 IoCs
- Client.exe
- Path:
C:\Users\Daniyyell-Client\AppData\Roaming\Subdir\client.exe - Publisher: Google LLC
- Path:
- Google Chrome.exe
- Path:
C:\Users\Daniyyell-Client\Desktop\Google Chrome.exe - Publisher: Google LLC
- Path:
- Google Chrome.exe
- Path:
C:\Users\Daniyyell-Client\Desktop\Fakenet3.3\Google Chrome.exe - Publisher: Google LLC
- Path:
Now that we’ve identified these items as suspicious, we will keep them in mind as we continue analysing the remaining hunting package logs. In the meantime, we will remain vigilant for anything else that stands out and will correlate the results later.
2.3 Windows.Detection.BinaryHunter
Windows.Detection.BinaryHunter is a client artifact developed by Matt Green (@mgreen27) that provides powerful capabilities for hunting binary file attributes. It accepts a glob pattern as input to target specific files and examines each file within scope for the presence of an MZ header as shown in Fig 4. The artifact also retrieves Authenticode metadata and parses Portable Executable (PE) attributes for analysis.
Using regular expressions and whitelists, the output of both PE and Authenticode queries can be filtered to identify relevant strings. This enables the detection of specific elements such as PE imports, exports, or other attributes.
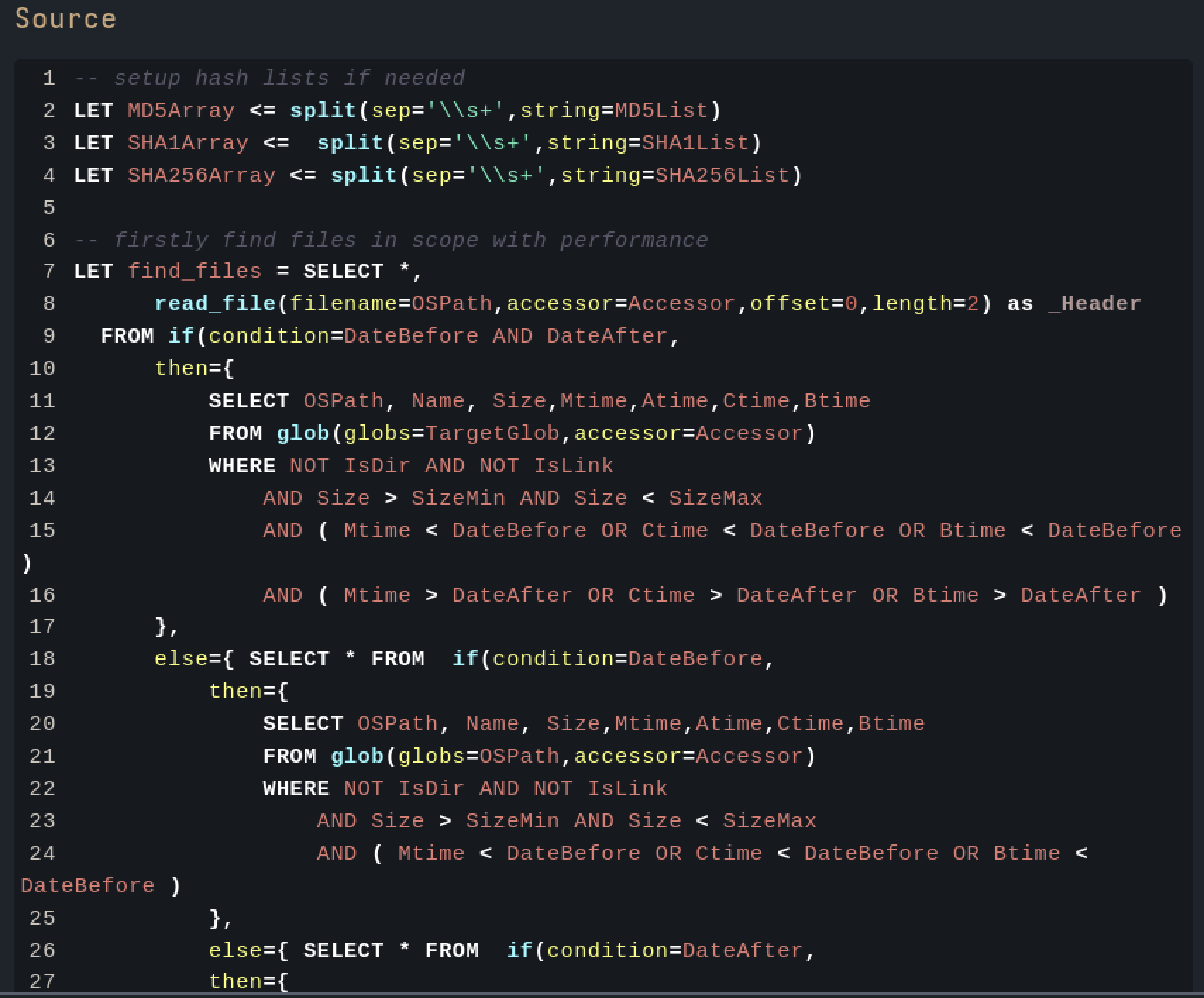
Fig 4: Windows.Detection.BinaryHunter
Filters in this artifact are cumulative; for example, if a file is excluded by one filter, it will not produce results even if it matches other filters, such as a hash-based filter. To optimise performance, it is recommended to use path, size, and date filters. By default, the artifact uses the “auto” data accessor, although this can be modified as needed.
2.3.1 Results and Analysis
Detailed Binary Analysis: Google Chrome.exe
Overview of File Attributes
The binary analysed, Google Chrome.exe, is located at C:\Users\daniyyell-client\AppData\Roaming\SubDir, a directory often exploited by malware for persistence. Its size is 3,333,632 bytes, and the timestamps suggest recent creation, with the birth time recorded as 2024-12-29T13:51:19Z.
| Attribute | Value |
|---|---|
| File Name | Google Chrome.exe |
| File Path | C:\Users\daniyyell-client\AppData\Roaming\SubDir |
| Size | 3,333,632 bytes |
| Last Modified | 2024-12-29T13:36:06Z |
| Last Accessed | 2024-12-29T15:47:56Z |
| Created | 2024-12-29T13:36:06Z |
| Birth Time | 2024-12-29T13:51:19Z |
Authenticode Analysis
The file lacks any Authenticode metadata, such as a valid publisher or timestamp, and its trust status is marked as “Unknown” as shown in Fig 5. This absence of digital signing is unusual for legitimate software distributed by reputable companies like Google. The mismatch between computed hash values and the Authenticode hash further indicates possible tampering.
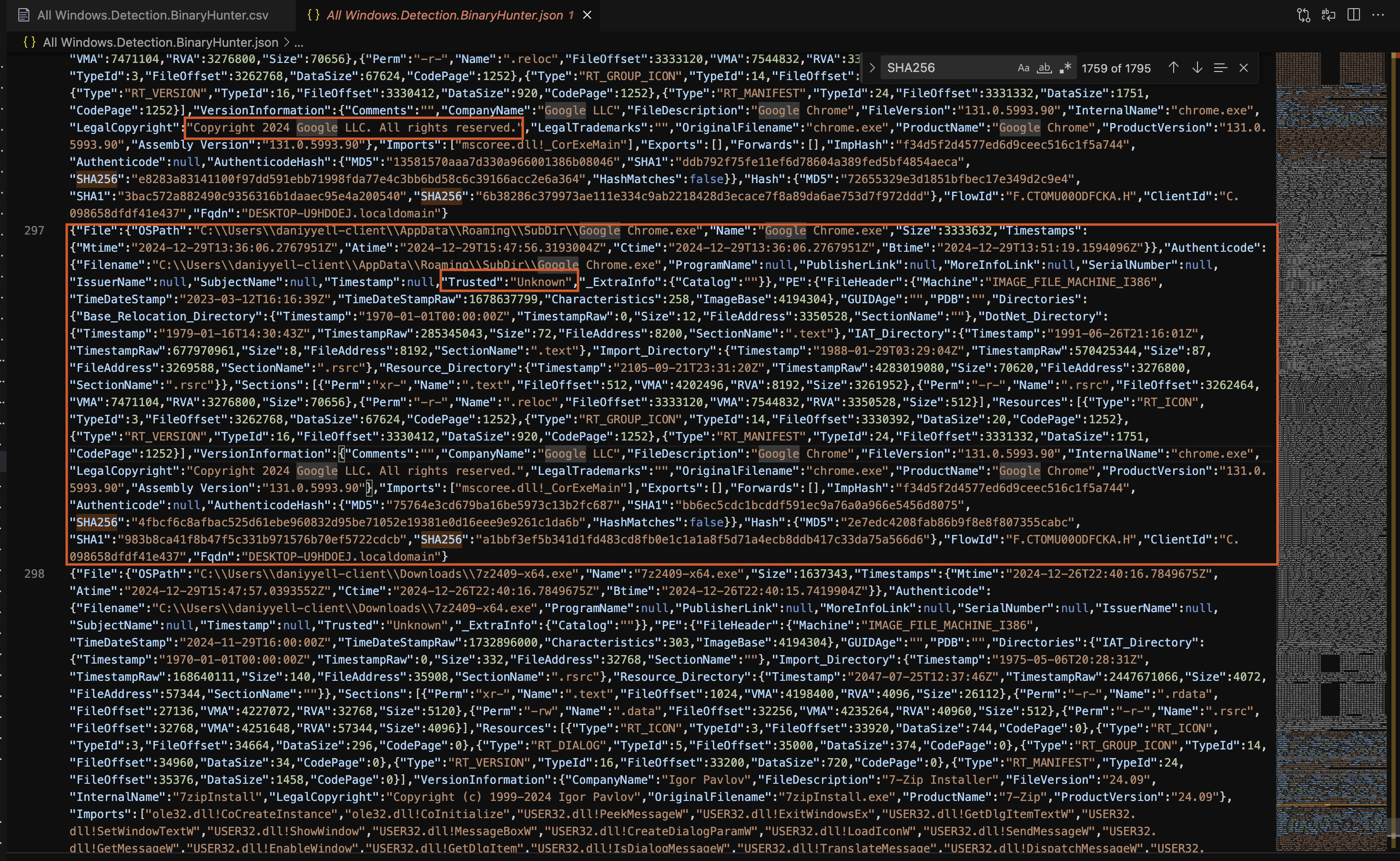
Fig 5: Windows.Detection.BinaryHunter
Authenticode Summary
| Field | Value |
|---|---|
| Trusted | Unknown |
| Publisher | Not available |
| Timestamp | Not available |
| Certificate Serial | Not available |
Section Details
The binary contains three sections, each with distinct characteristics. The .text section is executable and occupies the largest portion of the file, while .rsrc and .reloc are read-only sections.
| Section Name | Permissions | Size | Virtual Address | File Offset |
|---|---|---|---|---|
| .text | Executable, Readable (xr-) |
3,261,952 bytes | 0x402000 | 512 bytes |
| .rsrc | Readable (-r-) |
70,656 bytes | 0x722000 | 3,262,464 bytes |
| .reloc | Readable (-r-) |
512 bytes | 0x730000 | 3,333,120 bytes |
Resource Directory
The file includes embedded resources such as icons and version metadata. Notably, the RT_ICON resource is significantly large, which could indicate attempts to mimic legitimate branding or obscure malicious content.
| Resource Type | File Offset | Data Size |
|---|---|---|
| RT_ICON | 3,262,768 bytes | 67,624 bytes |
| RT_GROUP_ICON | 3,330,392 bytes | 20 bytes |
| RT_VERSION | 3,330,412 bytes | 920 bytes |
| RT_MANIFEST | 3,331,332 bytes | 1,751 bytes |
Version Information
The binary’s metadata claims to belong to Google LLC, with the product name “Google Chrome” and version 131.0.5993.90. However, version information is easily spoofed and must be corroborated with additional verification.
Metadata Overview
| Field | Value |
|---|---|
| Company Name | Google LLC |
| File Description | Google Chrome |
| File Version | 131.0.5993.90 |
| Product Version | 131.0.5993.90 |
| Original Filename | chrome.exe |
| Legal Copyright | Copyright 2024 Google LLC. All rights reserved. |
Import Analysis
The binary imports a single DLL, mscoree.dll, and references _CorExeMain, indicating it is a .NET application. Managed .NET files often involve obfuscation techniques, making static analysis challenging and necessitating dynamic testing.
Hash Analysis
The computed hash values differ from the Authenticode hash, raising concerns about potential tampering. Hash mismatches are a strong indicator of modification or malicious intent.
| Algorithm | Hash Value |
|---|---|
| MD5 | 2e7edc4208fab86b9f8e8f807355cabc |
| SHA1 | 983b8ca41f8b47f5c331b971576b70ef5722cdcb |
| SHA256 | a1bbf3ef5b341d1fd483cd8fb0e1c1a1a8f5d71a4ecb8ddb417c33da75a566d6 |
Analysis and Findings
The binary exhibits several red flags:
- Suspicious File Path: The location is a common hiding spot for malware.
- Unsigned Binary: The absence of a digital signature is unusual for Google software.
- Hash Mismatch: This indicates the binary may have been tampered with.
- Large Resources: Abnormally large icon files may be used for deceptive purposes.
2.3.2 Conclusion
Following the detailed analysis of the binary Google Chrome.exe, the next steps will involve reviewing additional Velociraptor artifacts to gather a broader context regarding the system’s state and potential indicators of compromise (IOCs). Once this data is collected, the hashes and other extracted IOCs will be thoroughly analysed against threat intelligence sources to confirm any malicious activity and identify its scope. This combined approach ensures a comprehensive understanding of the binary’s role within the system and its potential impact.
2.4 Windows.EventLogs.Evtx
The Windows.EventLogs.Evtx artifact, developed by Chris Hendricks (chris@counteractive.net), is a powerful tool for extracting and analysing events from Windows event logs (evtx files) as depicted in Fig 6. Each event is returned in full detail, but the results can be refined using a range of filters to focus on specific files, timeframes, paths, channels, or event IDs.
This artifact allows users to target specific event logs through glob patterns while also narrowing results by defining start and end timestamps. Regular expressions can be applied to match file paths, event channels, or event IDs, enabling precise and efficient searches. The parsed data is suitable for further processing, such as bulk exports to Elasticsearch or in-depth analysis using Velociraptor Query Language (VQL). It also serves as a foundation for creating custom artifacts with enhanced filtering capabilities.
Fig 6: Windows.EventLogs.Evtx
Performance optimisation is crucial when using this artifact, as it can be resource-intensive. Parsing large logs or processing Volume Shadow Copies (VSS) may demand significant CPU and memory resources. To mitigate this, users are encouraged to reduce operations per second, refine glob patterns, or apply stricter regex filters. In scenarios involving extensive logs or high-volume third-party sources like Sysmon, extending default timeouts may also be necessary.
The artifact often produces a substantial volume of results, sometimes exceeding hundreds of thousands of rows per host. Filtering outputs using regex for paths, channels, or event IDs is recommended to maintain manageable datasets. Despite these challenges, the artifact’s capability to parse, aggregate, and analyse events makes it a valuable tool for incident response and forensic investigations.
This artifact is inspired by others within the Windows.EventLogs* family, with notable contributions from Matt Green (@mgreen27).
2.4.1 Results and analysis
Overview of the Event
The Windows.EventLogs.Evtx artifact reveals significant results from a detection event triggered by Microsoft Defender Antivirus as shown in Fig 7. The event details are from the Windows Defender Operational channel and pertain to a security action taken against a potential threat on the system.
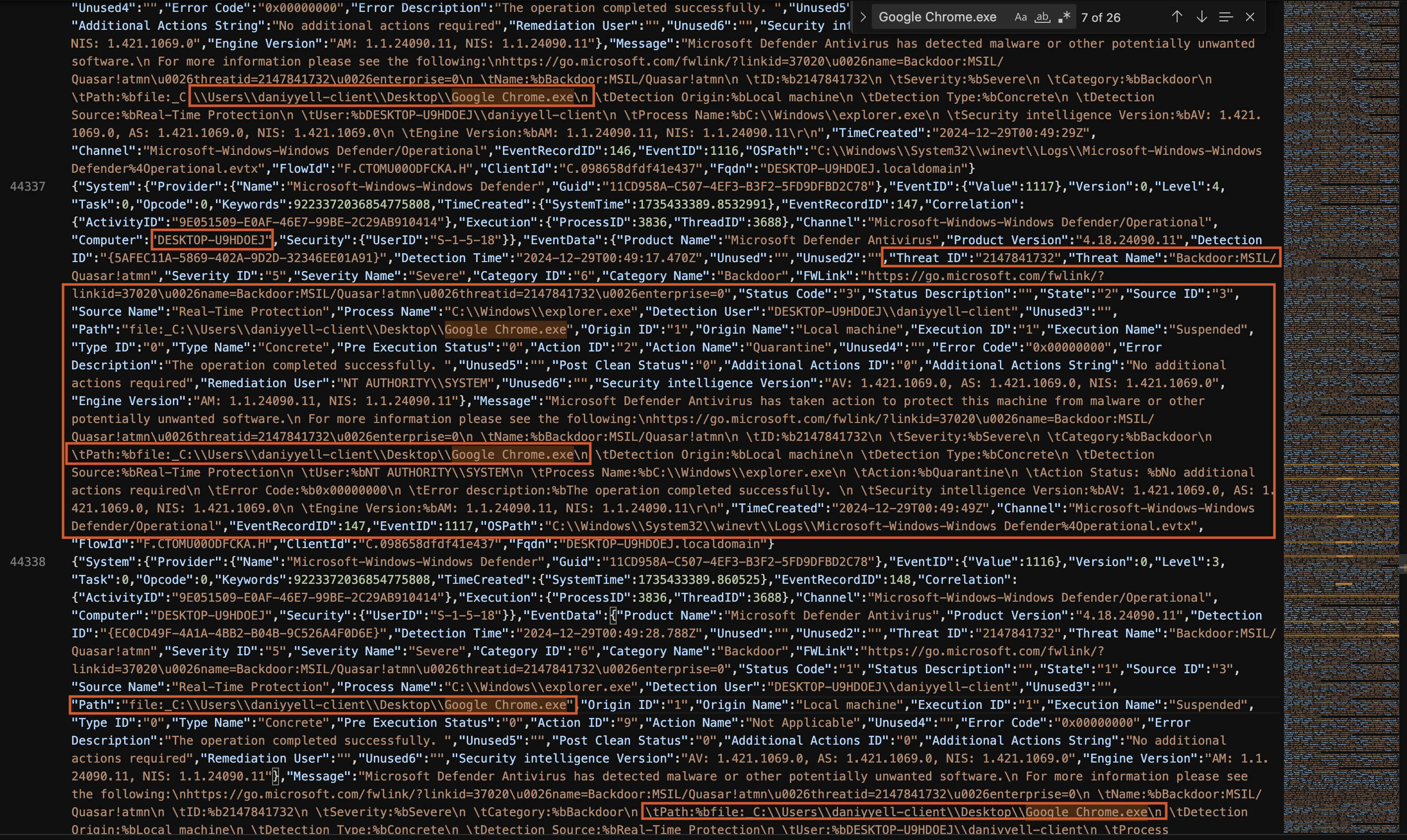
Fig 7: Windows.EventLogs.Evtx
Event Information
The key information in the event is summarised below:
| Field | Value |
|---|---|
| Provider Name | Microsoft-Windows-Windows Defender |
| Event ID | 1117 |
| Severity | Severe |
| Threat Name | Backdoor:MSIL/Quasar!atmn |
| Detection Time | 2024-12-29T00:49:17.470Z |
| Threat ID | 2147841732 |
| Threat Category | Backdoor |
| Path to Infected File | C:\Users\daniyyell-client\Desktop\Google Chrome.exe |
| Action Taken | Quarantine |
| Source | Real-Time Protection |
| Process Involved | C:\Windows\explorer.exe |
| User Involved | DESKTOP-U9HDOEJ\daniyyell-client |
| Security Intelligence Version | AV: 1.421.1069.0, AS: 1.421.1069.0, NIS: 1.421.1069.0 |
| Engine Version | AM: 1.1.24090.11, NIS: 1.1.24090.11 |
Event Breakdown
The event, logged with EventID 1117, indicates that Microsoft Defender Antivirus detected a Backdoor:MSIL/Quasar!atmn malware in the system. This particular threat, identified with the threat ID 2147841732, was classified as a Severe severity, categorized as a Backdoor. The infection was detected at 2024-12-29T00:49:17.470Z, and the Google Chrome.exe file, located on the desktop of the user daniyyell-client, was flagged as suspicious.
The action taken by Defender was to quarantine the file, and no additional actions were required. The detection originated from the local machine, specifically from Real-Time Protection. The event also reveals that the process associated with the infection was C:\Windows\explorer.exe, and the user involved was the system user NT AUTHORITY\SYSTEM.
Message Description
The message from the event log confirms that Microsoft Defender Antivirus successfully quarantined the Google Chrome.exe file after detecting the Backdoor:MSIL/Quasar!atmn threat. It also provides further details, including the detection source and the engine versions used at the time of detection. The operation was completed successfully, as indicated by the error code 0x00000000.
2.4.2 Conclusion and Summary of Windows.EventLogs.Evtx
The Windows.EventLogs.Evtx artifact provides detailed information regarding a detection event triggered by Microsoft Defender Antivirus. This event pertains to the detection of a Backdoor:MSIL/Quasar!atmn threat, which was flagged as severe. The detection took place on 2024-12-29 and was associated with the file Google Chrome.exe located on the user’s desktop.
The event was logged in the Microsoft-Windows-Windows Defender Operational channel, specifically with Event ID 1117. It shows that Microsoft Defender took the action of quarantining the infected file to mitigate potential harm. The Google Chrome.exe file was identified as a potential backdoor malware, and its process was associated with explorer.exe. This indicates that the malware may have been launched through the system’s file explorer.
The analysis of this log entry reveals how the antivirus system reacted to a detected threat and took the necessary action to protect the system. The severity of the threat, its classification as a backdoor, and the successful quarantine action highlight the efficiency of Microsoft Defender in responding to malware threats.
2.5 Windows.Sysinternals.Autoruns
The Velociraptor artifact Windows.Sysinternals.Autoruns is designed to analyse autostart entries within a Windows system. These entries represent various points where applications or DLLs are configured to launch automatically, often serving as persistence mechanisms. The artifact begins by defining a list of flags and options. Flags correspond to specific categories of autostart entries, such as “Boot execute” or “Appinit DLLs,” while options include additional features like verifying digital signatures.
The artifact processes these definitions to determine the user-selected flags and options. It then identifies the system architecture, such as x86 or x64, to ensure the correct Autoruns binary is retrieved using the Artifact.Generic.Utils.FetchBinary function. Once the appropriate binary is fetched, it is executed with a range of arguments. These include suppressing banners, automatically accepting the End User License Agreement, and specifying the types and categories of autostart entries to analyse. The command also enables hash calculations for files and processes entries across all user profiles.
The output from the executed command is retrieved and parsed into rows. It is processed as CSV data, allowing for structured interpretation and further filtering. This approach ensures that analysts receive detailed information about autostart entries, including file hashes and digital signature validation results.
The artifact supports extensive customisation, enabling analysts to focus on specific autostart categories or apply validation checks. Its ability to process multiple user profiles and generate hash data makes it particularly valuable for detecting persistence mechanisms, unauthorised modifications, or malicious startup behaviour within the system. By combining flexibility and detailed output, this artifact serves as a critical tool for investigating potential threats effectively.
2.5.1 Autostart Entry Analysis
The artifact allows for the detailed examination of autostart entries across various system locations, including:
- Task Scheduler
- Registry Run Keys
- Startup Folders
- Service Entries
- Browser Add-ons
By providing a comprehensive list of all programs configured to start automatically, it enables analysts to detect abnormal or unauthorized entries, which can be indicative of a compromise. This feature is crucial for identifying both legitimate software and malicious entities using persistence techniques.
2.5.2 Persistence Detection
Persistence is a common tactic used by attackers to maintain access to compromised systems. This artifact plays a critical role in detecting such mechanisms by identifying:
- Malicious scheduled tasks, especially those using disguised or misleading names.
- Unusual entries pointing to executables in unexpected locations, such as the
AppDataorTempdirectories as shown in Fig 8, which are commonly abused by malware. - Abnormal registry modifications and manipulated autostart configurations that could signal unauthorized access or a foothold on the system.
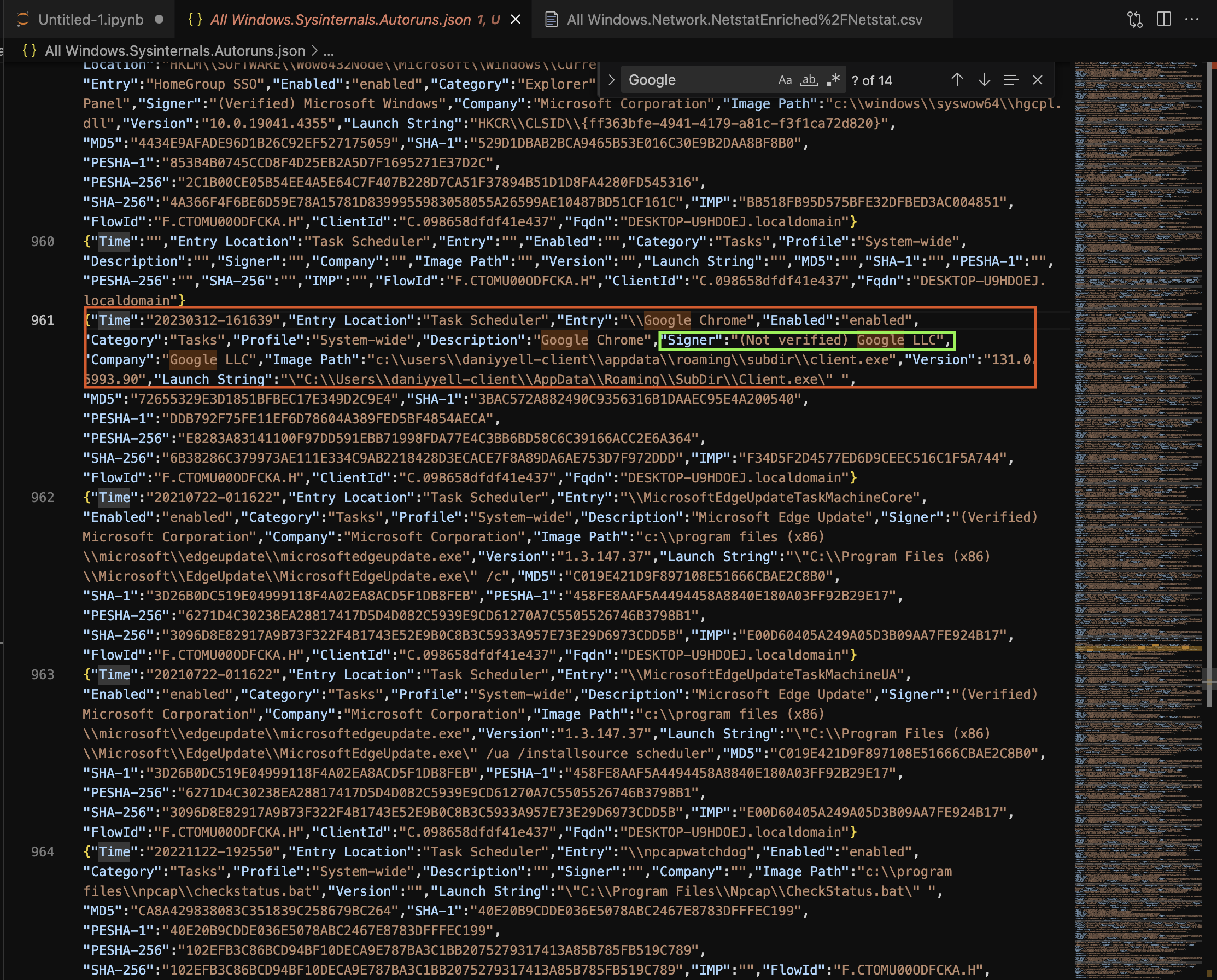
Fig 8: Windows.EventLogs.Evtx
By exposing these autostart mechanisms, Autoruns helps analysts uncover how attackers have maintained persistent access, allowing them to take appropriate containment and remediation actions.
2.5.3 Digital Signature Validation
The artifact verifies the digital signatures of autostart entries, helping analysts differentiate between trusted, legitimate software and potentially malicious binaries. It does this by:
- Identifying unsigned or improperly signed binaries, which are often a hallmark of malware.
- Checking the validity of the signature to ensure that the file has not been tampered with or altered by malicious actors.
This validation step is vital for assessing the integrity of files and ensuring that only verified software is running on the system. Any unsigned or suspiciously signed software can be flagged for further investigation.
2.5.4 Hashing for Threat Intelligence
Autoruns generates cryptographic hashes (MD5, SHA-1, SHA-256) for all detected binaries. This functionality enables analysts to:
- Compare the generated hashes against known malware databases (such as VirusTotal or MISP) to identify potentially malicious files.
- Track file modifications, detect new malware variants, or identify malware spreading across multiple endpoints.
- Correlate the data with other threat intelligence sources to understand the scope of an attack or identify patterns in the malware’s behavior.
2.5.5 Granular Filtering and Scoping
The artifact provides the ability to scope the search based on system-wide or user-specific autostart entries. This flexibility allows analysts to:
- Focus on specific users or applications when investigating targeted attacks or insider threats.
- Identify whether certain malicious activities are being initiated by specific users or system-wide processes, streamlining the investigation process.
2.5.6 Results and Analysis
The extracted results provide a detailed breakdown of a suspicious entry discovered in the Task Scheduler. This entry appears to be masquerading as a legitimate Google Chrome process but has several indicators of potential compromise. The following table summarises the key findings:
| Attribute | Value | Explanation |
|---|---|---|
| Time | 2023-03-12 16:16:39 | The timestamp when the entry was recorded. This can be correlated with other logs for further analysis. |
| Entry Location | Task Scheduler | The autostart mechanism being used. Task Scheduler is often exploited for persistence by attackers. |
| Entry | \Google Chrome | The name of the scheduled task. It mimics a legitimate Google Chrome process, which may mislead analysts or users. |
| Enabled | Enabled | Confirms that the task is active and will execute as configured. |
| Category | Tasks | Indicates that this is a task-based autostart entry. |
| Profile | System-wide | Affects all users on the system, increasing the risk and scope of impact. |
| Description | Google Chrome | The task description further adds to the deception by using a legitimate application name. |
| Signer | (Not verified) Google LLC | Indicates the signature is not verified, raising suspicion about the authenticity of the file. |
| Company | Google LLC | Claimed company name. Attackers may falsify this information to appear trustworthy. |
| Image Path | c:\users\daniyyell-client\appdata\roaming\subdir\client.exe |
The executable’s location in the user’s AppData directory is unusual for a legitimate Google Chrome binary. |
| Version | 131.0.5993.90 | Version string used to mimic the appearance of a legitimate application. |
| Launch String | "C:\Users\daniyyell-client\AppData\Roaming\SubDir\Client.exe" |
Specifies the full command executed by the scheduled task. |
| MD5 | 72655329E3D1851BFBEC17E349D2C9E4 | The MD5 hash of the executable file. This can be used to check against known malicious or benign file databases. |
| SHA-1 | 3BAC572A882490C9356316B1DAAEC95E4A200540 | The SHA-1 hash provides an additional layer of file integrity verification. |
| PESHA-1 | DDB792F75FE11EF6D78604A389FED5BF4854AECA | A SHA-1 hash of the Portable Executable (PE) file structure, offering insights into file modifications. |
| PESHA-256 | E8283A83141100F97DD591EBB71998FDA77E4C3BB6BD58C6C39166ACC2E6A364 | A more robust hash of the PE structure for deeper analysis. |
| SHA-256 | 6B38286C379973AE111E334C9AB2218428D3ECACE7F8A89DA6AE753D7F972DDD | The SHA-256 hash is used to verify the file’s integrity and compare it with known threat intelligence feeds. |
| IMP | F34D5F2D4577ED6D9CEEC516C1F5A744 | The Import Hash (IMP) value reveals similarities in imported libraries between this file and others, aiding in clustering malicious binaries. |
| FlowId | F.CTOMU00ODFCKA.H | Identifies the execution flow for tracking purposes. |
| ClientId | C.098658dfdf41e437 | Identifies the machine on which the task was discovered. |
| Fqdn | DESKTOP-U9HDOEJ.localdomain | The fully qualified domain name (FQDN) of the affected system. |
2.5.7 Thorough Analysis
-
Suspicious File Path and Name
The file is located in theAppData\Roamingdirectory, which is often used by malware due to its accessibility and lack of frequent monitoring. The nameClient.exeis generic and provides no clear indication of its purpose. -
Unverified Digital Signature
Although the file claims to be signed by “Google LLC,” the lack of verification indicates potential tampering or forgery, a common technique used by attackers to disguise malicious binaries as legitimate ones. -
Hash Values and Integrity
The provided MD5, SHA-1, and SHA-256 hashes do not correspond to any known legitimate Google Chrome executables. These hashes can be cross-checked against threat intelligence databases like VirusTotal for further validation. -
Task Scheduler Exploitation
The use of Task Scheduler for persistence is concerning. This method ensures the malicious file executes at regular intervals or system startup, maintaining the attacker’s foothold on the system. -
Deceptive Attributes
The version number, company name, and description are crafted to mimic a legitimate Google Chrome task. This social engineering tactic aims to mislead both end-users and system administrators. -
Potential Threat
Given the above indicators, this scheduled task is likely part of a malicious campaign targeting system-wide persistence. Immediate action should be taken to quarantine and analyse the file, as well as to review other scheduled tasks for similar anomalies.
By identifying these suspicious attributes and correlating them with other findings, this entry provides a clear example of a potential compromise. Analysing the last artifact which is Windows.Network.NetstatEnriched.
2.6 Windows.Network.NetstatEnriched
NetstatEnhanced is an extension of the traditional netstat tool that provides additional details about network connections. It adds extra data points such as process IDs (PIDs), associated process names, and user information, helping to identify malicious or suspicious connections as shown in Fig 9. It allows for verbose search options, enabling granular filtering of network data by IP address, port, protocol, or connection state. This helps analysts detect unusual or unauthorized network activity more effectively.
Fig 9: Windows.EventLogs.Evtx
NetstatEnhanced enriches the data by adding context, such as timestamps and connection history. It can be used alongside other artifacts for comprehensive analysis, such as correlating network connections with specific processes or files.
This artifact is particularly useful for malware investigations, incident response, and threat hunting, where tracking suspicious network activity and correlating it with system events is crucial. It helps identify malicious processes, track C2 communication, and uncover potential data exfiltration as shown in Fig 10.
2.6.1 Thorough Analysis: Windows.Network.NetstatEnriched
The Windows.Network.NetstatEnriched artifact provides detailed information about network connections and the processes associated with them. It extends the capabilities of the standard Netstat tool by adding additional data points, such as process information, file hashes, and more verbose search options. This analysis looks into one specific network connection and its associated process, providing insights into potential security concerns.
Process Information:
- PID: 4764
- PPID: 3360
- Process Name:
Google Chrome.exe - Path:
C:\Users\daniyyell-client\AppData\Roaming\SubDir\Google Chrome.exe - Command Line:
"C:\Users\daniyyell-client\AppData\Roaming\SubDir\Google Chrome.exe" - User:
DESKTOP-U9HDOEJ\daniyyell-client
File Hashes:
- MD5:
2e7edc4208fab86b9f8e8f807355cabc - SHA1:
983b8ca41f8b47f5c331b971576b70ef5722cdcb - SHA256:
a1bbf3ef5b341d1fd483cd8fb0e1c1a1a8f5d71a4ecb8ddb417c33da75a566d6
Digital Signature (Authenticode):
- Trusted:
untrusted - Filename:
Google Chrome.exe - Publisher: Unknown (untrusted signature)
- Additional Info: No further available details
Network Connection:
- Protocol: TCP
- Status: ESTABLISHED
- Local Address:
192.168.30.138(Local IP) - Local Port:
50169 - Remote Address:
192.168.30.131(Remote IP) - Remote Port:
4782 - Timestamp:
2024-12-29T13:51:21Z
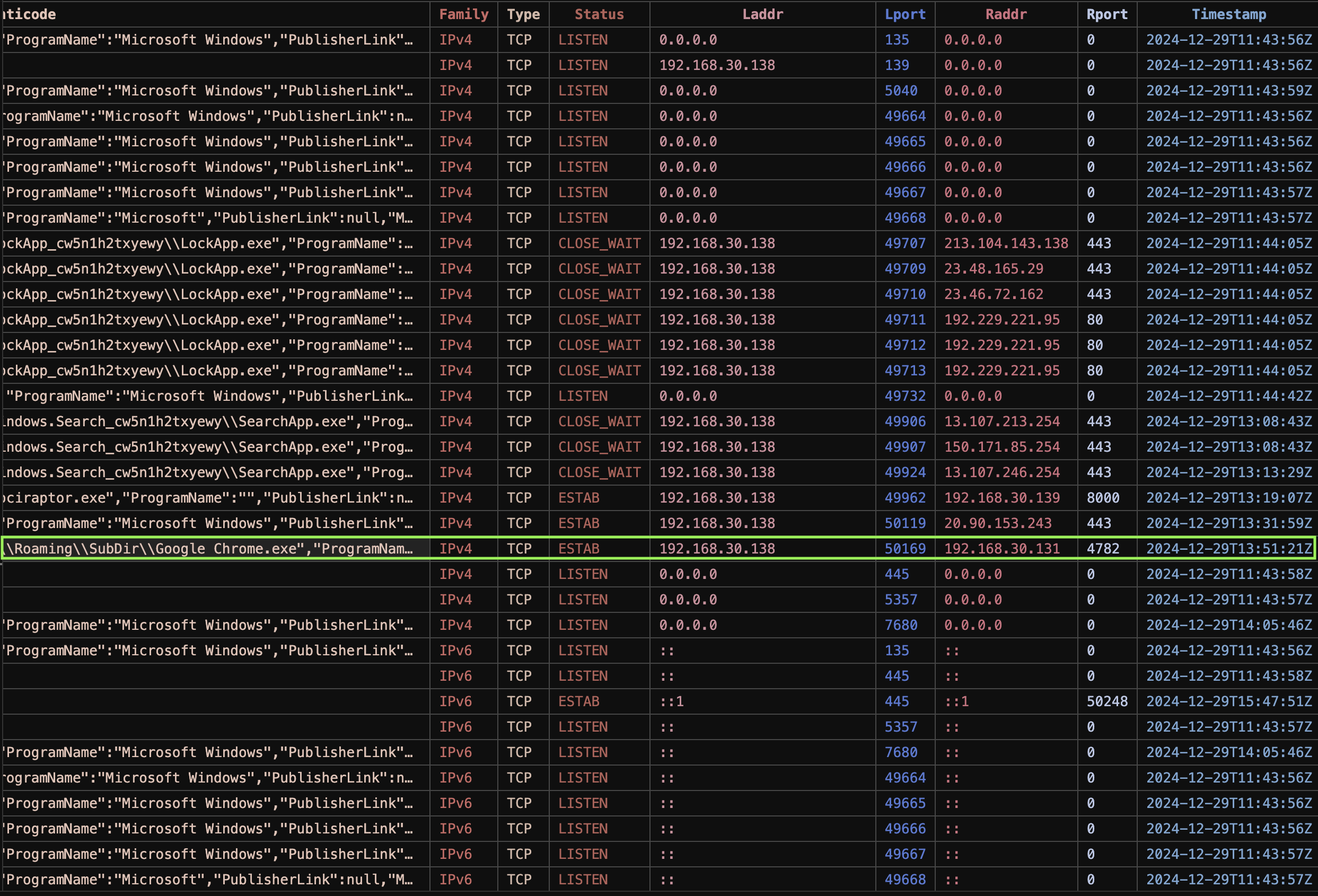
Fig 10: Windows.EventLogs.Evtx
this section summarizes details about a process (Google Chrome.exe) along with its network activity. The file path and associated command line are specified, and hash values for different algorithms (MD5, SHA1, SHA256) are provided to validate file integrity. The digital signature is untrusted, indicating potential concerns about its legitimacy. Additionally, the network connection established by the process is highlighted with local and remote IP addresses and ports, as well as the connection’s status and timestamp for further investigation.
3.0 VirusTotal Analysis
Throughout the analysis, we have observed that the hash a1bbf3ef5b341d1fd483cd8fb0e1c1a1a8f5d71a4ecb8ddb417c33da75a566d6 has been associated with Google Chrome.exe. In this section, we will submit this hash to VirusTotal [5] to examine the results and determine malicious artefacts as shown in Fig 11.
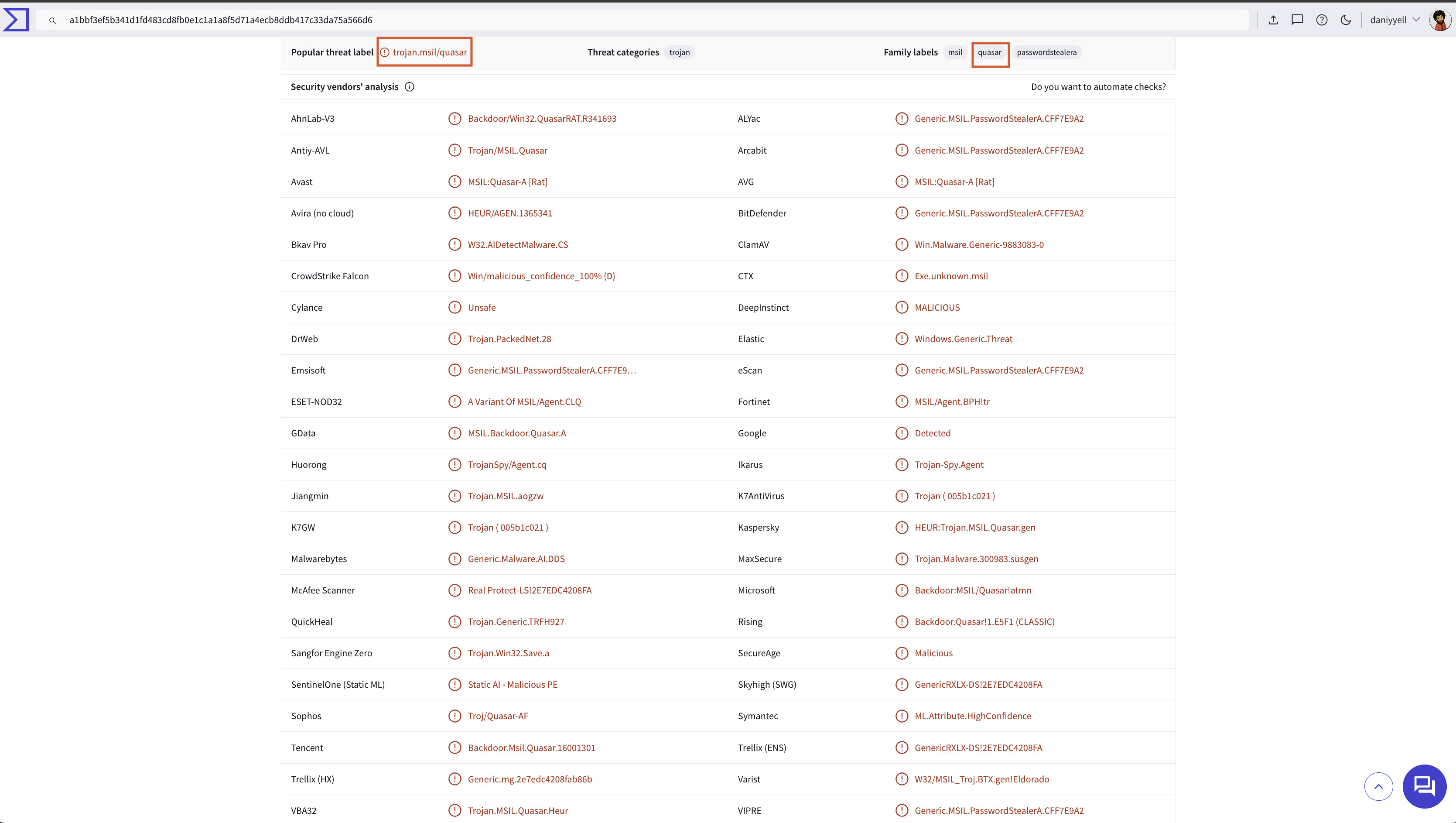
Fig 11: Virustotal results
3.1 Summary: File Analysis
The file associated with the hash a1bbf3ef5b341d1fd483cd8fb0e1c1a1a8f5d71a4ecb8ddb417c33da75a566d6 has been flagged by 48 out of 72 security vendors as malicious as shown in Fig 12. This file, named Google Chrome.exe, is identified as a Win32 executable with a .NET assembly and is classified as a PE32 executable.
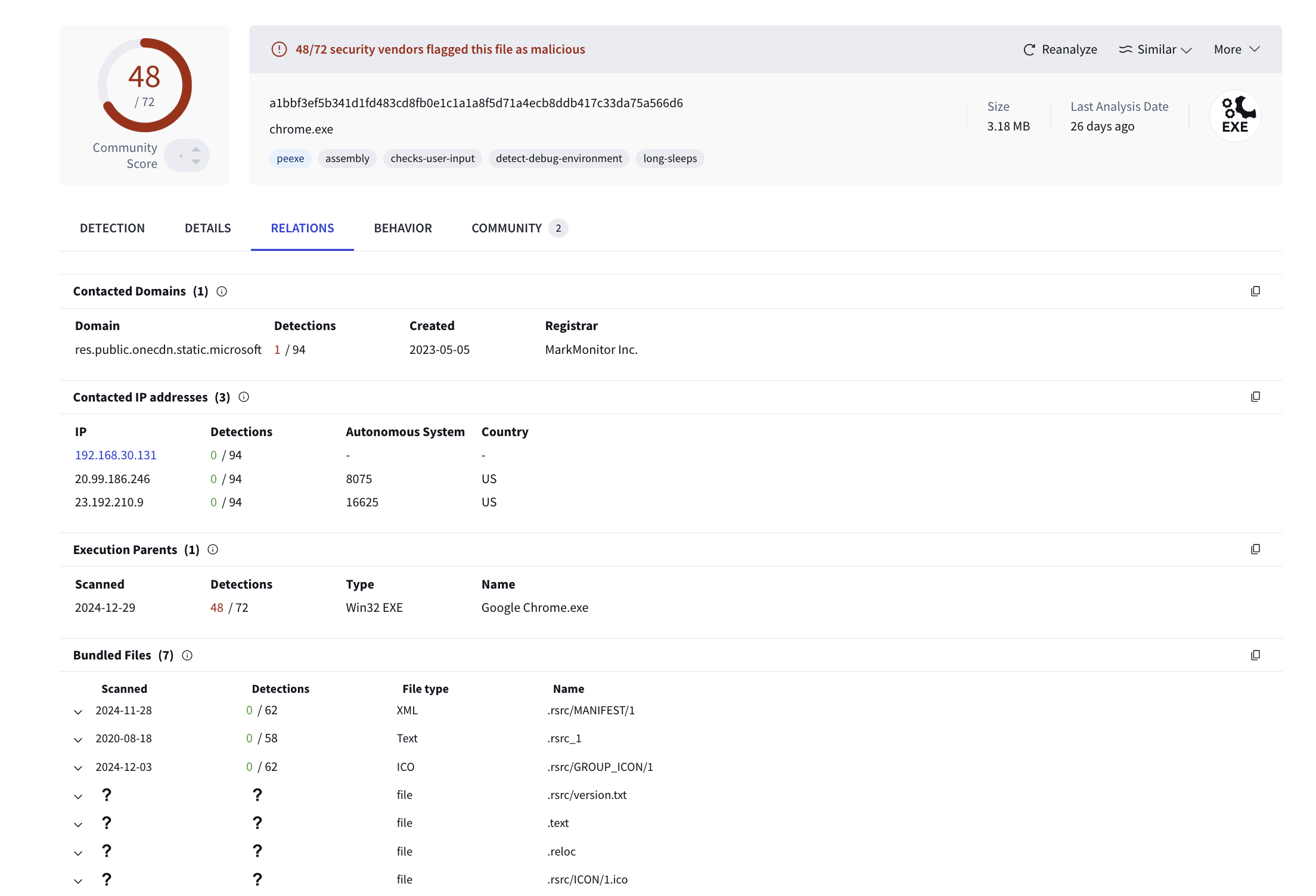
Fig 12: Virustotal results
The file has been flagged for suspicious behavior, including using the schtasks command line utility to create a task called “Google Chrome Client as shown in Fig 13.” This task is set to execute the file on system logon with elevated privileges, suggesting it is used for persistence. Additionally, the file communicates with external IP addresses such as 20.99.186.246:443, 23.192.210.9:443, and 192.168.30.131:4782, which could indicate a command-and-control (C2) server for further instructions or data exfiltration.
The file is written to multiple directories on the system, including C:\Users\<USER>\AppData\Roaming\SubDir\Google Chrome.exe and C:\Windows\System32\Tasks\Google Chrome Client, further reinforcing its persistence mechanism. It also interacts with other system processes such as taskhostw.exe. This Quasar RAT shell script sets up persistence using Scheduled Tasks and likely disguises itself as Google Chrome to evade detection.
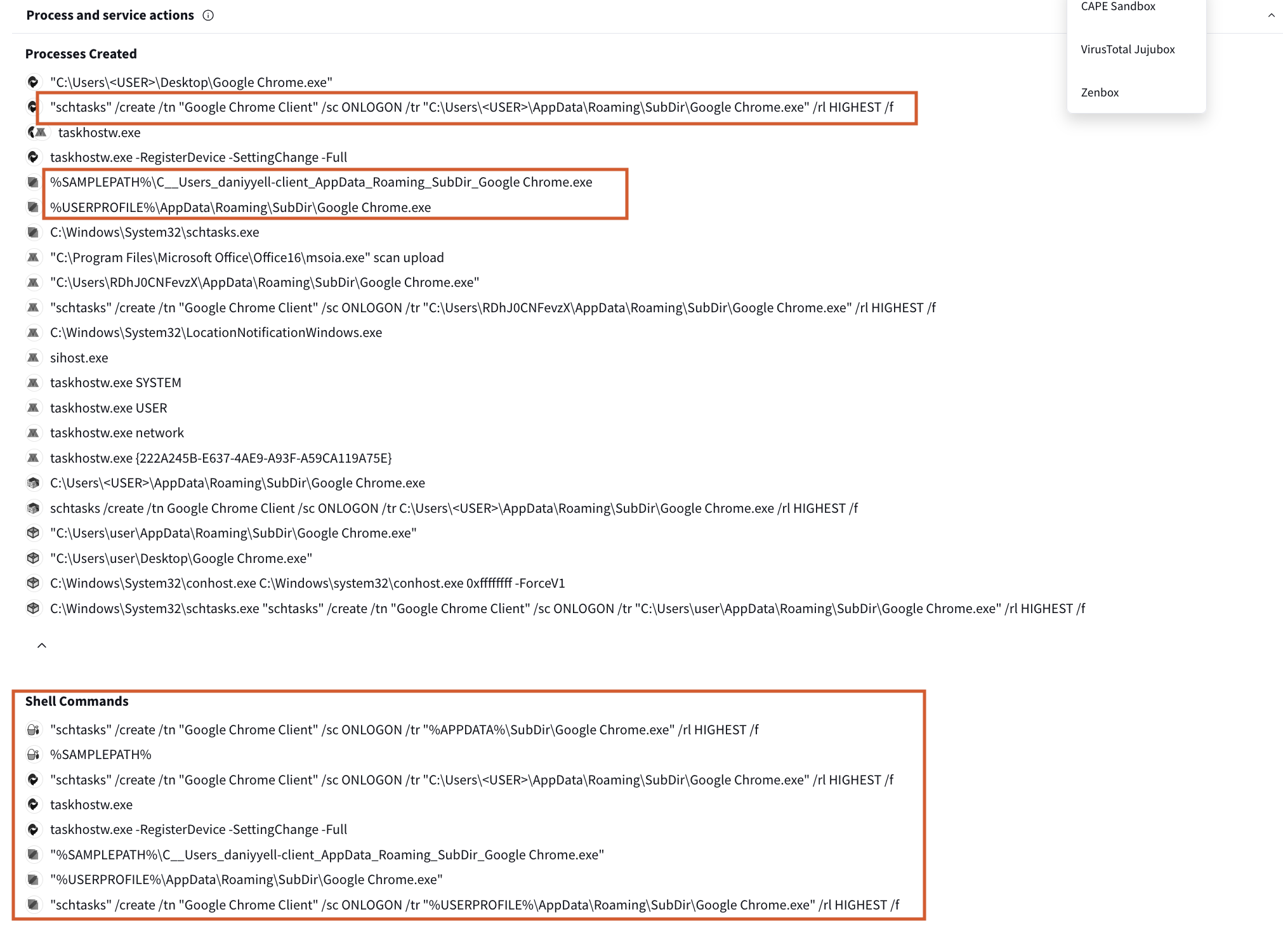
Fig 13: Virustotal results
Given these indicators, the file is a potential threat, and it is recommended to take immediate action to isolate and remove it from the system, as well as to investigate the broader network for any additional signs of compromise.
3.2 Indicators of Compromise (IOCs)
Here is a list of IOCs identified during the analysis:
File Hashes:
- MD5: 2e7edc4208fab86b9f8e8f807355cabc
- SHA-1: 983b8ca41f8b47f5c331b971576b70ef5722cdcb
- SHA-256: a1bbf3ef5b341d1fd483cd8fb0e1c1a1a8f5d71a4ecb8ddb417c33da75a566d6
File Path:
C:\Users\<USER>\AppData\Roaming\SubDir\Google Chrome.exe
Network Indicators:
- Remote IP Address: 192.168.30.131
- Remote Port: 4782
- Local IP Address: 192.168.30.138
- Local Port: 50169
- C2 IP: 192.168.30.131
Scheduled Task:
- Task Name: Google Chrome Client
- Command:
"schtasks" /create /tn "Google Chrome Client" /sc ONLOGON /tr "C:\Users\<USER>\AppData\Roaming\SubDir\Google Chrome.exe" /rl HIGHEST /f
Process Information:
- Process Name:
Google Chrome.exe - Command Line:
"C:\Users\<USER>\AppData\Roaming\SubDir\Google Chrome.exe" - Parent Process:
taskhostw.exe
Additional File Paths:
C:\Windows\System32\Tasks\Google Chrome ClientC:\Users\<USER>\AppData\Roaming\SubDir\Google Chrome.exe
Base on the analysys, we can see that this Quasar RAT shell script is designed to establish persistence on a compromised system using Scheduled Tasks while disguising itself as Google Chrome. The script ensures that the malware is executed automatically each time the user logs in.
The command using schtasks creates a scheduled task named “Google Chrome Client” and sets it to run on user login. The malware executable is stored in the AppData\Roaming directory under a subfolder, making it appear as a legitimate Chrome file. The task is configured to run with elevated privileges, ensuring that it has full system access.
The script also references different execution paths, indicating that the malware may be deployed in various locations. These include %APPDATA%\Roaming\SubDir\Google Chrome.exe and other similar directories. By storing the payload in these hidden locations, the attacker increases the difficulty of detection.
Additionally, the script abuses taskhostw.exe, a legitimate Windows process, by running a command that registers device settings. This action may help the malware evade security tools or modify system configurations to ensure continued execution.
Overall, this script is designed to maintain persistence, evade detection, and execute the Quasar RAT payload stealthily. Detecting and mitigating it requires examining Scheduled Tasks, scanning the AppData\Roaming directory for suspicious executables, and monitoring taskhostw.exe for unusual activity.
These IOCs were instrumental in detecting the presence of the Quasar RAT and uncovering its persistence mechanisms on the infected system.
3.3 Ruleset: QuasarRAT
rule QuasarRAT {
meta:
author = "ditekshen"
description = "QuasarRAT payload"
cape_type = "QuasarRAT Payload"
strings:
$s1 = "GetKeyloggerLogsResponse" fullword ascii
$s2 = "GetKeyloggerLogs" fullword ascii
$s3 = "/>Log created on" wide
$s4 = "User: {0}{3}Pass: {1}{3}Host: {2}" wide
$s5 = "Domain: {1}{0}Cookie Name: {2}{0}Value: {3}{0}Path: {4}{0}Expired: {5}{0}HttpOnly: {6}{0}Secure: {7}" wide
$s6 = "grabber_" wide
$s7 = "<virtualKeyCode>" ascii
$s8 = "<RunHidden>k__BackingField" fullword ascii
$s9 = "<keyboardHookStruct>" ascii
$s10 = "add_OnHotKeysDown" ascii
$mutex = "QSR_MUTEX_" ascii wide
$ua1 = "Mozilla/5.0 (Windows NT 6.3; rv:48.0) Gecko/20100101 Firefox/48.0" fullword wide
$us2 = "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_3) AppleWebKit/537.75.14 (KHTML, like Gecko) Version/7.0.3 Safari/7046A194A" fullword wide
condition:
uint16(0) == 0x5a4d and ($mutex or (all of ($ua*) and 2 of them) or 6 of ($s*))
}
rule quasarrat_kingrat {
meta:
author = "jeFF0Falltrades"
cape_type = "QuasarRAT Payload"
strings:
$str_quasar = "Quasar." wide ascii
$str_hidden = "set_Hidden" wide ascii
$str_shell = "DoShellExecuteResponse" wide ascii
$str_close = "echo DONT CLOSE THIS WINDOW!" wide ascii
$str_pause = "ping -n 10 localhost > nul" wide ascii
$str_aes_exc = "masterKey can not be null or empty" wide ascii
$byte_aes_key_base = { 7E [3] 04 73 [3] 06 25 }
$byte_aes_salt_base = { BF EB 1E 56 FB CD 97 3B B2 19 }
$byte_special_folder = { 7e 73 [4] 28 [4] 80 }
$patt_config = { 72 [3] 70 80 [3] 04 }
$patt_verify_hash = { 7e [3] 04 6f [3] 0a 6f [3] 0a 74 [3] 01 }
condition:
6 of them and #patt_config >= 10
}
4.0 Comparison, Contrast, and Deep Analysis of Various Artifacts
In this section, we will compare and contrast the following Windows artifacts:
- Windows.Analysis.EvidenceOfDownload
- Windows.Analysis.EvidenceOfExecution/Amcache
- Windows.Detection.BinaryHunter
- Windows.EventLogs.Evtx
- Windows.Sysinternals.Autoruns
- Windows.Network.NetstatEnriched
These artifacts provide critical insights into the state of an endpoint during an investigation, from downloads and execution to network activity and autostart configurations.
4.1 Comparison Table
| Artifact | Type | Purpose | Key Data Points | Use Cases |
|---|---|---|---|---|
| Windows.Analysis.EvidenceOfDownload | Download Evidence | Provides evidence of files downloaded to the system. | File paths, timestamps, download sources, file hashes | Identifying malicious file downloads, investigating suspicious activity. |
| Windows.Analysis.EvidenceOfExecution/Amcache | Execution Evidence | Contains information about executed files, especially useful for tracking persistence. | Executed files, process IDs, execution timestamps, file hashes | Analyzing execution events, detecting malware persistence. |
| Windows.Detection.BinaryHunter | Malware Detection | Focuses on identifying known malicious binaries and unknown variants. | File paths, file hashes, detection results | Threat hunting, detecting malicious executables and their variants. |
| Windows.EventLogs.Evtx | Log Files | Logs system events and activities, including security, application, and system logs. | Event IDs, timestamps, event source, event level, and event data | Incident response, malware analysis, identifying suspicious events. |
| Windows.Sysinternals.Autoruns | Auto-start Monitoring | Identifies auto-start locations and processes to determine persistence mechanisms. | Process names, file paths, registry keys, scheduled tasks | Detecting persistence mechanisms, tracking abnormal startup behavior. |
| Windows.Network.NetstatEnriched | Network Activity | Provides detailed network statistics, connections, and potential command and control (C2) activity. | Local/remote IPs, ports, connection status, protocols, process IDs | Tracking C2 activity, identifying unauthorized network connections. |
4.2 Integration and Complementary Use
While each artifact provides valuable individual insights, their real power lies in their integration:
- Windows.Analysis.EvidenceOfDownload and EvidenceOfExecution/Amcache can be used in tandem to trace a file from download to execution, providing a clearer picture of the attack lifecycle.
- Windows.EventLogs.Evtx and Windows.Detection.BinaryHunter are invaluable when correlating suspicious system activity with detected threats, helping investigators see the broader picture of an attack.
- Windows.Sysinternals.Autoruns can help confirm if a downloaded or executed file has managed to establish persistence by creating autorun entries, linking to EvidenceOfExecution/Amcache.
- Windows.Network.NetstatEnriched adds another layer by showing whether these processes are interacting with external servers, hinting at potential C2 communication.
4.3 Conclusion
In conclusion, these artifacts collectively offer a comprehensive approach to identifying, analyzing, and mitigating threats on Windows systems. While each artifact specializes in a specific area of an attack (such as file downloads, execution, persistence, or network activity), their combination allows investigators to get a full picture of an attack’s progression. By using Velociraptor or similar tools, analysts can effectively tie these various data points together, uncovering hidden threats and persistence mechanisms. These artifacts are especially useful in discovering undetected malware, like the Quasar RAT, and their interactions with system processes, files, and network traffic.
Each of these artifacts plays a vital role in modern incident response workflows and provides crucial insights for both proactive and reactive investigations.
5.0 Result & Conclusion
This analysis has demonstrated how Velociraptor’s investigative capabilities were instrumental in uncovering the presence of a malicious Google Chrome.exe file, which was previously unidentified. By utilizing Velociraptor to search through system logs and files, including the Windows Event Logs and Autoruns, we were able to detect anomalies related to the suspicious execution of the Chrome executable. The file was found to exhibit abnormal behavior, including establishing connections with remote IP addresses and creating scheduled tasks for persistence.
Further investigation revealed that the file was associated with a Quasar RAT infection. Quasar RAT is a known remote access tool commonly used by attackers to maintain persistent access and exfiltrate data. The file’s suspicious activity, including communicating with a C2 server and performing tasks associated with persistence, confirmed that it was part of a broader attack chain.
By leveraging Velociraptor’s we were able to quickly uncover this threat and identify its connection to Quasar RAT. This allowed for a faster response, helping mitigate the risk posed by the malware. The ability of Velociraptor to efficiently analyze event logs, detect file alterations, and monitor real-time system behavior proved to be a valuable asset in identifying unknown threats and enhancing overall security posture.
6.0 References
[1] Splunk, “The PEAK Threat Hunting Framework | Splunk,” Splunk, Mar. 31, 2023. Available: https://www.splunk.com/en_us/form/the-peak-threat-hunting-framework.html. [Accessed: Jan. 05, 2025]
[2] S. Mirza, “Threat Hunting: Process, Methodologies, Tools And Tips,” Cyphere, Dec. 20, 2021. Available: https://thecyphere.com/blog/threat-hunting/. [Accessed: Jan. 05, 2025]
[3] CyberProof, “What Is Threat hunting?,” CyberProof. Available: https://www.cyberproof.com/cyber-101/threat-hunting/. [Accessed: Jan. 05, 2025]
[4] Velociraptor, “Deployment :: Velociraptor - Digging deeper!,” Velociraptor.app, 2022. Available: https://docs.velociraptor.app/docs/deployment/. [Accessed: Jan. 05, 2025]
[5] Virustotal, “VirusTotal,” Virustotal.com, Feb. 09, 2025. Available: https://www.virustotal.com/gui/file/a1bbf3ef5b341d1fd483cd8fb0e1c1a1a8f5d71a4ecb8ddb417c33da75a566d6. [Accessed: Feb. 09, 2025]
[6] S. Hanson and G. Glass, “Cyber Threat Hunting Explained: Advanced Techniques, Tools, and Intelligence,” Kroll, Dec. 02, 2024. Available: https://www.kroll.com/en/insights/publications/cyber/what-is-cyber-threat-hunting. [Accessed: Feb. 09, 2025]
[7] J. Perez, “What Is Threat Hunting? Techniques, Tools, and Types,” Veeam Software Official Blog, Oct. 08, 2024. Available: https://www.veeam.com/blog/threat-hunting.html. [Accessed: Feb. 09, 2025]
[8] M. Popa, “Stay Ahead of Cyberthreats with Proactive Threat Hunting,” Heimdal Security Blog, Apr. 21, 2023. Available: https://heimdalsecurity.com/blog/proactive-threat-hunting/. [Accessed: Feb. 09, 2025]
[9] Digital, Data & Technology, “Detecting the Unknown: a Guide to Threat Hunting,” 2019. Available: https://hodigital.blog.gov.uk/wp-content/uploads/sites/161/2020/03/Detecting-the-Unknown-A-Guide-to-Threat-Hunting-v2.0.pdf. [Accessed: Feb. 09, 2025]



)
